A new malware strain identified as ZenRAT has emerged in the wild that’s distributed by means of bogus installation deals of the Bitwarden password manager.
“The malware is precisely targeting Windows consumers and will redirect individuals making use of other hosts to a benign web page,” enterprise security organization Proofpoint said in a technological report. “The malware is a modular remote obtain trojan (RAT) with facts thieving abilities.”
ZenRAT is hosted on faux websites pretending to be associated with Bitwarden, although it truly is unsure as to how targeted traffic is remaining directed to the domains. These types of malware has been propagated through phishing, malvertising, or Search engine optimization poisoning assaults in the past.
The payload (Bitwarden-Installer-variation-2023-7-1.exe), downloaded from crazygameis[.]com, is a trojanized version of the regular Bitwarden installation bundle that is made up of a destructive .NET executable (ApplicationRuntimeMonitor.exe).
A noteworthy part of the campaign is that users who stop up traveling to the misleading website from non-Windows programs are redirected to a cloned opensource.com write-up revealed in March 2018 about “How to control your passwords with Bitwarden, a LastPass choice.”
More, Windows buyers clicking on downloading links marked for Linux or macOS on the Downloads website page are redirected to the genuine Bitwarden web-site, vault.bitwarden.com.
An analysis of the installer’s metadata reveals makes an attempt on the component of the danger actor to masquerade the malware as Piriform’s Speccy, a freeware Windows utility to present components and software package data.
The electronic signature utilized to sign the executable is not only invalid, but also promises to be signed by Tim Kosse, a effectively-identified German laptop scientist recognized for building the absolutely free cross-system FTP software package FileZilla.
ZenRAT, as soon as introduced, gathers details about the host, like CPU identify, GPU name, operating system variation, browser credentials, and put in apps and security computer software, to a command-and-command (C2) server (185.186.72[.]14) operated by the menace actors.
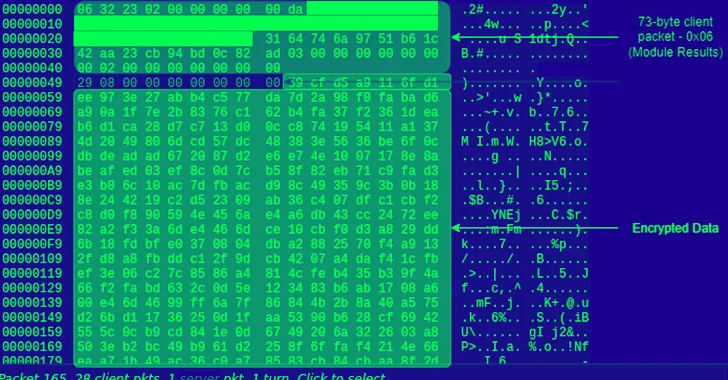
“The client initiates communication to the C2,” Proofpoint stated. “No matter of the command, and further data transmitted, the to start with packet is always 73 bytes.”
ZenRAT is also configured to transmit its logs to the server in plaintext, which captures a series of process checks carried out by the malware and the standing of the execution of every module, indicating its use as a “modular, extendable implant.”
To mitigate this kind of threats, it is really advised that people download software only from trustworthy resources and ensure the authenticity of the web sites.
The disclosure comes as the information and facts stealer identified as Lumma Stealer has been observed compromising manufacturing, retail, and organization industries considering the fact that the commencing of August 2023.
“The infostealer was delivered via generate-by downloads disguised as bogus installers these types of as Chrome and Edge browser installers, and some of them ended up distributed via PrivateLoader,” eSentire said earlier this month.
In a relevant marketing campaign, rogue web sites impersonating Google Enterprise Profile and Google Sheets were being located to trick buyers into installing a stealer malware dubbed Stealc under the pretext of a security update.
“Push-by downloads proceed to be a prevalent process to unfold malware, such as info stealers and loaders,” the Canadian cybersecurity firm mentioned.
Observed this post appealing? Follow us on Twitter and LinkedIn to read through more unique articles we write-up.
Some parts of this article are sourced from:
thehackernews.com

 New libwebp Vulnerability Under Active Exploitation – Gets Maximum CVSS Score
New libwebp Vulnerability Under Active Exploitation – Gets Maximum CVSS Score