Cybersecurity scientists have disclosed specifics of an ongoing phishing marketing campaign that leverages recruiting- and occupation-themed lures to produce a Windows-based backdoor named WARMCOOKIE.
“WARMCOOKIE seems to be an first backdoor tool applied to scout out target networks and deploy added payloads,” Elastic Security Labs researcher Daniel Stepanic mentioned in a new evaluation. “Just about every sample is compiled with a tricky-coded [command-and-control] IP handle and RC4 important.”
The backdoor comes with abilities to fingerprint contaminated equipment, capture screenshots, and drop far more destructive plans. The organization is tracking the activity under the title REF6127.
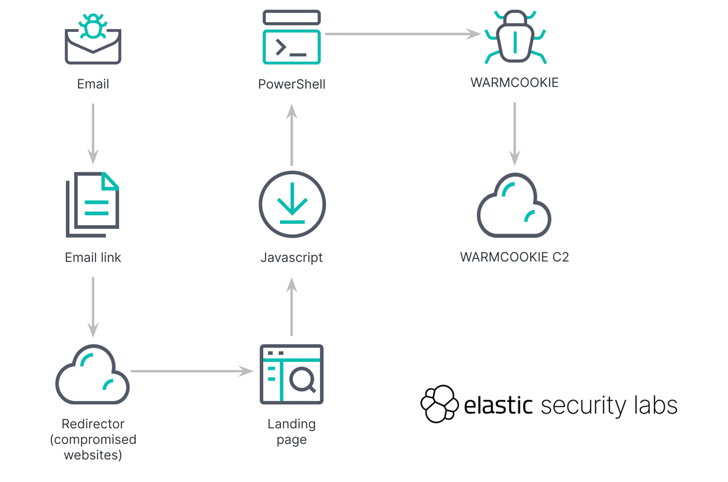
The attack chains observed considering that late April contain the use of email messages purporting to be from recruitment firms like Hays, Michael Web page, and PageGroup, urging recipients to click on an embedded hyperlink to see information about a occupation option.
Consumers who conclude up clicking on the url are then prompted to download a document by fixing a CAPTCHA challenge, adhering to which a JavaScript file (“Update_23_04_2024_5689382.js”) is dropped.
“This obfuscated script runs PowerShell, kicking off the initial task to load WARMCOOKIE,” Elastic said. “The PowerShell script abuses the Qualifications Smart Transfer Provider (BITS) to obtain WARMCOOKIE.”
A vital component of the marketing campaign is the use of compromised infrastructure to host the original phishing URL, which is then used to redirect victims to the ideal landing webpage.
A Windows DLL, WARMCOOKIE follows a two-action system that permits for creating persistence utilizing a scheduled process and launching the core functionality, but not in advance of performing a sequence of anti-assessment checks to sidestep detection.
The backdoor is designed to seize information about the infected host in a method that’s very similar to an artifact utilized in relationship with a prior marketing campaign codenamed Resident that targeted manufacturing, commercial, and health care companies.
It also supports commands to study from and compose to documents, execute commands utilizing cmd.exe, fetch the listing of installed apps, and get screenshots.
“WARMCOOKIE is a newly discovered backdoor that is gaining attractiveness and is becoming employed in campaigns concentrating on customers throughout the world,” Elastic claimed.
The disclosure will come as Trustwave SpiderLabs in-depth a advanced phishing marketing campaign that employs invoice-associated decoys and takes gain of the Windows look for features embedded in HTML code to deploy malware.
The email messages bear a ZIP archive made up of an HTML file, which uses the legacy Windows “search:” URI protocol handler to screen a Shortcut (LNK) file hosted on a distant server in the Windows Explorer, giving the effect it is a community search end result.

“This LNK file details to a batch script (BAT) hosted on the exact same server, which, on person click on, could potentially cause added malicious functions,” Trustwave said, adding it could not retrieve the batch script thanks to the server becoming unresponsive.
It truly is worthy of noting that the abuse of search-ms: and look for: as a malware distribution vector was documented by Trellix in July 2023.
“Even though this attack does not use automatic installation of malware, it does demand users to interact with several prompts and clicks,” the business said. “However, this approach cleverly obscures the attacker’s real intent, exploiting the have confidence in customers put in acquainted interfaces and popular actions like opening email attachments.”
Observed this post exciting? Abide by us on Twitter and LinkedIn to read extra unique material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 China-Backed Hackers Exploit Fortinet Flaw, Infecting 20,000 Systems Globally
China-Backed Hackers Exploit Fortinet Flaw, Infecting 20,000 Systems Globally