This report has not been generated by ChatGPT.
2022 was the 12 months when inflation hit globe economies, besides in just one corner of the world-wide market – stolen facts. Ransomware payments fell by over 40% in 2022 compared to 2021. Much more organisations chose not to pay back ransom requires, in accordance to results by blockchain organization Chainalysis.
Nevertheless, stolen info has price beyond a price tag, and in dangerous techniques you may well not assume. Assessing stolen documents is what Lab 1, a new cyber checking platform, thinks will make a large change for extensive-time period cybersecurity resilience.
Think of info worth this way:
- Stolen credentials can become long term phishing assaults
- Logins for adult internet websites are potential extortion attempts
- Journey and spot info are a risk to VIPs and senior leadership,
- And so on…
Hackers could retaliate for non-payment by simply publishing their loot to message boards wherever the knowledge will be out there for even further enrichment and exploitation.
Shining a light on dark sites
Even though your enterprise might not have suffered a immediate breach, your facts may possibly presently be on the Dark Web. That is why Lab 1 will get hold of available facts and contextualises it to evaluate risk.
The Dark Web begun off as a closed network to safeguard dissidents. Now 50 % of it is a common backwater for felony exercise. In accordance to the IMF, knowledge marketplaces are the 2nd most well-known action immediately after pharma and recreational medicines.
Marketplace investigation in 2022 also observed more than 24 billion username and password combinations on sale on the dark web, up from 15 billion in 2020. But there can be other information – intellectual residence, accountancy documents, employee information and more.
Breaches stop up staying promoted by hackers with information descriptions and auction needs, typically in Bitcoin. By obtaining keep of these records, no issue their benefit or 50 % life, Lab 1 builds a photo of risk exposure.
Chain reaction
You may possibly not imagine of your source chain as a supply of cybersecurity risk, but you should. 53% of organisations have experienced a knowledge breach induced by 3rd social gathering info theft, according to Ponemon Institute.
Facts breaches can and do unfold outside the perimeter of your business. Which is the insight that drives the Lab 1 platform. In an interconnected business enterprise, the resources you use, the businesses you employ the service of, and the subcontractors you use to execute everyday business are all likely vectors of attack.
Say you are a consumer of a computer software vendor, and their stolen knowledge pack features code obtain to the servers of various customers, it truly is very likely to include things like yours. Or what if journey information of VIP buyers get leaked and they’re about to exhibit up at an crucial convention?
Keep track of your supply chain
Fallouts from cybersecurity breaches never have to be inescapable. Lab 1 monitors, alerts and analyses information breaches throughout a firm’s total provide chain by discovering and contextualising facts found on boards, messaging platforms and Dark Web marketplaces.
Working with Lab 1, organisations can “adhere to” the companies they function with and get alerted if any of them have been breached that would pose a risk. This can be particularly useful for breach insurance coverage and other risk-similar provisions.
For the reason that Lab 1 is acquiring new data entities by the 2nd – 24bn to date – and is incorporating them to CiGraph, its graph database, the checking is ongoing.
As and when incidents are recorded or knowledge results in being out there, Lab 1 systems offer a in close proximity to-serious-time alerting services identified as Blast Radius. It lets security groups to dig further on what transpired.
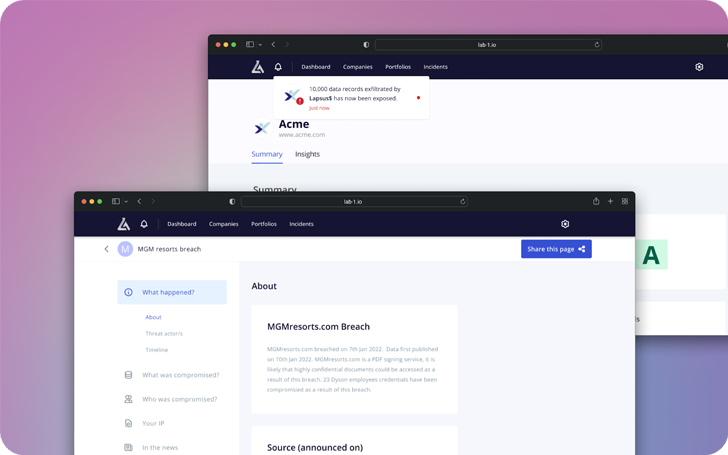
Handle the network result of breaches
Every single incident generates fallout that impacts other businesses, at times in their thousands. Lab 1’s Fallout support specifics this network effect and how firms you comply with (like your possess) are impacted.
Lab 1 also facts history, risk quantification, and proposed cures, based on the character and sizing of the breach. Serving to to protect against attack, control problems and watch dwell risk quantification across 1000’s of suppliers, with the intention for companies to establish much more sturdy offer chains.
To discover out if you can find a concealed facts breach that requires your organization, go to https://www.lab-1.io/, exactly where CiGraph could but expose a Dark Web magic formula you did not know you had.
Observed this write-up intriguing? Stick to us on Twitter and LinkedIn to examine far more unique written content we article.
Some parts of this article are sourced from:
thehackernews.com


 “Hinata” Botnet Could Launch Massive DDoS Attacks
“Hinata” Botnet Could Launch Massive DDoS Attacks