A formerly not known Linux remote accessibility trojan called Krasue has been noticed focusing on telecom corporations in Thailand by danger actors to key covert accessibility to target networks at lease given that 2021.
Named soon after a nocturnal feminine spirit of Southeast Asian folklore, the malware is “capable to conceal its very own existence throughout the initialization period,” Team-IB reported in a report shared with The Hacker News.
The precise preliminary access vector applied to deploy Krasue is at the moment not acknowledged, although it truly is suspected that it could be via vulnerability exploitation, credential brute-drive assaults, or downloaded as section of a bogus application package deal or binary. The scale of the campaign is
Upcoming WEBINAR Cracking the Code: Master How Cyber Attackers Exploit Human Psychology
At any time wondered why social engineering is so effective? Dive deep into the psychology of cyber attackers in our upcoming webinar.
Be part of Now
The malware’s core functionalities are recognized by way of a rootkit that makes it possible for it to maintain persistence on the host without having attracting any consideration. The rootkit is derived from open up-supply projects such as Diamorphine, Suterusu, and Rooty.
This has lifted the possibility that Krasue is possibly deployed as component of a botnet or bought by original entry brokers to other cybercriminals, these as ransomware affiliate marketers, who are looking to attain accessibility to a particular focus on.
“The rootkit can hook the `kill()` syscall, network-linked features, and file listing functions in order to hide its pursuits and evade detection,” Group-IB malware analyst Sharmine Minimal reported.
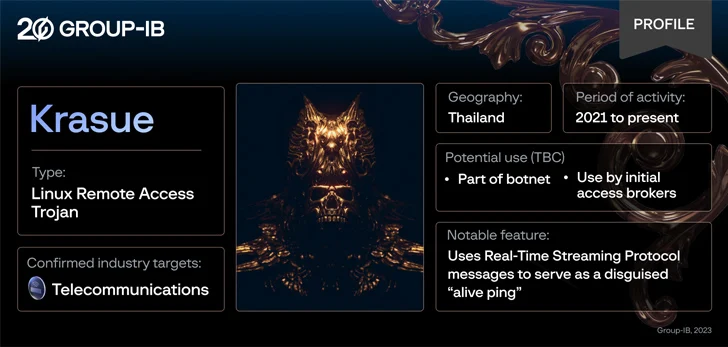
“Notably, Krasue makes use of RTSP (Serious Time Streaming Protocol) messages to serve as a disguised ‘alive ping,’ a tactic almost never noticed in the wild.”
The trojan’s command-and-command (C2) communications further let it to designate a speaking IP as its learn upstream C2 server, get facts about the malware, and even terminate by itself.

Krasue also shares quite a few resource code similarities with an additional Linux malware named XorDdos, indicating that it has been made by the identical creator as the latter, or by actors who had obtain to its supply code.
“The data available is not sufficient to put ahead a conclusive attribution as to the creator of Krasue, or the groups that are leveraging it in the wild, but the actuality that these malicious courses are ready to continue to be less than the radar for extended intervals can make it clear that continual vigilance and improved security measures are necessary,” Small mentioned.
Found this write-up exciting? Observe us on Twitter and LinkedIn to read far more exceptional written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Meta Launches Default End-to-End Encryption for Chats and Calls on Messenger
Meta Launches Default End-to-End Encryption for Chats and Calls on Messenger