The cyber assaults concentrating on the power sector in Denmark past 12 months may not have experienced the involvement of the Russia-connected Sandworm hacking group, new results from Forescout clearly show.
The intrusions, which targeted close to 22 Danish energy organizations in May well 2023, occurred in two distinctive waves, a person which exploited a security flaw in Zyxel firewall (CVE-2023-28771) and a stick to-on activity cluster that saw the attackers deploy Mirai botnet variants on infected hosts by means of an as-nonetheless-mysterious preliminary obtain vector.

The initially wave took put on May well 11, even though the 2nd wave lasted from May possibly 22 to 31, 2023. In a single such attack detected on May perhaps 24, it was observed that the compromised process was speaking with IP addresses (217.57.80[.]18 and 70.62.153[.]174) that ended up earlier used as command-and-management (C2) for the now-dismantled Cyclops Blink botnet.
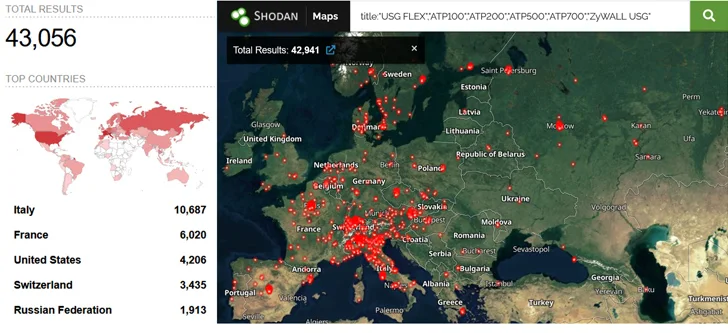
Forescout’s nearer assessment of the attack campaign, however, has unveiled that not only had been the two waves unrelated, but also not likely the do the job of the state-sponsored team owing to the fact the next wave was section of a broader mass exploitation marketing campaign from unpatched Zyxel firewalls. It’s presently not regarded who is behind the twin sets of attacks.
“The marketing campaign described as the ‘second wave’ of attacks on Denmark, started off prior to and continued immediately after [the 10-day time period], concentrating on firewalls indiscriminately in a quite comparable fashion, only transforming staging servers periodically,” the enterprise mentioned in a report aptly titled “Clearing the Fog of War.”

There is proof to propose that the assaults may have begun as early as February 16 using other identified flaws Zyxel products (CVE-2020-9054 and CVE-2022-30525) along with CVE-2023-28771, and persisted as late as October 2023, with the exercise singling out various entities throughout Europe and the U.S.
“This is more proof that exploitation of CVE-2023-27881, alternatively than getting constrained to Danish critical infrastructure, is ongoing and focusing on uncovered devices, some of which just transpire to be Zyxel firewalls safeguarding critical infrastructure organizations,” Forescout extra.
Identified this article exciting? Follow us on Twitter and LinkedIn to go through more unique content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Critical RCE Vulnerability Uncovered in Juniper SRX Firewalls and EX Switches
Critical RCE Vulnerability Uncovered in Juniper SRX Firewalls and EX Switches