Cybersecurity scientists have recognized a “lightweight approach” termed iShutdown for reliably identifying indications of spyware on Apple iOS units, which includes infamous threats like NSO Group’s Pegasus, QuaDream’s Reign, and Intellexa’s Predator.
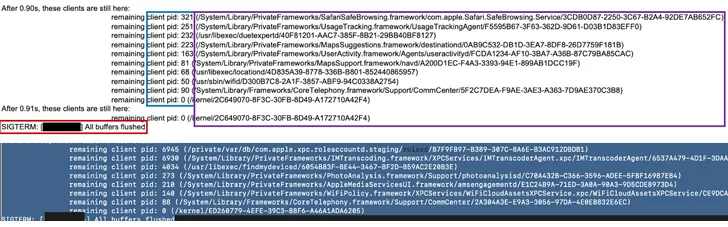
Kaspersky, which analyzed a set of iPhones that have been compromised with Pegasus, claimed the infections remaining traces in a file named “Shutdown.log,” a text-based mostly method log file obtainable on all iOS units and which information every reboot event together with its natural environment properties.

“In contrast to far more time-consuming acquisition strategies like forensic device imaging or a comprehensive iOS backup, retrieving the Shutdown.log file is fairly uncomplicated,” security researcher Maher Yamout said. “The log file is saved in a sysdiagnose (sysdiag) archive.”
The Russian cybersecurity business mentioned it identified entries in the log file that recorded instances in which “sticky” processes, these kinds of as individuals linked with the adware, induced a reboot hold off, in some situations observing Pegasus-related processes in around 4 reboot hold off notices.
What’s extra, the investigation exposed a the presence of a related filesystem route which is used by all the a few adware households – “/non-public/var/db/” for Pegasus and Reign, and “/private/var/tmp/” for Predator – thus performing as an indicator of compromise.
That mentioned, the success of this strategy hinges on a caveat that the concentrate on person reboots their machine as normally as doable, the frequency for which differs in accordance to their threat profile.
Kaspersky has also posted a assortment of Python scripts to extract, examine, and parse the Shutdown.log in get to extract the reboot stats.
“The lightweight character of this approach tends to make it conveniently accessible and accessible,” Yamout mentioned. “Furthermore, this log file can retail outlet entries for quite a few yrs, generating it a precious forensic artifact for analyzing and figuring out anomalous log entries.”

The disclosure will come as SentinelOne discovered data stealers focusing on macOS these types of as KeySteal, Atomic, and JaskaGo (aka CherryPie or Gary Stealer) are quickly adapting to circumvent Apple’s created-in antivirus technology called XProtect.
“Regardless of solid endeavours by Apple to update its XProtect signature database, these rapidly evolving malware strains continue on to evade,” security researcher Phil Stokes reported. “Relying exclusively on signature-dependent detection is insufficient as danger actors have the means and motive to adapt at velocity.”
Observed this write-up fascinating? Abide by us on Twitter and LinkedIn to read through a lot more distinctive material we article.
Some parts of this article are sourced from:
thehackernews.com


 GitHub Rotates Keys After High-Severity Vulnerability Exposes Credentials
GitHub Rotates Keys After High-Severity Vulnerability Exposes Credentials