A new malware marketing campaign has been noticed generating use of destructive OpenBullet configuration data files to concentrate on inexperienced cyber criminals with the objective of delivering a remote obtain trojan (RAT) capable of thieving sensitive information.
Bot mitigation business Kasada reported the activity is designed to “exploit trusted felony networks,” describing it as an instance of sophisticated danger actors “preying on rookie hackers.”
OpenBullet is a respectable open-source pen screening resource applied for automating credential stuffing assaults. It will take in a configuration file that’s personalized to a precise internet site and can combine it with a password list procured as a result of other signifies to log profitable attempts.
“OpenBullet can be used with Puppeteer, which is a headless browser that can be utilised for automating web interactions,” the company mentioned. “This would make it incredibly uncomplicated to start credential stuffing assaults devoid of having to offer with browser windows popping up.”

The configurations, essentially a piece of executable code to make HTTP requests from the goal website or web application, are also traded, or bought inside of criminal communities, reducing the bar for criminal action and enabling script kiddies to mount their possess assaults.
“The curiosity in the obtain of configs, for case in point, could suggest that the end users of OpenBullet are fairly unsophisticated,” Israeli cybersecurity firm Cybersixgill pointed out back in September 2021.
“But it could also be but yet another illustration of the dark web’s remarkably productive division of labor. That is, danger actors market that they want to purchase configs simply because they never know how to script them, but for the reason that it can be less complicated and faster.”
This versatility can also be a double-edged sword, as it opens up a new vector, only it targets other legal actors who are actively in search of these configuration documents on hacking boards.
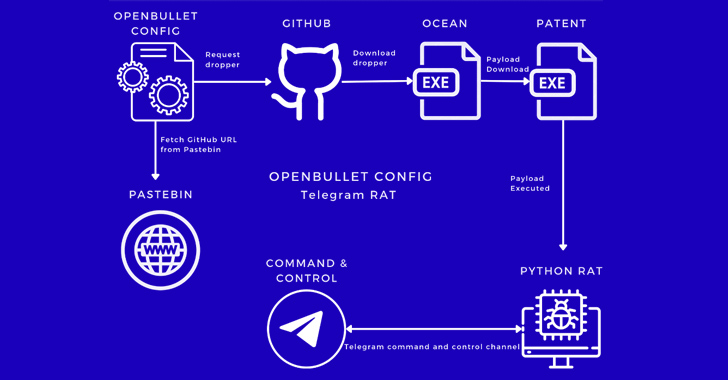
The campaign discovered by Kasada employs destructive configs shared on a Telegram channel to achieve out to a GitHub repository to retrieve a Rust-centered dropper named Ocean which is intended to fetch the upcoming-stage payload from the same repository.
The executable, a Python-based mostly malware referred to as Patent, in the end launches a distant entry trojan that utilizes Telegram as a command-and-management (C2) system and issues instructions to capture screenshots, listing directory contents, terminate responsibilities, exfiltrate crypto wallet info, and steal passwords and cookies from Chromium-based mostly web browsers.

Qualified browsers and crypto wallets involve Brave, Google Chrome, Microsoft Edge, Opera, Opera GX, Opera Crypto, Yandex Browser, Atomic, Sprint Main, Electron Hard cash, Electrum, Electrum-LTC, Ethereum Wallet, Exodus, Jaxx Liberty, Litecoin Wallet, and Mincoin.
The trojan also functions as a clipper to observe the clipboard for cryptocurrency wallet addresses and substitute contents matching a predefined normal expression with an actor-managed address, main to unauthorized fund transfers.
Two of the Bitcoin wallet addresses operated by the adversary have been given a complete of $1,703.15 about the previous two months, which were subsequently laundered working with an anonymous crypto exchange acknowledged as Fastened Float.
“The distribution of the malicious OpenBullet configs within Telegram is a novel infection vector, probably concentrating on these criminal communities thanks to their frequent use of cryptocurrencies,” the scientists stated.
“This presents an option for attackers to form their selection to a specific goal group and receive other members’ resources, accounts, or access. As the outdated indicating goes, there is no honor amongst thieves.”
Found this article intriguing? Follow us on Twitter and LinkedIn to go through far more distinctive content material we publish.
Some parts of this article are sourced from:
thehackernews.com

 North Korean Hackers Targets Russian Missile Engineering Firm
North Korean Hackers Targets Russian Missile Engineering Firm