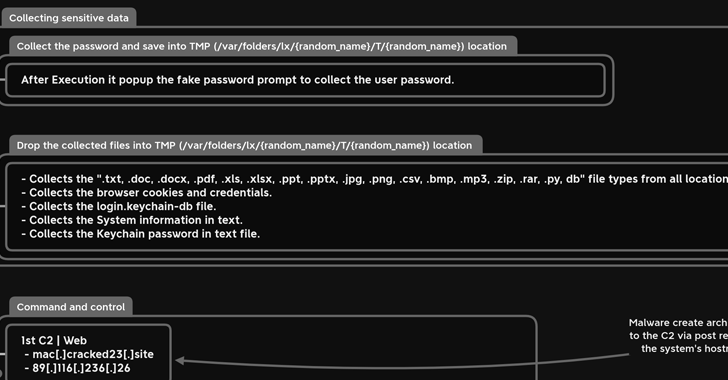
A new details-stealing malware has established its sights on Apple’s macOS working program to siphon sensitive facts from compromised equipment.
Dubbed MacStealer, it is really the hottest illustration of a menace that utilizes Telegram as a command-and-regulate (C2) system to exfiltrate data. It principally influences devices functioning macOS variations Catalina and later on working on M1 and M2 CPUs.
“MacStealer has the skill to steal documents, cookies from the victim’s browser, and login information and facts,” Uptycs scientists Shilpesh Trivedi and Pratik Jeware claimed in a new report.
1st marketed on on the web hacking forums at the begin of the thirty day period, it is nevertheless a perform in development, with the malware authors scheduling to insert attributes to seize knowledge from Apple’s Safari browser and the Notes application.
In its recent form, MacStealer is built to extract iCloud Keychain data, passwords and credit history card information and facts from browsers like Google Chrome, Mozilla Firefox, and Courageous. It also capabilities assist for harvesting Microsoft Office environment data files, photos, archives, and Python scripts.
The precise method utilised to provide the malware is not known, but it is propagated as a DMG file (weed.dmg) that, when executed, opens a fake password prompt to harvest the passwords under the guise of searching for entry to the Method Configurations application.
MacStealer is a single of numerous details-stealers that have surfaced just around the previous couple of months and adds to an previously large variety of similar applications at the moment in the wild.

This also features an additional piece of new C#-dependent malware known as HookSpoofer that is motivated by StormKitty and arrives with keylogging and clipper qualities and transmits the stolen facts to a Telegram bot.
One more browser cookie-thieving malware of observe is Ducktail, which also uses a Telegram bot to exfiltrate info and re-emerged in mid-February 2023 with enhanced strategies to sidestep detection.
This involves “changing the initial infection from an archive containing a destructive executable to an archive made up of a malicious LNK file that would start off the an infection chain,” Deep Intuition researcher Simon Kenin said earlier this month.
WEBINARDiscover the Hidden Risks of 3rd-Occasion SaaS Applications
Are you informed of the pitfalls related with 3rd-celebration application accessibility to your company’s SaaS applications? Be part of our webinar to discover about the varieties of permissions staying granted and how to decrease risk.
RESERVE YOUR SEAT
Stealer malware is commonly spread by way of unique channels, which include email attachments, bogus software package downloads, and other social engineering techniques.
To mitigate this kind of threats, it can be suggested that end users maintain their operating method and security software up to day and keep away from downloading files or clicking backlinks from mysterious sources.
“As Macs have come to be significantly well-known in the business among the management and improvement teams, the much more important the information saved on them is to attackers,” SentinelOne researcher Phil Stokes reported previous 7 days.
Uncovered this post exciting? Abide by us on Twitter and LinkedIn to examine much more special content material we put up.
Some parts of this article are sourced from:
thehackernews.com

 Latitude Financial Admits Breach Impacted Millions
Latitude Financial Admits Breach Impacted Millions