An updated edition of an info-thieving malware termed Rhadamanthys is getting applied in phishing campaigns concentrating on the oil and gasoline sector.
“The phishing e-mail use a exceptional vehicle incident lure and, in afterwards levels of the infection chain, spoof the Federal Bureau of Transportation in a PDF that mentions a sizeable fantastic for the incident,” Cofense researcher Dylan Duncan claimed.
The email message arrives with a malicious connection that leverages an open up redirect flaw to acquire the recipients to a backlink hosting a intended PDF doc, but, in reality, is an graphic that, upon clicking, downloads a ZIP archive with the stealer payload.
Prepared in C++, Rhadamanthys is intended to establish connections with a command-and-management (C2) server in get to harvest delicate information from the compromised hosts.

“This marketing campaign appeared in times of the law enforcement takedown of the LockBit ransomware group,” Duncan mentioned. “Though this could be a coincidence, Pattern Micro exposed in August 2023 a Rhadamanthys variant that came bundled with a leaked LockBit payload, along with a clipper malware and cryptocurrency miner.

“The danger actors included a blend of an data stealer and a LockBit ransomware variant in a solitary Rhadamanthys bundle, potentially indicating the ongoing evolution of the malware,” the business pointed out.
The development will come amid a steady stream of new stealer malware people like Sync-Scheduler and Mighty Stealer, even as current strains like StrelaStealer are evolving with improved obfuscation and anti-analysis techniques.
It also follows the emergence of a malspam marketing campaign concentrating on Indonesia that employs banking-connected lures to propagate the Agent Tesla malware to plunder delicate details this kind of as login credentials, money details, and personal paperwork.
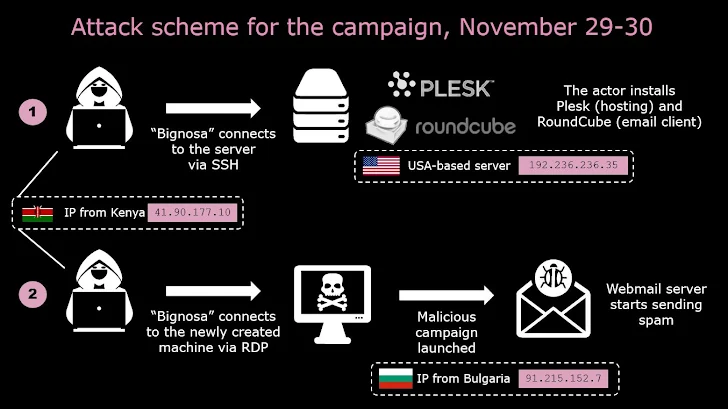
Agent Tesla phishing strategies noticed in November 2023 have also established their sights on Australia and the U.S., according to Verify Stage, which attributed the functions to two African-origin threat actors tracked as Bignosa (aka Nosakhare Godson and Andrei Ivan) and Gods (aka GODINHO or Kmarshal or Kingsley Fredrick), the latter of whom will work as a web designer.

“The primary actor [Bignosa] seems to be a component of a team running malware and phishing campaigns, concentrating on businesses, which is testified by the US and Australian email enterprise databases, as perfectly as people today,” the Israeli cybersecurity business reported.
The Agent Tesla malware distributed by using these attack chains have been uncovered to be secured by the Cassandra Protector, which assists guard program applications against reverse-engineering or modification efforts. The messages are sent via an open-supply webmail tool known as RoundCube.
“As witnessed from the description of these risk actors’ steps, no rocket science diploma is required to perform the cyber crime functions driving one particular of the most commonplace malware households in the past many several years,” Examine Level stated.
“It is an unlucky training course of functions induced by the minimal-entry degree threshold so that any person keen to provoke victims to start the malware by using spam strategies can do so.”
Observed this post appealing? Comply with us on Twitter and LinkedIn to examine much more distinctive written content we submit.
Some parts of this article are sourced from:
thehackernews.com


 Considerations for Operational Technology Cybersecurity
Considerations for Operational Technology Cybersecurity