A new Go-dependent malware loader identified as JinxLoader is being used by threat actors to supply following-stage payloads these kinds of as Formbook and its successor XLoader.
The disclosure will come from cybersecurity companies Palo Alto Networks Unit 42 and Symantec, equally of which highlighted multi-move attack sequences that led to the deployment of JinxLoader by way of phishing assaults.
“The malware pays homage to League of Legends character Jinx, that includes the character on its advertisement poster and [command-and-control] login panel,” Symantec reported. “JinxLoader’s major function is straightforward – loading malware.”
Device 42 unveiled in late November 2023 that the malware service was 1st marketed on hackforums[.]net on April 30, 2023, for $60 a month, $120 a yr, or for a life time price of $200.

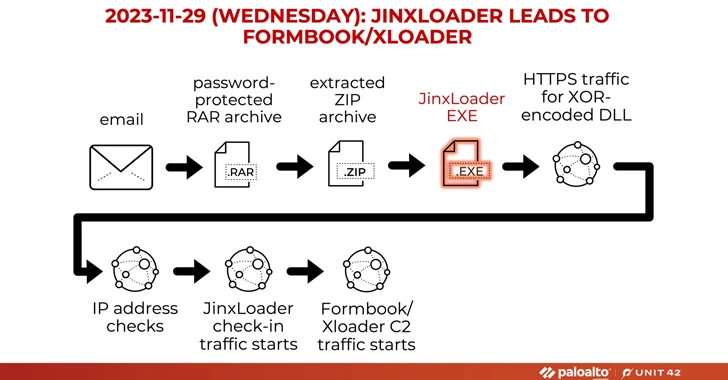
The assaults start out with phishing email messages impersonating Abu Dhabi Nationwide Oil Business (ADNOC), urging recipients to open up password-shielded RAR archive attachments that, upon opening, fall the JinxLoader executable, which subsequently functions as a gateway for Formbook or XLoader.
The advancement will come as ESET exposed a spike in infections, providing another beginner loader malware loved ones dubbed Rugmi to propagate a extensive selection of facts stealers.
It also will come amid a surge in campaigns distributing DarkGate and PikaBot, with a threat actor known as TA544 (aka Narwal Spider) leveraging new variants of loader malware named IDAT Loader to deploy Remcos RAT or SystemBC malware.
What is far more, the menace actors guiding the Meduza Stealer have released an current model of the malware (edition 2.2) on the dark web with expanded assistance for browser-based mostly cryptocurrency wallets and an enhanced credit rating card (CC) grabber.

In a indication that stealer malware proceeds to be a profitable current market for cybercriminals, scientists have found a new stealer household acknowledged as Vortex Stealer that is capable of exfiltrating browser facts, Discord tokens, Telegram sessions, technique information, and documents that are fewer than 2 MB in sizing.
“Stolen information will be archived and uploaded to Gofile or Anonfiles the malware will also post it onto the author’s Discord making use of webhooks,” Symantec stated. “It really is also capable of putting up to Telegram via a Telegram bot.”
Discovered this report fascinating? Abide by us on Twitter and LinkedIn to browse extra special written content we article.
Some parts of this article are sourced from:
thehackernews.com

 Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks
Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks