A recently disclosed critical security flaw impacting Progress Application MOVEit Transfer is presently seeing exploitation attempts in the wild soon soon after specifics of the bug ended up publicly disclosed.
The vulnerability, tracked as CVE-2024-5806 (CVSS rating: 9.1), worries an authentication bypass that impacts the next variations –
- From 2023.. right before 2023..11
- From 2023.1. right before 2023.1.6, and
- From 2024.. ahead of 2024..2
“Improper authentication vulnerability in Development MOVEit Transfer (SFTP module) can guide to Authentication Bypass,” the enterprise claimed in an advisory produced Tuesday.

Progress has also addressed another critical SFTP-affiliated authentication bypass vulnerability (CVE-2024-5805, CVSS rating: 9.1) impacting MOVEit Gateway model 2024…
Thriving exploitation of the flaws could let attackers to bypass SFTP authentication and attain entry to MOVEit Transfer and Gateway programs.
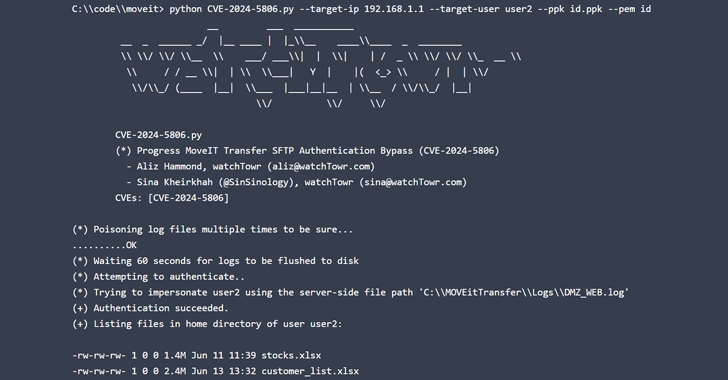
watchTowr Labs has because released added technological specifics about CVE-2024-5806, with security researchers Aliz Hammond and Sina Kheirkhah noting that it could be weaponized to impersonate any consumer on the server.
The cybersecurity firm additional described the flaw as comprising two independent vulnerabilities, one particular in Development MOVEit and the other in the IPWorks SSH library.
“Although the extra devastating vulnerability, the capability to impersonate arbitrary customers, is special to MOVEit, the fewer impactful (but nevertheless really real) forced authentication vulnerability is possible to affect all applications that use the IPWorks SSH server,” the scientists explained.
Development Computer software stated the shortcoming in the 3rd-get together part “elevates the risk of the first issue” if remaining unpatched, urging customers to follow the under two methods –
- Block general public inbound RDP entry to MOVEit Transfer server(s)
- Limit outbound access to only identified trusted endpoints from MOVEit Transfer server(s)
According to Speedy7, there are a few conditions to leveraging CVE-2024-5806: Attackers want to have understanding of an existing username, the focus on account can authenticate remotely, and the SFTP service is publicly obtainable around the internet.

As of June 25, facts gathered by Censys displays that there are around 2,700 MOVEit Transfer cases on the net, most of them located in the U.S., the U.K., Germany, the Netherlands, Canada, Switzerland, Australia, France, Eire, and Denmark.
With a further critical issue in MOVEit Transfer commonly abused in a spate of Cl0p ransomware attacks last 12 months (CVE-2023-34362, CVSS rating: 9.8), it’s vital that consumers shift speedily to update to the most current versions.
The improvement arrives as the U.S. Cybersecurity and Infrastructure Security Company (CISA) disclosed that its Chemical Security Evaluation Software (CSAT) was specific previously this January by an unknown menace actor by having advantage of security flaws in the Ivanti Join Secure (ICS) equipment (CVE-2023-46805, CVE-2024-21887, and CVE-2024-21893).
“This intrusion may possibly have resulted in the possible unauthorized access of Major-Display surveys, Security Vulnerability Assessments, Website Security Plans, Personnel Surety Plan (PSP) submissions, and CSAT person accounts,” the agency said, incorporating it observed no proof of facts exfiltration.
Located this posting appealing? Follow us on Twitter and LinkedIn to study a lot more unique written content we put up.
Some parts of this article are sourced from:
thehackernews.com

 Chinese and N. Korean Hackers Target Global Infrastructure with Ransomware
Chinese and N. Korean Hackers Target Global Infrastructure with Ransomware