A new Rust-based mostly info stealer malware known as Fickle Stealer has been observed remaining shipped via a number of attack chains with the target of harvesting sensitive info from compromised hosts.
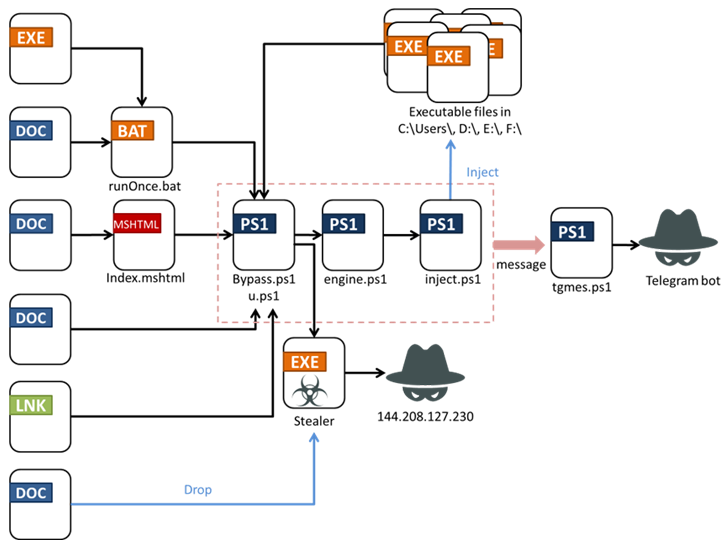
Fortinet FortiGuard Labs reported it’s mindful of four different distribution procedures — namely VBA dropper, VBA downloader, hyperlink downloader, and executable downloader — with some of them working with a PowerShell script to bypass User Account Handle (UAC) and execute Fickle Stealer.
The PowerShell script (“bypass.ps1” or “u.ps1”) is also developed to periodically send out facts about the sufferer, together with place, city, IP address, running process version, computer title, and username to a Telegram bot controlled by the attacker.

The stealer payload, which is protected applying a packer, runs a collection of anti-analysis checks to decide if it truly is running in a sandbox or a virtual equipment natural environment, following which it beacons out to a remote server to exfiltrate information in the form of JSON strings.
Fickle Stealer is no various from other variants in that it’s developed to assemble facts from crypto wallets, web browsers driven by Chromium and the Gecko browser motor (i.e, Google Chrome, Microsoft Edge, Courageous, Vivaldi, and Mozilla Firefox), and apps like AnyDesk, Discord, FileZilla, Sign, Skype, Steam, and Telegram.
It can be also made to export files matching the extensions .txt, .kdbx, .pdf, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .odt, .odp, and wallet.dat.
“In addition to some well-liked purposes, this stealer lookups sensitive data files in mother or father directories of popular set up directories to be certain thorough information accumulating,” security researcher Pei Han Liao explained. “It also receives a focus on checklist from the server, which tends to make Fickle Stealer extra versatile.”
The disclosure arrives as Symantec disclosed aspects of an open up-resource Python stealer termed AZStealer that will come with the performance to steal a vast wide range of information. Out there on GitHub, it has been advertised as the “most effective undetected Discord stealer.”

“All stolen facts is zipped and depending on the measurement of the archive exfiltrated straight as a result of Discord webhooks or very first uploaded to Gofile on line data files storage and just after that exfiltrated by way of Discord,” the Broadcom-owned organization stated.
“AZStealer will also endeavor the theft of doc documents with predefined targeted extensions or individuals owning precise key phrases this sort of as password, wallet, backup, and many others. in the filename.”
Identified this write-up attention-grabbing? Follow us on Twitter and LinkedIn to read through far more distinctive content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Experts Uncover New Evasive SquidLoader Malware Targeting Chinese Organizations
Experts Uncover New Evasive SquidLoader Malware Targeting Chinese Organizations