An up to date model of an information stealer malware recognized as Jupyter has resurfaced with “very simple but impactful adjustments” that purpose to stealthily set up a persistent foothold on compromised units.
“The crew has learned new waves of Jupyter Infostealer assaults which leverage PowerShell command modifications and signatures of private keys in tries to pass off the malware as a legitimately signed file,” VMware Carbon Black scientists mentioned in a report shared with The Hacker Information.
Jupyter Infostealer, also acknowledged as Polazert, SolarMarker, and Yellow Cockatoo, has a track document of leveraging manipulated search engine optimization (Web optimization) techniques and malvertising as an preliminary entry vector to trick end users browsing for common computer software into downloading it from doubtful web-sites.
It comes with abilities to harvest credentials as very well as set up encrypted command-and-regulate (C2) interaction to exfiltrate data and execute arbitrary instructions.
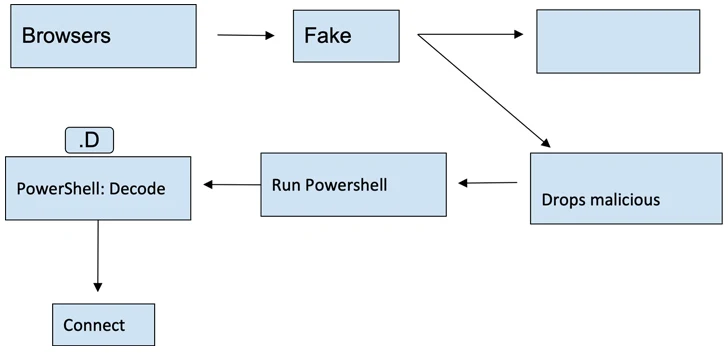
The most current set of artifacts utilizes many certificates to signal the malware to lend them a veneer of legitimacy, only for the pretend installers to activate the an infection chain on launch.
The installers are developed to invoke an interim payload that, in change, employs PowerShell to join to a remote server and finally decode and start the stealer malware.

The enhancement will come as stealer malware offered for sale on the cybercrime underground proceeds to evolve with new ways and approaches, proficiently decreasing the barrier to entry for lesser-proficient actors.
This consists of an update to Lumma Stealer, which now incorporates a loader and the capability to randomly create a construct for enhanced obfuscation.
“This requires the malware from staying a stealer sort to a more devious malware that can load 2nd-stage assaults on its victims,” VMware said. “The loader supplies a way for the threat actor to escalate its attack from info theft to nearly anything up to infecting its victims with ransomware.”
One more stealer malware spouse and children that has acquired continuous improvements is Mystic Stealer, which has also added a loader features in the latest versions to complement its information and facts-thieving qualities.
“The code carries on to evolve and grow the details theft abilities and the network conversation was current from a personalized binary TCP-based mostly protocol to an HTTP-dependent protocol,” Zscaler claimed in a report late final month.
“The new modifications have led to enhanced recognition with felony menace actors leveraging its loader performance to distribute extra malware households including RedLine, DarkGate, and GCleaner.”
The continuously evolving character of these kinds of malware is additional exemplified by the emergence of stealers and remote entry trojans such as Akira Stealer and Millenium RAT, which come fitted with a variety of functions to facilitate info theft.

The disclosure also arrives as malware loaders like PrivateLoader and Amadey have been noticed infecting countless numbers of gadgets with a proxy botnet dubbed Socks5Systemz, which has been all over considering the fact that 2016.
Cybersecurity firm Bitsight, which uncovered specifics of the support past 7 days, claimed it determined at minimum 53 servers connected to the botnet that are distributed throughout France, Bulgaria, Netherlands, and Sweden.
The top purpose of the campaign is to switch infected machines into proxies able of forwarding site visitors for other actors, genuine or usually, as an added layer of anonymity. It’s suspected that the danger actors are of Russian origin, specified the absence of infections in the state.
“The proxy provider allows customers to choose a subscription ranging from $1 USD to $4,000 USD, payable in whole making use of cryptocurrency,” Bitsight reported. “Based mostly on network telemetry analysis, it is approximated that this botnet has about 10,000 contaminated programs with victims spread throughout the world.”
Uncovered this short article attention-grabbing? Stick to us on Twitter and LinkedIn to examine far more exceptional content we post.
Some parts of this article are sourced from:
thehackernews.com


 QNAP Releases Patch for 2 Critical Flaws Threatening Your NAS Devices
QNAP Releases Patch for 2 Critical Flaws Threatening Your NAS Devices