End users in Brazil are the focus on of a new banking trojan identified as CHAVECLOAK that is propagated by using phishing e-mail bearing PDF attachments.
“This intricate attack involves the PDF downloading a ZIP file and subsequently making use of DLL aspect-loading techniques to execute the ultimate malware,” Fortinet FortiGuard Labs researcher Cara Lin explained.
The attack chain includes the use of agreement-themed DocuSign lures to trick buyers into opening PDF files that contains a button to browse and sign the paperwork.
In reality, clicking the button prospects to the retrieval of an installer file from a distant connection which is shortened applying the Goo.su URL shortening service.
Current inside of the installer is an executable named “Lightshot.exe” that leverages DLL facet-loading to load “Lightshot.dll,” which is the CHAVECLOAK malware that facilitates the theft of delicate info.
This features collecting method metadata and operating checks to figure out whether or not the compromised machine is located in Brazil and, if so, periodically checking the foreground window to compare it towards a predefined record of financial institution-related strings.

If it matches, a connection is recognized with a command-and-management (C2) server and proceeds to harvest several varieties of data and exfiltrate them to distinctive endpoints on the server dependent on the fiscal establishment.
“The malware facilitates several actions to steal a victim’s qualifications, such as letting the operator to block the victim’s monitor, log keystrokes, and display deceptive pop-up windows,” Lin stated.
“The malware actively displays the victim’s accessibility to particular economical portals, which include a number of banks and Mercado Bitcoin, which encompasses equally classic banking and cryptocurrency platforms.”
Fortinet explained it also uncovered a Delphi variant of CHAVECLOAK, after again highlighting the prevalence of Delphi-based mostly malware focusing on Latin The united states.

“The emergence of the CHAVECLOAK banking Trojan underscores the evolving landscape of cyberthreats concentrating on the financial sector, particularly focusing on end users in Brazil,” Lin concluded.
The results arrive amid an ongoing cellular banking fraud campaign from the U.K., Spain, and Italy that involves using smishing and vishing (i.e., SMS and voice phishing) strategies to deploy an Android malware called Copybara with the aim of executing unauthorized banking transfers to a network of lender accounts operated by dollars mules.
“TAs [Threat actors] have been caught using a structured way of controlling all the ongoing phishing strategies by using a centralized web panel acknowledged as ‘Mr. Robot,'” Cleafy explained in a report posted last 7 days.

“With this panel, TAs can enable and manage a number of phishing campaigns (from distinctive fiscal institutions) centered on their requirements.”
The C2 framework also makes it possible for attackers to orchestrate tailor-made attacks on unique money establishments employing phishing kits that are engineered to mimic the person interface of the specific entity, while also adopting anti-detection approaches by using geofencing and product fingerprinting to limit connections only from cellular products.
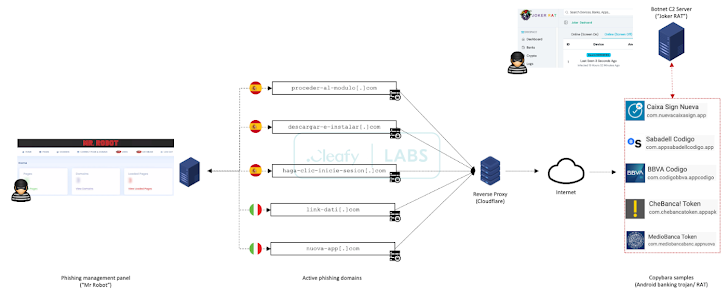
The phishing kit – which serves as a faux login web site – is dependable for capturing retail banking shopper qualifications and phone numbers and sending the information to a Telegram team.
Some of the destructive infrastructure applied for the campaign is designed to supply Copybara, which is managed using a C2 panel named JOKER RAT that displays all the contaminated equipment and their geographical distribution in excess of a reside map.
It also lets the threat actors to remotely interact in serious-time with an contaminated gadget working with a VNC module, in addition to injecting pretend overlays on best of banking apps to siphon credentials, logging keystrokes by abusing Android’s accessibility providers, and intercepting SMS messages.

On best of that, JOKER RAT comes with an APK builder that helps make it achievable to customise the rogue app’s identify, package title, and icons.
“A different function out there within the panel is the ‘Push Notification,’ in all probability made use of to mail to the contaminated products pretend thrust notifications that appear like a lender notification to entice the person to open the bank’s application in these types of a way that the malware can steal qualifications,” Cleafy scientists Francesco Iubatti and Federico Valentini stated.
The developing sophistication of on-machine fraud (ODF) techniques is even further evidenced by a not long ago disclosed TeaBot (aka Anatsa) campaign that managed to infiltrate the Google Enjoy Retail outlet below the guise of PDF reader applications.
“This software serves as a dropper, facilitating the obtain of a banking trojan of the TeaBot relatives via numerous phases,” Iubatti reported. “Before downloading the banking trojan, the dropper performs innovative evasion tactics, such as obfuscation and file deletion, along with several checks about the target countries.”
Found this report appealing? Stick to us on Twitter and LinkedIn to go through more exceptional articles we article.
Some parts of this article are sourced from:
thehackernews.com

 Data Leakage Prevention in the Age of Cloud Computing: A New Approach
Data Leakage Prevention in the Age of Cloud Computing: A New Approach