Cybersecurity researchers have uncovered the to start with-ever illicit cryptocurrency mining marketing campaign utilised to mint Dero given that the start off of February 2023.
“The novel Dero cryptojacking procedure concentrates on finding Kubernetes clusters with nameless entry enabled on a Kubernetes API and listening on non-normal ports accessible from the internet,” CrowdStrike stated in a new report shared with The Hacker Information.
The development marks a noteworthy change from Monero, which is a widespread cryptocurrency utilized in these campaigns. It is really suspected it might have to do with the simple fact that Dero “provides larger sized benefits and delivers the exact or far better anonymizing characteristics.”
The assaults, attributed to an unfamiliar fiscally inspired actor, start with scanning for Kubernetes clusters with authentication established as –anonymous-auth=accurate, which permits nameless requests to the server, to fall preliminary payloads from three different U.S.-centered IP addresses.
This features deploying a Kubernetes DaemonSet named “proxy-api,” which, in switch, is used to drop a malicious pod on just about every node of the Kubernetes cluster to kick-start out the mining exercise.
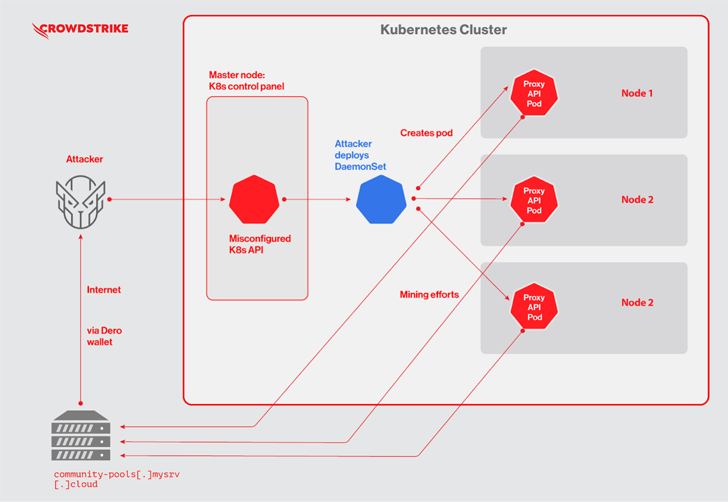
To that stop, the DaemonSet’s YAML file is orchestrated to operate a Docker impression that is made up of a “pause” binary, which is truly the Dero coin miner.
“In a legitimate Kubernetes deployment, ‘pause’ containers are employed by Kubernetes to bootstrap a pod,” the business pointed out. “Attackers may possibly have utilised this name to mix in to stay clear of apparent detection.”
WEBINARDiscover the Hidden Hazards of Third-Party SaaS Apps
Are you knowledgeable of the dangers affiliated with 3rd-social gathering app access to your company’s SaaS apps? Join our webinar to find out about the styles of permissions being granted and how to reduce risk.
RESERVE YOUR SEAT
The cybersecurity company claimed it discovered a parallel Monero-mining campaign also concentrating on exposed Kubernetes clusters by making an attempt to delete the current “proxy-api” DaemonSet involved with the Dero marketing campaign.
This is an indicator of the ongoing tussle involving cryptojacking groups that are vying for cloud assets to consider and retain manage of the devices and consume all of its resources.
“Both of those campaigns are trying to come across undiscovered Kubernetes attack surfaces and are battling it out,” CrowdStrike danger scientists Benjamin Grap and Manoj Ahuje mentioned.
Located this write-up intriguing? Adhere to us on Twitter and LinkedIn to examine additional special material we article.
Some parts of this article are sourced from:
thehackernews.com


 Phishing Campaigns Use SVB Collapse to Harvest Crypto
Phishing Campaigns Use SVB Collapse to Harvest Crypto