A new variant of remote entry trojan identified as Bandook has been observed being propagated by using phishing assaults with an goal to infiltrate Windows devices, underscoring the constant evolution of the malware.
Fortinet FortiGuard Labs, which discovered the activity in October 2023, claimed the malware is distributed by way of a PDF file that embeds a link to a password-protected .7z archive.
“Just after the victim extracts the malware with the password in the PDF file, the malware injects its payload into msinfo32.exe,” security researcher Pei Han Liao stated.
Bandook, first detected in 2007, is an off-the-shelf malware that will come with a huge assortment of options to remotely attain manage of the contaminated programs.

In July 2021, Slovak cybersecurity business ESET detailed a cyber espionage campaign that leveraged an upgraded variant of Bandook to breach company networks in Spanish-speaking nations around the world this kind of as Venezuela.
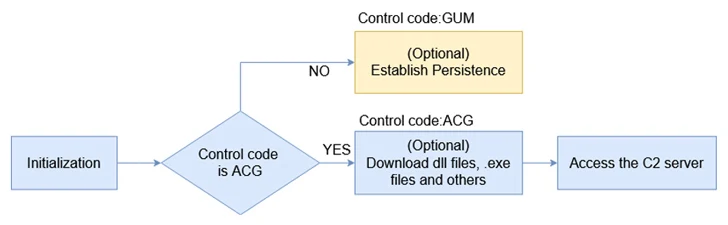
The beginning place of the hottest attack sequence is an injector element that’s created to decrypt and load the payload into msinfo32.exe, a legit Windows binary that gathers system data to diagnose computer system issues.
The malware, moreover building Windows Registry adjustments to create persistence on the compromised host, establishes speak to with a command-and-control (C2) server to retrieve extra payloads and guidance.
“These actions can be around categorized as file manipulation, registry manipulation, down load, information stealing, file execution, invocation of functions in DLLs from the C2, managing the victim’s personal computer, system killing, and uninstalling the malware,” Han Liao stated.
Found this post interesting? Observe us on Twitter and LinkedIn to go through far more distinctive material we article.
Some parts of this article are sourced from:
thehackernews.com


 Three Ways To Supercharge Your Software Supply Chain Security
Three Ways To Supercharge Your Software Supply Chain Security