A new ransomware group known as RA Group has grow to be the most current menace actor to leverage the leaked Babuk ransomware source code to spawn its personal locker variant.
The cybercriminal gang, which is mentioned to have been working because at the very least April 22, 2023, is promptly growing its functions, according to cybersecurity firm Cisco Talos.
“To day, the team has compromised 3 organizations in the U.S. and one particular in South Korea across numerous enterprise verticals, like producing, prosperity management, insurance coverage companies and prescribed drugs,” security researcher Chetan Raghuprasad mentioned in a report shared with The Hacker News.
RA Team is no different from other ransomware gangs in that it launches double extortion assaults and operates a date leak web page to utilize supplemental stress on victims into spending ransoms.

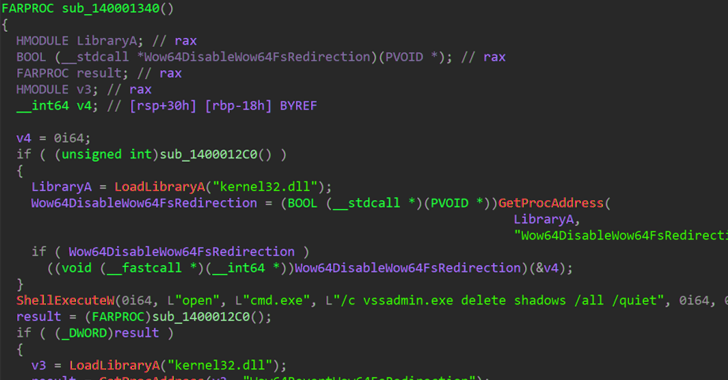
The Windows-centered binary employs intermittent encryption to velocity up the system and evade detection, not to point out delete quantity shadow copies and contents of the machine’s Recycle Bin.
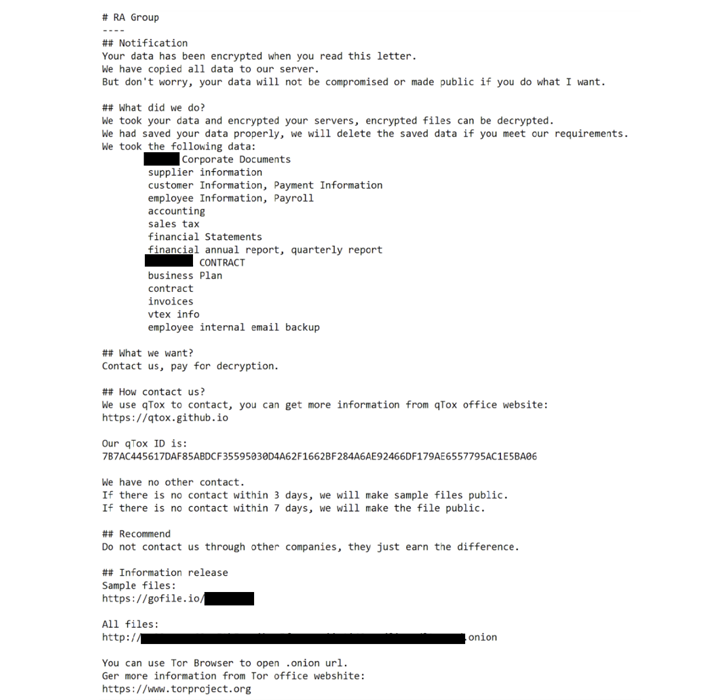
“RA Team employs custom-made ransom notes, which includes the victim’s name and a distinctive backlink to obtain the exfiltration proofs,” Raghuprasad stated. “If the sufferer fails to get in touch with the actors in just a few days, the group leaks the victim’s files.”
It also can take ways to avoid encrypting program information and folders by implies of a challenging-coded listing so that it enables the victims to down load the qTox chat software and achieve out to the operators making use of the qTox ID furnished on the ransom take note.
The advancement will come a lot less than a week immediately after SentinelOne disclosed that threat actors of various sophistication and know-how are progressively adopting the Babuk ransomware code to create a dozen variants that are able of targeting Linux devices.
“There is a obvious pattern that actors ever more use the Babuk builder to produce ESXi and Linux ransomware,” the cybersecurity firm said. “This is particularly evident when utilized by actors with much less sources, as these actors are less most likely to noticeably modify the Babuk resource code.”
Forthcoming WEBINARLearn to Quit Ransomware with Genuine-Time Protection
Sign up for our webinar and discover how to end ransomware attacks in their tracks with serious-time MFA and assistance account defense.
Help save My Seat!
Other ransomware actors that have adopted the Babuk source code more than the earlier yr include AstraLocker and Nokoyawa. Cheerscrypt, an additional ransomware pressure based mostly on Babuk, has been connected to a Chinese espionage actor called Emperor Dragonfly which is recognized for functioning short-lived ransomware strategies these types of as Rook, Evening Sky, and Pandora.
The conclusions also stick to the discovery of two other new ransomware strains codenamed Rancoz and BlackSuit, the latter of which is made to goal equally Windows and VMware ESXi servers.
“The continuous evolution and launch of new ransomware variants emphasize the sophisticated competencies and agility of [threat actors], indicating that they are responding to cybersecurity measures and checks being implemented and customizing their ransomware accordingly,” Cyble said.
Found this posting exciting? Stick to us on Twitter and LinkedIn to go through additional unique written content we post.
Some parts of this article are sourced from:
thehackernews.com

 Why High Tech Companies Struggle with SaaS Security
Why High Tech Companies Struggle with SaaS Security