A new variant of the GootLoader malware termed GootBot has been observed to facilitate lateral motion on compromised devices and evade detection.
“The GootLoader group’s introduction of their own tailor made bot into the late phases of their attack chain is an try to avoid detections when using off-the-shelf equipment for C2 such as CobaltStrike or RDP,” IBM X-Power scientists Golo Mühr and Ole Villadsen stated.
“This new variant is a lightweight but helpful malware letting attackers to fast unfold in the course of the network and deploy further more payloads.”
GootLoader, as the title indicates, is a malware capable of downloading next-phase malware right after luring possible victims working with lookup engine optimization (Web optimization) poisoning techniques. It’s linked to a threat actor tracked as Hive0127 (aka UNC2565).

The use of GootBot points to a tactical shift, with the implant downloaded as a payload just after a Gootloader infection in lieu of publish-exploitation frameworks these as CobaltStrike.”
Described as an obfuscated PowerShell script, GootBot is developed to connect to a compromised WordPress internet site for command and manage and receive even further instructions.
Complicating issues even further is the use of a one of a kind tricky-coded C2 server for each and every deposited GootBot sample, creating it challenging to block destructive targeted visitors.
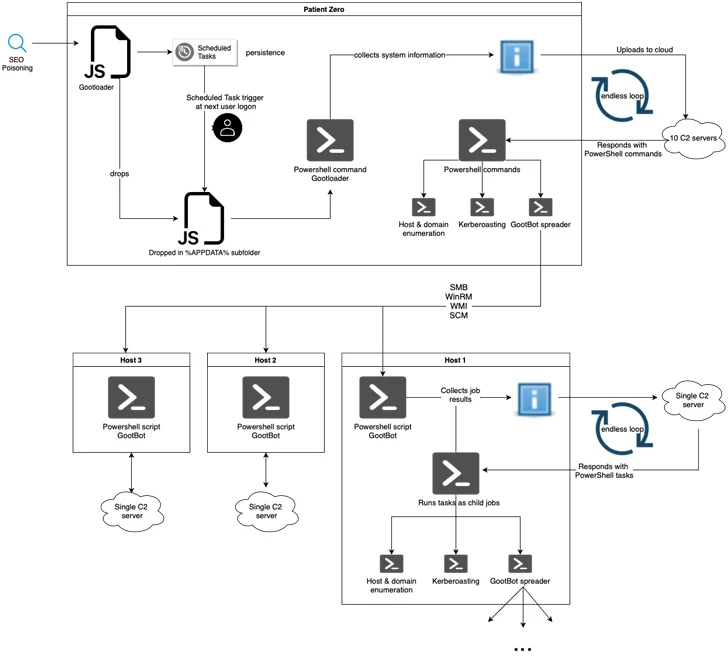
“Currently observed strategies leverage Web optimization-poisoned searches for themes this kind of as contracts, legal sorts, or other enterprise-related documents, directing victims to compromised internet sites built to appear like reputable forums the place they are tricked into downloading the original payload as an archive file,” the scientists mentioned.
The archive file incorporates an obfuscated JavaScript file, which, on execution, fetches yet another JavaScript file which is induced by using a scheduled process to realize persistence.

In the next stage, JavaScript is engineered to run a PowerShell script for gathering system information and facts and exfiltrating it to a remote server, which, in change, responds with a PowerShell script that is operate in an infinite loop and grants the danger actor to distribute various payloads.
This includes GootBot, which beacons out to its C2 server each individual 60 seconds to fetch PowerShell responsibilities for execution and transmit the effects of the execution back to the server in the type of HTTP Post requests.
Some of the other capabilities of GootBot vary from reconnaissance to carrying out lateral motion across the environment, successfully increasing the scale of the attack.
“The discovery of the Gootbot variant highlights the lengths to which attackers will go to evade detection and run in stealth,” the researchers mentioned. “This shift in TTPs and tooling heightens the risk of profitable article-exploitation levels, these kinds of as GootLoader-linked ransomware affiliate action.”
Identified this short article appealing? Adhere to us on Twitter and LinkedIn to read through extra distinctive content material we submit.
Some parts of this article are sourced from:
thehackernews.com


 Confidence in File Upload Security is Alarmingly Low. Why?
Confidence in File Upload Security is Alarmingly Low. Why?