North Korean state-sponsored risk actors have been attributed to a cyber espionage campaign targeting the protection sector across the environment.
In a joint advisory published by Germany’s Federal Office for the Defense of the Structure (BfV) and South Korea’s Countrywide Intelligence Provider (NIS), the organizations said the target of the attacks is to plunder innovative protection systems in a “value-effective” manner.
“The regime is applying the navy technologies to modernize and boost the general performance of regular weapons and to produce new strategic weapon methods like ballistic missiles, reconnaissance satellites and submarines,” they noted.
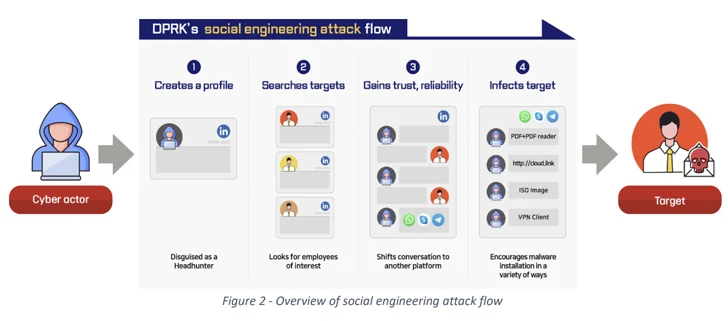
The infamous Lazarus Team has been blamed for 1 of the two hacking incidents, which included the use of social engineering to infiltrate the defense sector as aspect of a extended-standing operation termed Desire Occupation. The campaign has been ongoing considering that August 2020 about many waves.
In these attacks, the threat actors either build a fake profile or leverage legitimate-but-compromised profiles on platforms like LinkedIn to method potential targets and build have confidence in with them, in advance of giving valuable work alternatives and shifting the dialogue to a diverse messaging provider like WhatsApp to initiate the recruitment process.

Victims are then despatched coding assignments and career offer you documents laden with malware that, when launched, activate the infection process to compromise their desktops.
“Universally, the circumstance that workforce normally do not converse to their colleagues or employer about occupation offers plays into the hands of the attacker,” the organizations explained.
“The Lazarus Group altered its resources all through the marketing campaign and shown more than when that it is capable of creating regardless of what is vital to go well with the predicament.”
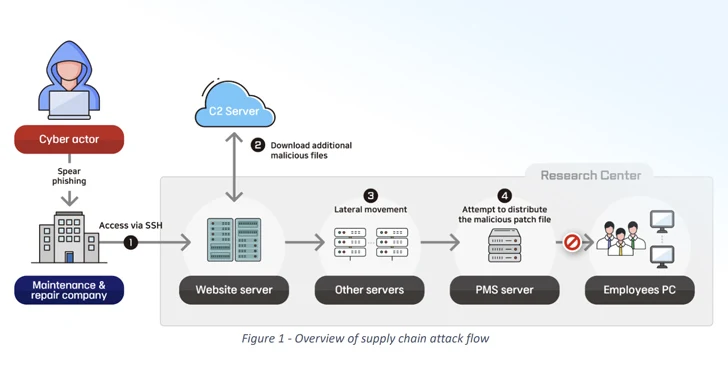
The 2nd circumstance issues an intrusion into a protection investigation center in direction of the conclusion of 2022 by executing a application supply chain attack versus an unnamed enterprise accountable for preserving just one of the investigate center’s web servers.
“The cyber actor further more infiltrated the investigation facility by deploying remote-control malware as a result of a patch administration system (PMS) of the investigate centre, and stole various account information of enterprise portals and email contents,” the BfV and NIS explained.
The breach, which was carried by an additional North Korea-dependent risk actor, unfolded over 5 levels –
- Hack into the web server routine maintenance organization, steal SSH qualifications, and achieve remote obtain to the investigation center’s server
- Obtain more destructive tooling making use of curl commands, like a tunneling program and a Python-based mostly downloader
- Carry out lateral motion and plunder employee account qualifications
- Leverage the stolen security manager’s account details to unsuccessfully distribute a trojanized update that comes with capabilities to add and down load files, execute code, and to gather method information
- Persist inside of target surroundings by weaponizing a file add vulnerability in the internet site to deploy a web shell for remote access and ship spear-phishing email messages
“The actor avoided carrying out a immediate attack from its focus on, which managed a higher degree of security, but relatively produced an original attack in opposition to its vendor, the upkeep and restore enterprise,” the companies discussed. “This suggests that the actor took gain of the trustful romantic relationship among the two entities.”

The security bulletin is the second to be revealed by BfV and NIS in as a lot of yrs. In March 2023, the companies warned of Kimsuky actors utilizing rogue browser extensions to steal users’ Gmail inboxes. Kimsuky was sanctioned by the U.S. authorities in November 2023.
The advancement comes as blockchain analytics firm Chainalysis exposed that the Lazarus Team has switched to applying YoMix bitcoin mixer to launder stolen proceeds following the shutdown of Sinbad late past calendar year, indicating their capacity to adapt their modus operandi in reaction to legislation enforcement actions.
“Sinbad turned a most popular mixer for North Korea-affiliated hackers in 2022, before long soon after the sanctioning of Twister Cash, which experienced previously been the go-to for these complex cybercriminals,” the corporation explained. “With Sinbad out of the photo, Bitcoin-dependent mixer YoMix has acted as a replacement.”
The malicious routines are the work of a plethora of North Korean hacking units functioning below the broad Lazarus umbrella, which are regarded to have interaction in an array of hacking operations ranging from cyber espionage to cryptocurrency thefts, ransomware, and offer chain attacks to realize their strategic objectives.
Observed this write-up exciting? Adhere to us on Twitter and LinkedIn to browse much more exclusive information we post.
Some parts of this article are sourced from:
thehackernews.com

 Critical Flaws Found in ConnectWise ScreenConnect Software – Patch Now
Critical Flaws Found in ConnectWise ScreenConnect Software – Patch Now