A new elaborate attack marketing campaign has been noticed utilizing PowerShell and VBScript malware to infect Windows systems and harvest sensitive facts.
Cybersecurity business Securonix, which dubbed the campaign DEEP#GOSU, mentioned it’s probably associated with the North Korean state-sponsored team tracked as Kimsuky.
“The malware payloads utilised in the DEEP#GOSU symbolize a complex, multi-phase menace built to function stealthily on Windows techniques specially from a network-monitoring standpoint,” security scientists Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a technological evaluation shared with The Hacker Information.
“Its capabilities integrated keylogging, clipboard monitoring, dynamic payload execution, and data exfiltration, and persistence applying the two RAT computer software for whole remote access, scheduled jobs as properly as self-executing PowerShell scripts using employment.”
A notable facet of the an infection technique is that it leverages legit providers these types of as Dropbox or Google Docs for command-and-command (C2), consequently allowing for the danger actor to blend undetected into regular network traffic.
On best of that, the use of this sort of cloud expert services to stage the payloads makes it possible for for updating the performance of the malware or providing further modules.
The beginning place is stated to be a destructive email attachment made up of a ZIP archive with a rogue shortcut file (.LNK) that masquerades as a PDF file (“IMG_20240214_0001.pdf.lnk”).
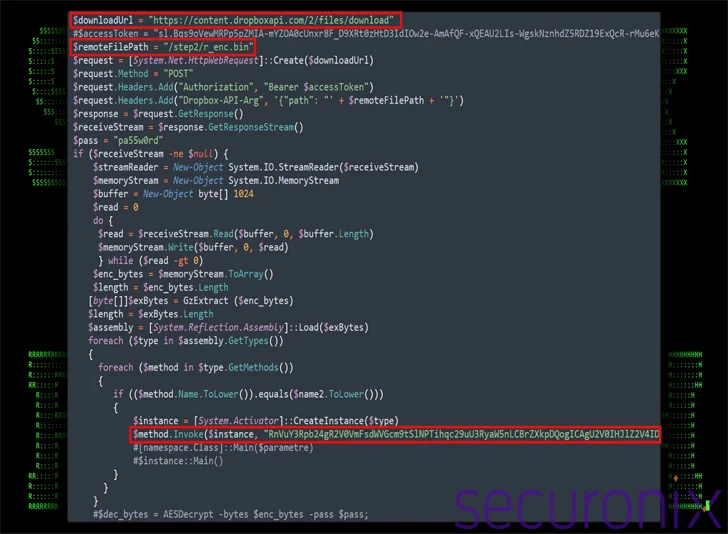
The .LNK file comes embedded with a PowerShell script as well as a decoy PDF document, with the former also reaching out to an actor-controlled Dropbox infrastructure to retrieve and execute one more PowerShell script (“ps.bin”).

The 2nd-phase PowerShell script, for its element, fetches a new file from Dropbox (“r_enc.bin”), a .NET assembly file in binary sort that’s basically an open up-source distant entry trojan recognised as TruRat (aka TutRat or C# RAT) with abilities to record keystrokes, manage documents, and facilitate distant handle.
It can be really worth noting that Kimsuky has utilized TruRat in at minimum two strategies uncovered by the AhnLab Security Intelligence Heart (ASEC) last year.
Also retrieved by the PowerShell script from Dropbox is a VBScript (“information_sc.txt”), which, in turn, is built to operate arbitrary VBScript code retrieved from the cloud storage provider, including a PowerShell script (“w568232.ps12x”).
The VBScript is also intended to use Windows Management Instrumentation (WMI) to execute instructions on the process, and established up scheduled responsibilities on the procedure for persistence.
Yet another noteworthy component of the VBScript is the use of Google Docs to dynamically retrieve configuration knowledge for the Dropbox connection, letting the risk actor to modify the account information devoid of getting to alter the script by itself.
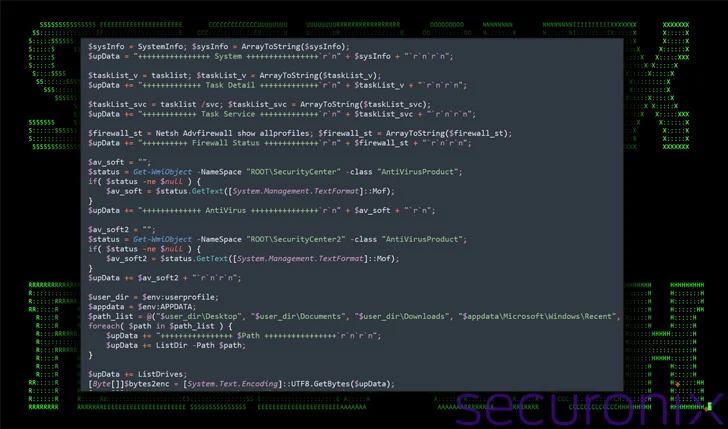
The PowerShell script downloaded as a end result is equipped to acquire extensive facts about the technique and exfiltrate the specifics by means of a Article ask for to Dropbox.
“The goal of this script appears to be made to provide as a resource for periodic communication with a command-and-command (C2) server through Dropbox,” the researchers stated. “Its major functions include things like encrypting and exfiltrating or downloading information.”
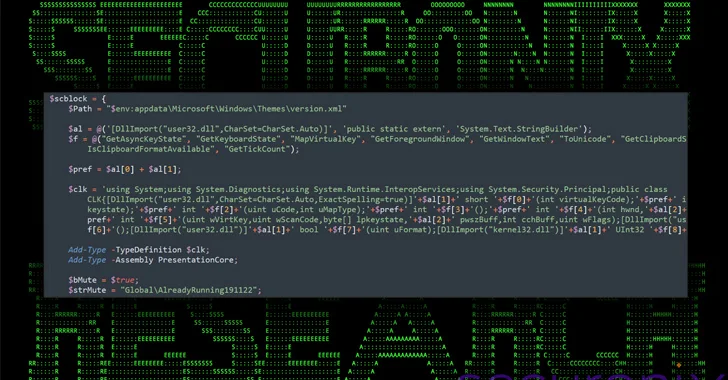
In other text, it acts as a backdoor to command the compromised hosts and constantly retain a log of user action, together with keystrokes, clipboard material, and the foreground window.
The enhancement comes as security researcher Ovi Liber thorough North Korea-joined ScarCruft’s embedding of malicious code inside of Hangul Phrase Processor (HWP) lure files present in phishing e-mail to distribute malware like RokRAT.
“The email contains a HWP Doc which has an embedded OLE object in the sort of a BAT script,” Liber claimed. “The moment the person clicks on the OLE object, the BAT script executes which in change makes a PowerShell-primarily based reflective DLL injection attack on the victims device.”
It also follows Andariel’s exploitation of a legitimate remote desktop resolution referred to as MeshAgent to install malware like AndarLoader and ModeLoader, a JavaScript malware intended for command execution.
“This is the to start with verified use of a MeshAgent by the Andariel team,” ASEC mentioned. “The Andariel Team has been consistently abusing the asset administration answers of domestic providers to distribute malware in the approach of lateral motion, starting up with Innorix Agent in the past.”

Andariel, also identified by the names Nicket Hyatt or Silent Chollima, is a sub-cluster of the notorious Lazarus Team, actively orchestrating attacks for both cyber espionage and monetary obtain.
The prolific point out-sponsored threat actor has considering the fact that been noticed laundering a chunk of the crypto assets stolen from the hack of crypto exchange HTX and its cross-chain bridge (aka HECO Bridge) by Tornado Money. The breach led to the theft of $112.5 million in cryptocurrency in November 2023.
“Next widespread crypto-laundering styles, the stolen tokens ended up instantly swapped for ETH, making use of decentralized exchanges,” Elliptic stated. “The stolen funds then lay dormant until March 13, 2024, when the stolen crypto belongings started to be despatched through Twister Income.”
The blockchain analytics agency stated that Twister Cash’s continuation of its functions despite sanctions have probable manufactured it an appealing proposition for the Lazarus Team to conceal its transaction path subsequent the shutdown of Sinbad in November 2023.
“The mixer operates by means of smart contracts running on decentralized blockchains, so it are unable to be seized and shut down in the identical way that centralized mixers such as Sinbad.io have been,” it famous.
Discovered this short article exciting? Follow us on Twitter and LinkedIn to go through additional special written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Fortra Patches Critical RCE Vulnerability in FileCatalyst Transfer Tool
Fortra Patches Critical RCE Vulnerability in FileCatalyst Transfer Tool