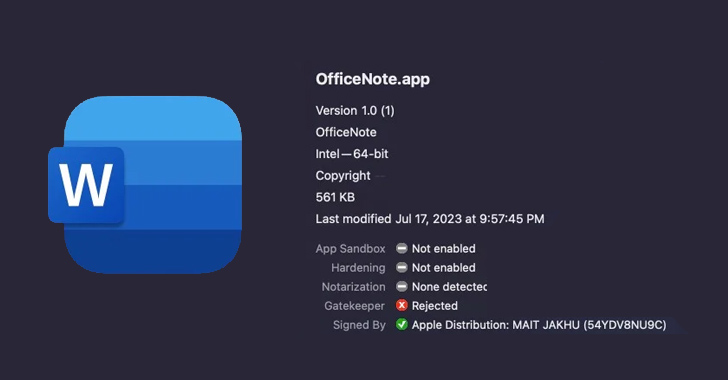
A new variant of an Apple macOS malware referred to as XLoader has surfaced in the wild, masquerading its destructive functions underneath the guise of an business efficiency application known as “OfficeNote.”
“The new edition of XLoader is bundled within a regular Apple disk impression with the identify OfficeNote.dmg,” SentinelOne security researchers Dinesh Devadoss and Phil Stokes reported in a Monday evaluation. “The software contained in is signed with the developer signature MAIT JAKHU (54YDV8NU9C).”
XLoader, first detected in 2020, is regarded a successor to Formbook and is an data stealer and keylogger available underneath the malware-as-a-company (MaaS) model. A macOS variant of the malware emerged in July 2021, dispersed as a Java program in the kind of a compiled .JAR file.

“Such documents involve the Java Runtime Surroundings, and for that explanation the destructive .jar file will not execute on a macOS put in out of the box, due to the fact Apple stopped delivery JRE with Macs above a ten years back,” the cybersecurity firm observed at the time.
The latest iteration of XLoader will get around this limitation by switching to programming languages such as C and Aim C, with the disk impression file signed on July 17, 2023. Apple has because revoked the signature.
SentinelOne said it detected several submissions of the artifact on VirusTotal all via the month of July 2023, indicating a widespread marketing campaign.
“Ads on crimeware discussion boards offer you the Mac version for rental at $199/thirty day period or $299/3 months,” the scientists reported. “Interestingly, this is somewhat expensive when compared to Windows variants of XLoader, which go for $59/thirty day period and $129/3 months.”
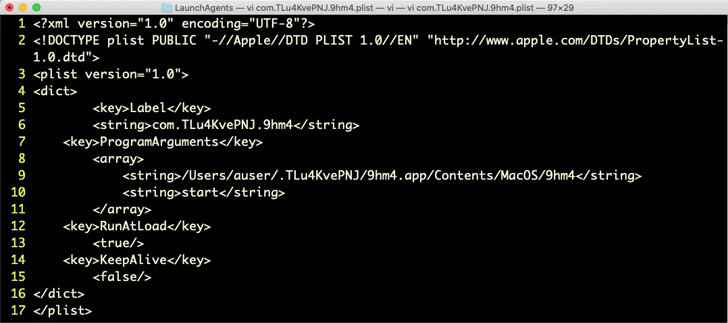
As soon as executed, OfficeNote throws an mistake concept indicating it “won’t be able to be opened mainly because the initial product can’t be found,” but, in truth, it installs a Start Agent in the qualifications for persistence.

XLoader is created to harvest clipboard details as nicely as information and facts stored in the directories linked with web browsers these kinds of as Google Chrome and Mozilla Firefox. Safari, even so, is not focused.
Other than getting measures to evade assessment equally manually and by automatic solutions, the malware is configured to run sleep instructions to hold off its execution and avoid raising any red flags.
“XLoader carries on to present a menace to macOS people and firms,” the scientists concluded.
“This latest iteration masquerading as an office environment productivity application shows that the targets of fascination are plainly customers in a doing work atmosphere. The malware attempts to steal browser and clipboard secrets and techniques that could be made use of or offered to other menace actors for even further compromise.”
Identified this short article attention-grabbing? Comply with us on Twitter and LinkedIn to read through more unique content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Ivanti Warns of Critical Zero-Day Flaw Being Actively Exploited in Sentry Software
Ivanti Warns of Critical Zero-Day Flaw Being Actively Exploited in Sentry Software