A new Mirai-dependent botnet named NoaBot is being employed by risk actors as part of a crypto mining marketing campaign due to the fact the starting of 2023.
“The abilities of the new botnet, NoaBot, contain a wormable self-spreader and an SSH crucial backdoor to down load and execute extra binaries or spread itself to new victims,” Akamai security researcher Stiv Kupchik stated in a report shared with The Hacker Information.
Mirai, which had its supply code leaked in 2016, has been the progenitor of a number of botnets, the most modern getting InfectedSlurs, which is able of mounting distributed denial-of-services (DDoS) assaults.
There are indications that NoaBot could be linked to a different botnet marketing campaign involving a Rust-based mostly malware family known as P2PInfect, which not too long ago obtained an update to concentrate on routers and IoT equipment.

This is based on the point that menace actors have also experimented with dropping P2PInfect in position of NoaBot in new assaults focusing on SSH servers, indicating most likely tries to pivot to customized malware.
Despite NaoBot’s Mirai foundations, its spreader module leverages an SSH scanner to look for for servers susceptible to dictionary attack in get to brute-force them and include an SSH community critical in the .ssh/licensed_keys file for remote obtain. Optionally, it can also obtain and execute added binaries submit profitable exploitation or propagate itself to new victims.
“NoaBot is compiled with uClibc, which looks to improve how antivirus engines detect the malware,” Kupchik pointed out. “While other Mirai variants are generally detected with a Mirai signature, NoaBot’s antivirus signatures are of an SSH scanner or a generic trojan.”
In addition to incorporating obfuscation methods to render assessment difficult, the attack chain finally final results in the deployment of a modified variation of the XMRig coin miner.
What makes the new variant a slice previously mentioned other identical Mirai botnet-primarily based strategies is that it does not consist of any details about the mining pool or the wallet handle, therefore building it unattainable to evaluate the profitability of the illicit cryptocurrency mining plan.

“The miner obfuscates its configuration and also makes use of a tailor made mining pool to prevent exposing the wallet handle utilized by the miner,” Kupchik mentioned, highlighting some degree of preparedness of the menace actors.
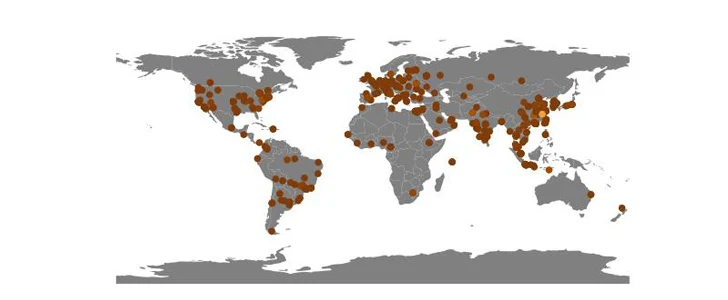
Akamai reported it discovered 849 target IP addresses to day that are distribute geographically across the world, with higher concentrations noted in China, so a great deal so that it quantities to pretty much 10% of all attacks versus its honeypots in 2023.
“The malware’s technique of lateral motion is via simple outdated SSH credentials dictionary assaults,” Kupchik stated. “Limiting arbitrary internet SSH obtain to your network tremendously diminishes the hazards of an infection. In addition, applying strong (not default or randomly generated) passwords also would make your network additional secure, as the malware works by using a basic record of guessable passwords.”
Discovered this short article appealing? Abide by us on Twitter and LinkedIn to read through more distinctive articles we publish.
Some parts of this article are sourced from:
thehackernews.com


 Getting off the Attack Surface Hamster Wheel: Identity Can Help
Getting off the Attack Surface Hamster Wheel: Identity Can Help