Amid the ongoing war among Russia and Ukraine, govt, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea have been attacked as section of an active campaign that drops a formerly unseen, modular framework dubbed CommonMagic.
“Though the initial vector of compromise is unclear, the information of the following phase suggest the use of spear phishing or similar solutions,” Kaspersky stated in a new report.
The Russian cybersecurity company, which detected the assaults in Oct 2022, is tracking the action cluster less than the title “Lousy Magic.”
Attack chains entail the use of booby-trapped URLS pointing to a ZIP archive hosted on a malicious web server. The file, when opened, consists of a decoy doc and a malicious LNK file that culminates in the deployment of a backdoor named PowerMagic.
Written in PowerShell, PowerMagic establishes get in touch with with a remote server and executes arbitrary instructions, the benefits of which are exfiltrated to cloud expert services like Dropbox and Microsoft OneDrive.
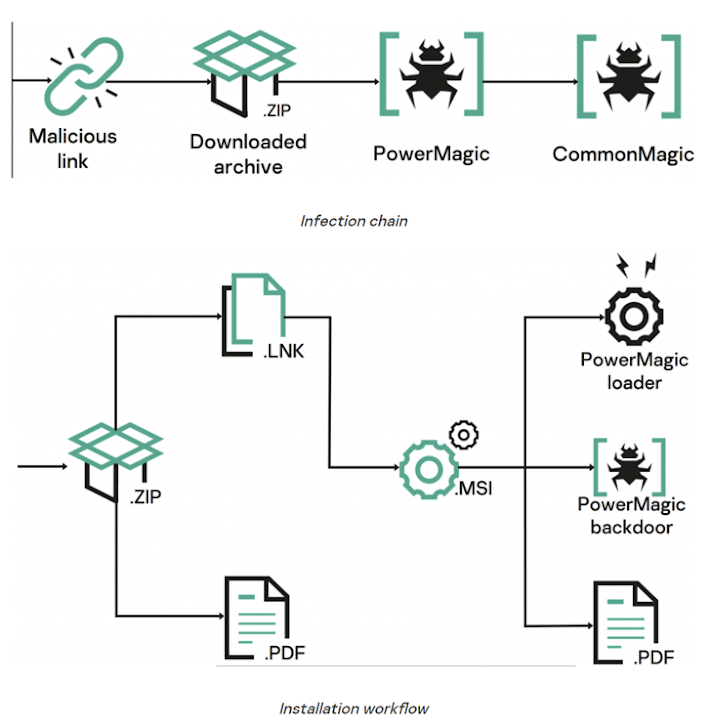
PowerMagic also serves as a conduit to supply the CommonMagic framework, a established of executable modules that are developed to have out distinct responsibilities these types of as interacting with the command-and-manage (C2) server, encrypting and decrypting C2 targeted traffic, and executing plugins.
Two of the plugins discovered so much occur with capabilities to capture screenshots each 3 seconds and acquire files of curiosity from related USB gadgets.
Kaspersky explained it uncovered no proof linking the procedure and its tooling to any identified danger actor or group.
Identified this short article intriguing? Follow us on Twitter and LinkedIn to read through extra special material we post.
Some parts of this article are sourced from:
thehackernews.com

 New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux Servers
New ShellBot DDoS Malware Variants Targeting Poorly Managed Linux Servers