A medium-severity flaw has been identified in Synology’s DiskStation Manager (DSM) that could be exploited to decipher an administrator’s password and remotely hijack the account.
“Under some exceptional problems, an attacker could leak more than enough information to restore the seed of the pseudorandom range generator (PRNG), reconstruct the admin password, and remotely acquire over the admin account,” Claroty’s Sharon Brizinov claimed in a Tuesday report.
The flaw, assigned the identifier CVE-2023-2729, is rated 5.9 for severity on the CVSS scoring scale. The flaw was tackled by Synology as part of updates unveiled in June 2023.

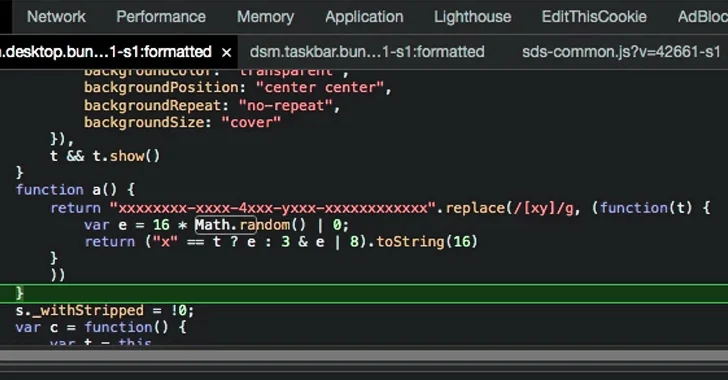
The problem is rooted in the point that the software uses a weak random amount generator that depends on the JavaScript Math.random() approach to programmatically construct the admin password for the network-attached storage (NAS) product.
Referred to as insecure randomness, it arises when a operate that can generate predictable values, or will not have more than enough entropy, is utilised as a source of randomness in a security context, enabling an attacker to crack the encryption and defeat the integrity of sensitive information and programs.
Thriving exploitation of these types of flaws, for that reason, could permit the risk actor to predict the created password and get accessibility to or else limited features.
“By leaking the output of a few Math.Random() produced quantities, we were able to reconstruct the seed for the PRNG and use it to brute-force the admin password,” Brizinov explained. “At last we were being equipped to use the password to login to the admin account (just after enabling it).”

The attack, on the other hand, hinges on an attacker effectively extracting a couple GUIDs that are also created working with the very same process for the duration of the setup procedure to be in a position to reconstruct the seed phrase for the pseudorandom amount generator (PRNG).
“In a actual existence scenario the attacker will 1st need to leak the aforementioned GUIDs, brute power the Math.Random point out, and obtain the admin password,” Brizinov said. “Even immediately after doing so, by default the builtin admin user account is disabled and most buyers would not permit it.”
“All over again, it can be crucial to bear in mind that Math.random() does not deliver cryptographically secure random figures. Do not use them for just about anything associated to security. Use the Web Crypto API as an alternative, and extra specifically the window.crypto.getRandomValues() technique.”
Located this posting exciting? Abide by us on Twitter and LinkedIn to examine much more distinctive articles we submit.
Some parts of this article are sourced from:
thehackernews.com

 D-Link Confirms Data Breach: Employee Falls Victim to Phishing Attack
D-Link Confirms Data Breach: Employee Falls Victim to Phishing Attack