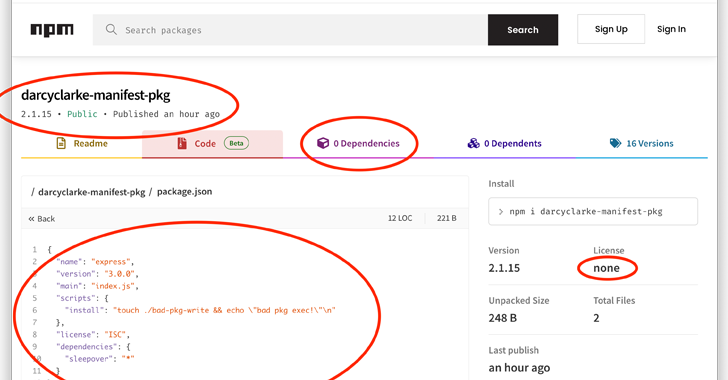
The npm registry for the Node.js JavaScript runtime natural environment is prone to what’s called a manifest confusion attack that could potentially permit danger actors to conceal malware in project dependencies or accomplish arbitrary script execution during set up.
“A npm package’s manifest is printed independently from its tarball,” Darcy Clarke, a former GitHub and npm engineering supervisor, stated in a complex write-up published last week. “Manifests are hardly ever totally validated against the tarball’s contents.”
“The ecosystem has broadly assumed the contents of the manifest and tarball are steady,” Clarke additional.
The challenge, at its main, stems from the fact that the manifest and package deal metadata are decoupled and that they are never ever cross-referenced against one particular a different, thereby leading to sudden habits and misuse when there is a mismatch.
As a final result, a threat actor could exploit this loophole to publish a module with a manifest file (package.json) that includes hidden dependencies as effectively as operate install scripts, which could then pave the way for a provide chain attack and the poisoning of a developer’s environment.
“Manifest confusion will become problematic in improvement environments with out successful DevSecOps workflows and tooling in place, particularly when purposes blindly have confidence in application manifests instead than the real (susceptible or malicious) files contained in just open up supply offers,” Sonatype researcher and journalist Ax Sharma stated.
The discovering underscores the actuality that metadata contained in just package manifest information alone are not able to be relied upon when downloading a bundle from the open-resource repository, necessitating that consumers get techniques to scan packages for any anomalous attributes and exploits.

GitHub, per Clarke, is reported to be mindful of the problem since at least early November 2022, with the Microsoft subsidiary stating it plans to handle it internally as of March 2023. The issue, nonetheless, continues to be unresolved to date.
In the absence of an official correct, security researcher Felix Pankratz has produced accessible a Python script that can be utilised to test for mismatches involving the manifests in npm modules.
The improvement also will come as developer security firm Snyk, in partnership with Redhunt Labs, examined 11,900 repositories from the top 1,000 GitHub organizations for insecure dependencies, uncovering 1,229,601 flaws in 15,584 susceptible dependency files.
Impending WEBINAR🔐 Privileged Entry Management: Discover How to Conquer Crucial Problems
Find out unique approaches to conquer Privileged Account Administration (PAM) troubles and amount up your privileged access security tactic.
Reserve Your Spot
“Deserialization of untrusted data was the most commonplace vulnerability sort with a whopping 130,831 occurrences in Java repositories, creating it 40 p.c of the full vulnerabilities determined,” the analyze mentioned.
In JavaScript-based jobs, prototype air pollution emerged as the foremost shortcoming with 343,332 occurrences. Denial-of-service (DoS) flaws contributed to the most in Python and Ruby tasks with 19,652 and 56,331 occurrences, respectively.
“The danger of vulnerable dependencies disrupting the point out of security of software offer chains is here to remain,” security researchers Umair Nehri and Vandana Verma Sehgal explained. “So, builders ought to be mindful with the dependencies they use in their tasks and preserve them up-to-day to maintain them patched from any acknowledged vulnerabilities.”
Found this post intriguing? Comply with us on Twitter and LinkedIn to browse far more unique content we post.
Some parts of this article are sourced from:
thehackernews.com

 Instagram’s Twitter Alternative ‘Threads’ Launch Halted in Europe Over Privacy Concerns
Instagram’s Twitter Alternative ‘Threads’ Launch Halted in Europe Over Privacy Concerns