Security scientists have thorough a new variant of a dynamic url library (DLL) research get hijacking strategy that could be utilized by danger actors to bypass security mechanisms and accomplish execution of destructive code on programs jogging Microsoft Windows 10 and Windows 11.
The tactic “leverages executables generally found in the trusted WinSxS folder and exploits them through the traditional DLL lookup order hijacking system,” cybersecurity organization Security Joes mentioned in a new report solely shared with The Hacker Information.
In undertaking so, it allows adversaries to do away with the will need for elevated privileges when attempting to operate nefarious code on a compromised machine as well as introduce probably susceptible binaries into the attack chain, as noticed in the earlier.
DLL look for buy hijacking, as the title implies, consists of gaming the look for buy utilized to load DLLs in purchase to execute malicious payloads for uses of protection evasion, persistence, and privilege escalation.

Specifically, assaults exploiting the strategy single out apps that do not specify the complete route to the libraries they require, and in its place, rely on a predefined look for get to identify the required DLLs on disk.
Menace actors consider advantage of this habits by moving reputable system binaries into non-normal directories that incorporate destructive DLLs that are named soon after respectable types so that the library made up of the attack code is picked up in position of the latter.
This, in transform, will work because the method contacting the DLL will lookup in the listing it really is executing from initially ahead of recursively iterating by means of other spots in a unique purchase to locate and load the source in problem. To put it in other phrases, the research purchase is as follows –
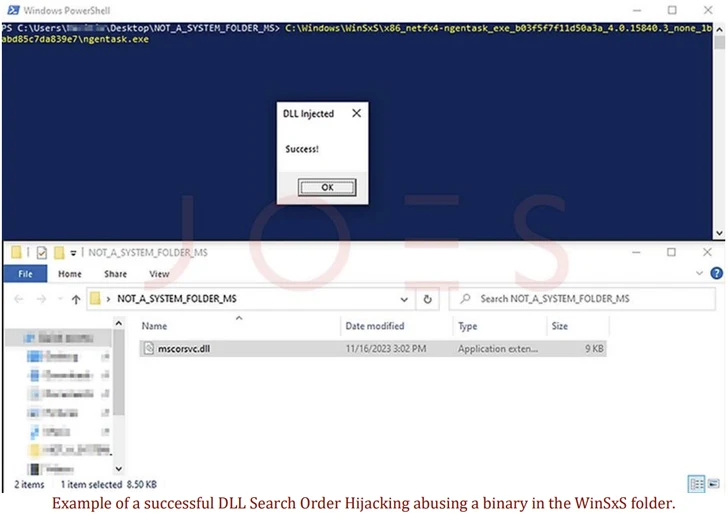
The novel twist devised by Security Joes targets information found in the reliable “C:WindowsWinSxS” folder. Quick for Windows facet-by-aspect, WinSxS is a critical Windows element that’s made use of for the customization and updating of the functioning system to make sure compatibility and integrity.

“This solution represents a novel software in cybersecurity: traditionally, attackers have mostly relied on properly-identified techniques like DLL lookup buy hijacking, a approach that manipulates how Windows purposes load exterior libraries and executables,” Ido Naor, co-founder and CEO of Security Joes, stated in a assertion shared with The Hacker News.
“Our discovery diverges from this path, unveiling a more delicate and stealthy approach of exploitation.”
The thought, in a nutshell, is to locate susceptible binaries in the WinSxS folder (e.g., ngentask.exe and aspnet_wp.exe) and merge it with the standard DLL search order hijacking methods by strategically putting a tailor made DLL with the similar name as the authentic DLL into an actor-controlled directory to achieve code execution.
As a outcome, merely executing a vulnerable file in the WinSxS folder by placing the custom made folder that contains the rogue DLL as the present-day listing is more than enough to set off the execution of the DLL’s contents devoid of owning to duplicate the executable from the WinSxS folder to it.
Security Joes warned that there could be added binaries in the WinSxS folder that are inclined to this kind of DLL lookup get hijacking, necessitating that businesses take enough safety measures to mitigate the exploitation approach in their environments.
“Analyze dad or mum-little one relationships between procedures, with a precise concentrate on reliable binaries,” the business explained. “Keep an eye on closely all the pursuits performed by the binaries residing in the WinSxS folder, focusing on each network communications and file functions.”
Uncovered this post attention-grabbing? Stick to us on Twitter and LinkedIn to read through much more exceptional content we article.
Some parts of this article are sourced from:
thehackernews.com


 New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security
New Terrapin Flaw Could Let Attackers Downgrade SSH Protocol Security