Almost 2,000 Citrix NetScaler cases have been compromised with a backdoor by weaponizing a not long ago disclosed critical security vulnerability as aspect of a big-scale attack.
“An adversary appears to have exploited CVE-2023-3519 in an automatic manner, placing web shells on vulnerable NetScalers to obtain persistent obtain,” NCC Team stated in an advisory introduced Tuesday.
“The adversary can execute arbitrary commands with this webshell, even when a NetScaler is patched and/or rebooted.”
CVE-2023-3519 refers to a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could lead to unauthenticated remote code execution. It was patched by Citrix previous month.

The development arrives a week following the Shadowserver Basis mentioned it recognized near to 7,000 susceptible, unpatched NetScaler ADC and Gateway circumstances on the net and the flaw is being abused to drop PHP web shells on susceptible servers for remote entry.
A comply with-up evaluation by NCC Team has now disclosed that 1,828 NetScaler servers remain backdoored, out of which approximately 1,248 are by now patched in opposition to the flaw.
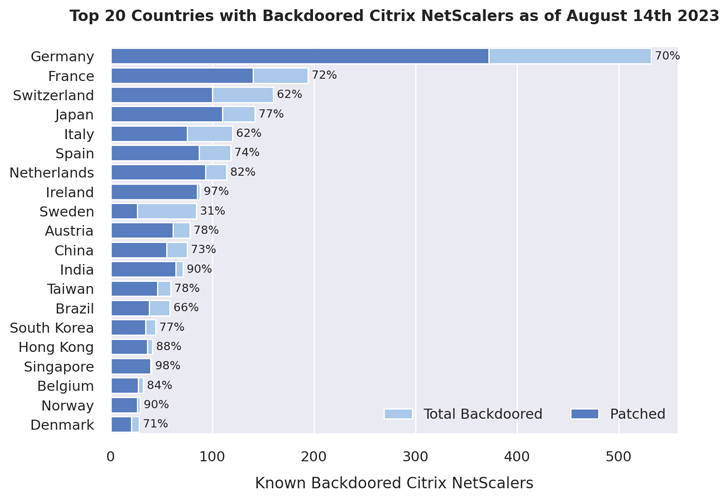
“This suggests that whilst most administrators were being informed of the vulnerability and have because patched their NetScalers to a non-vulnerable version, they have not been (effectively) checked for indicators of profitable exploitation,” the enterprise explained.
In whole, as numerous as 2,491 web shells have been found throughout 1,952 distinct NetScaler appliances. A bulk of the compromised circumstances are situated in Germany, France, Switzerland, Japan, Italy, Spain, the Netherlands, Eire, Sweden, and Austria.

The European emphasis apart, one more noteworthy component is that while Canada, Russia, and the U.S. had countless numbers of susceptible NetScaler servers late previous thirty day period, no web shells had been discovered on any of them.
The mass exploitation marketing campaign is believed to have compromised 6.3% of the 31,127 NetScaler instances that ended up vulnerable to CVE-2023-3519 as of July 21, 2023.
The disclosure also arrives as Mandiant has produced an open-supply tool to aid companies scan their Citrix appliances for proof of submit-exploitation activity related to CVE-2023-3519.
Found this article interesting? Follow us on Twitter and LinkedIn to examine far more exclusive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn
Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn