A earlier undocumented threat actor has been linked to a cyber attack targeting an aerospace firm in the U.S. as component of what is actually suspected to be a cyber espionage mission.
The BlackBerry Menace Exploration and Intelligence workforce is monitoring the exercise cluster as AeroBlade. Its origin is presently unknown and it can be not very clear if the attack was thriving.
“The actor employed spear-phishing as a shipping mechanism: A weaponized document, despatched as an email attachment, is made up of an embedded remote template injection strategy and a destructive VBA macro code, to supply the up coming stage to the ultimate payload execution,” the corporation claimed in an assessment revealed past week.
Impending WEBINAR Understand Insider Menace Detection with Application Reaction Methods
Discover how application detection, response, and automatic behavior modeling can revolutionize your protection towards insider threats.
Be a part of Now
The network infrastructure made use of for the attack is said to have long gone dwell all-around September 2022, with the offensive section of the intrusion developing just about a calendar year afterwards in July 2023, but not just before the adversary took methods to improvise its toolset to make it far more stealthy in the intervening time time period.
The initial attack, which took position in September 2022, commenced with a phishing email bearing a Microsoft Term attachment that, when opened, utilised a approach called remote template injection to retrieve a following-phase payload that’s executed after the victim permits macros.
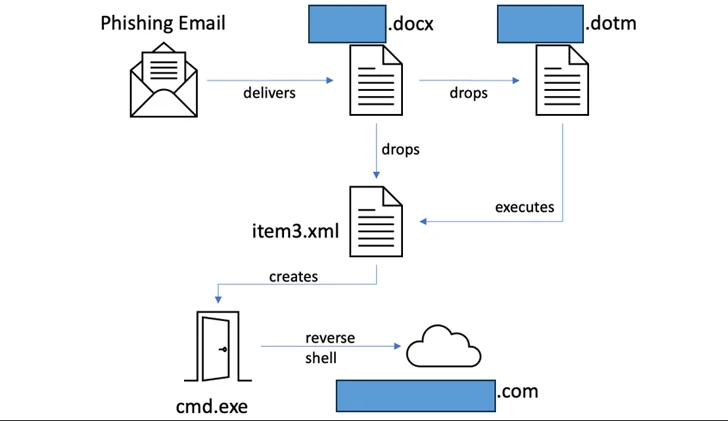
The attack chain finally led to the deployment of a dynamic-link library (DLL) that functions as a reverse shell, connecting to a tricky-coded command-and-control (C2) server and transmitting process data to the attackers.
The information accumulating abilities also consist of enumerating the total checklist of directories on the contaminated host, indicating that this could be a reconnaissance effort and hard work carried out to see if the equipment hosts any important data and help its operators in strategizing their following ways.

“Reverse shells enable attackers to open ports to the focus on devices, forcing communication and enabling a entire takeover of the product,” Dmitry Bestuzhev, senior director of cyber danger intelligence at BlackBerry, reported. “It is consequently a significant security menace.”
The greatly obfuscated DLL also will come equipped with anti-assessment and anti-disassembly tactics to make it demanding to detect and get apart, even though also skipping execution on sandboxed environments. Persistence is completed by usually means of a Endeavor Scheduler, in which a job named “WinUpdate2” is created to run each and every day at 10:10 a.m.
“In the course of the time that elapsed among the two campaigns we observed, the risk actor place substantial exertion into producing supplemental sources to assure they could protected entry to the sought-immediately after information and facts, and that they could exfiltrate it efficiently,” Bestuzhev reported.
Uncovered this article interesting? Follow us on Twitter and LinkedIn to read much more distinctive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Microsoft Warns of Kremlin-Backed APT28 Exploiting Critical Outlook Vulnerability
Microsoft Warns of Kremlin-Backed APT28 Exploiting Critical Outlook Vulnerability