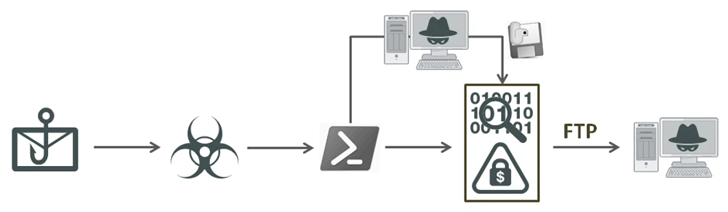
A new “all-in-a single” stealer malware named EvilExtractor (also spelled Evil Extractor) is getting marketed for sale for other risk actors to steal info and data files from Windows devices.
“It contains various modules that all function by means of an FTP service,” Fortinet FortiGuard Labs researcher Cara Lin explained. “It also includes setting examining and Anti-VM capabilities. Its main reason appears to be to be to steal browser information and data from compromised endpoints and then upload it to the attacker’s FTP server.”
The network security firm mentioned it has noticed a surge in assaults spreading the malware in the wild in March 2023, with a majority of the victims positioned in Europe and the U.S. Though promoted as an academic instrument, EvilExtractor has been adopted by menace actors for use as an data stealer.
Offered by an actor named Kodex on cybercrime community forums like Cracked because Oct 22, 2022, it is really continuously updated and packs in a variety of modules to siphon process metadata, passwords and cookies from numerous web browsers as perfectly as record keystrokes and even act as a ransomware by encrypting data files on the concentrate on system.
The malware is also explained to have been applied as portion of a phishing email marketing campaign detected by the firm on March 30, 2023. The emails lure recipients into launching an executable that masquerades as a PDF document under the pretext of confirming their “account particulars.”
The “Account_Facts.exe” binary is an obfuscated Python software developed to launch a .NET loader that utilizes a Foundation64-encoded PowerShell script to start EvilExtractor. The malware, besides collecting files, can also activate the webcam and capture screenshots.
“EvilExtractor is staying made use of as a complete details stealer with a number of malicious options, together with ransomware,” Lin said. “Its PowerShell script can elude detection in a .NET loader or PyArmor. Inside of a extremely brief time, its developer has current numerous capabilities and increased its security.”
The results appear as Secureworks Counter Danger Device (CTU) thorough a malvertising and Website positioning poisoning campaign made use of to deliver the Bumblebee malware loader by means of trojanized installers of legit software package.
Bumbleebee, documented very first a year in the past by Google’s Danger Analysis Team and Proofpoint, is a modular loader which is mainly propagating by way of phishing procedures. It really is suspected to be produced by actors related with the Conti ransomware operation as a substitution for BazarLoader.
Approaching WEBINARZero Belief + Deception: Discover How to Outsmart Attackers!
Uncover how Deception can detect advanced threats, prevent lateral movement, and increase your Zero Trust approach. Join our insightful webinar!
Preserve My Seat!
The use of Seo poisoning and malicious advertisements to redirect customers browsing for popular tools like ChatGPT, Cisco AnyConnect, Citrix Workspace, and Zoom to rogue web-sites hosting tainted installers has witnessed a spike in latest months after Microsoft began blocking macros by default from Office information downloaded from the internet.
In 1 incident described by the cybersecurity firm, the risk actor utilised the Bumblebee malware to receive an entry position and go laterally immediately after 3 hrs to deploy Cobalt Strike and authentic remote access program like AnyDesk and Dameware. The attack was eventually disrupted before it proceeded to the closing ransomware stage.
“To mitigate this and very similar threats, companies should guarantee that application installers and updates are only downloaded from acknowledged and trustworthy internet websites,” Secureworks reported. “People must not have privileges to put in software and run scripts on their personal computers.”
Identified this posting attention-grabbing? Stick to us on Twitter and LinkedIn to study additional distinctive material we post.
Some parts of this article are sourced from:
thehackernews.com


 Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers
Russian Hackers Suspected in Ongoing Exploitation of Unpatched PaperCut Servers