Buyers in Latin The usa (LATAM) are the goal of a financial malware named JanelaRAT which is able of capturing delicate info from compromised Microsoft Windows programs.
“JanelaRAT primarily targets fiscal and cryptocurrency info from LATAM financial institution and fiscal establishments,” Zscaler ThreatLabz researchers Gaetano Pellegrino and Sudeep Singh stated, introducing it “abuses DLL side-loading techniques from respectable sources (like VMWare and Microsoft) to evade endpoint detection.”
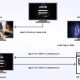
The correct commencing issue of the infection chain is unclear, but the cybersecurity corporation, which uncovered the marketing campaign in June 2023, mentioned the mysterious vector is used to supply a ZIP archive file made up of a Visible Primary Script.

The VBScript is engineered to fetch a 2nd ZIP archive from the attackers’ server as perfectly as fall a batch file utilised to create persistence of the malware.
The ZIP archive is packed with two components, the JanelaRAT payload and a reputable executable — id_helper.exe or vmnat.exe — that is made use of to start the previous by indicates of DLL side-loading.
JanelaRAT, for its portion, employs string encryption and transitions into an idle state when needed to steer clear of investigation and detection. It’s also a seriously modified variant of BX RAT, which was to start with learned in 2014.
One of the new additions to the trojan is its means to capture windows titles and send out them to the menace actors, but not prior to registering the freshly-contaminated host with the command-and-management (C2) server. Other capabilities of JanelaRAT permit it to track mouse inputs, log keystrokes, just take screenshots, and harvest process metadata.
“JanelaRAT ships with just a subset of the options presented by BX RAT,” the researchers explained. “The JanelaRAT developer failed to import shell instructions execution operation, or information and procedures manipulation functionalities.”

A closer investigation of the resource code has discovered the presence of a number of strings in Portuguese, indicating that the writer is common with the language.
The links to LATAM occur from references to businesses working in the banking and decentralized finance verticals and the reality that the VBScript uploads to VirusTotal originated from Chile, Colombia, and Mexico.
“The usage of original or modified commodity Remote Entry Trojans (RATs) is prevalent among threat actors working in the LATAM location,” the scientists mentioned. “JanelaRAT’s concentration on harvesting LATAM financial facts and its process of extracting window titles for transmission underscores its qualified and stealthy nature.”
Identified this post exciting? Stick to us on Twitter and LinkedIn to go through a lot more exceptional content material we submit.
Some parts of this article are sourced from:
thehackernews.com

 India Passes New Digital Personal Data Protection Bill (DPDPB), Putting Users’ Privacy First
India Passes New Digital Personal Data Protection Bill (DPDPB), Putting Users’ Privacy First