An current edition of a botnet malware identified as Prometei has infected a lot more than 10,000 units throughout the world due to the fact November 2022.
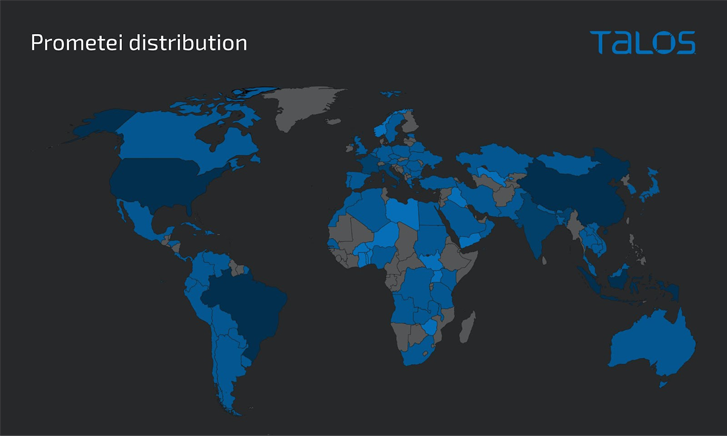
The bacterial infections are both geographically indiscriminate and opportunistic, with a the greater part of the victims noted in Brazil, Indonesia, and Turkey.
Prometei, very first observed in 2016, is a modular botnet that features a huge repertoire of factors and quite a few proliferation strategies, some of which also incorporate the exploitation of ProxyLogon Microsoft Exchange Server flaws.
It can be also notable for steering clear of placing Russia, suggesting that the menace actors driving the operation are probably based mostly in the region.
The cross-system botnet’s motivations are money, generally leveraging its pool of contaminated hosts to mine cryptocurrency and harvest credentials.
The most recent variant of Prometei (named v3) improves on its existing options to obstacle forensic analysis and additional burrow its obtain on sufferer devices, Cisco Talos mentioned in a report shared with The Hacker News.
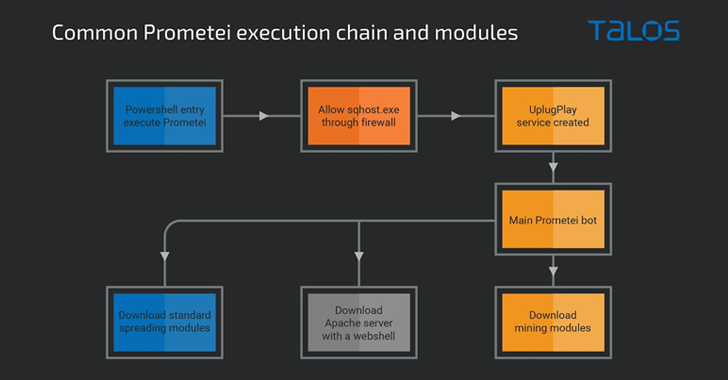
The attack sequence proceeds as a result: Upon attaining a profitable foothold, a PowerShell command is executed to download the botnet payload from a distant server. Prometei’s major module is then utilised to retrieve the real crypto-mining payload and other auxiliary parts on the program.
Some of these aid modules function as spreader applications intended to propagate the malware by means of Remote Desktop Protocol (RDP), Protected Shell (SSH), and Server Information Block (SMB).
WEBINARDiscover the Concealed Risks of 3rd-Occasion SaaS Applications
Are you conscious of the pitfalls affiliated with 3rd-get together app accessibility to your firm’s SaaS applications? Be part of our webinar to study about the varieties of permissions becoming granted and how to lessen risk.
RESERVE YOUR SEAT
Prometei v3 is also noteworthy for utilizing a area technology algorithm (DGA) to create out its command-and-regulate (C2) infrastructure. It more packs in a self-update mechanism and an expanded set of commands to harvest sensitive info and commandeer the host.
Very last but not minimum, the malware deploys an Apache web server that’s bundled with a PHP-based mostly web shell, which is capable of executing Foundation64-encoded instructions and carrying out file uploads.
“This latest addition of new capabilities [indicates] that the Prometei operators are consistently updating the botnet and adding functionality,” Talos scientists Andrew Windsor and Vanja Svajcer reported.
Identified this short article exciting? Observe us on Twitter and LinkedIn to examine more distinctive material we article.
Some parts of this article are sourced from:
thehackernews.com

 China-linked Hackers Targeting Unpatched SonicWall SMA Devices with Malware
China-linked Hackers Targeting Unpatched SonicWall SMA Devices with Malware