The North Korean threat actor recognized as Kimsuky has been noticed targeting analysis institutes in South Korea as part of a spear-phishing campaign with the best target of distributing backdoors on compromised techniques.
“The menace actor eventually makes use of a backdoor to steal data and execute commands,” the AhnLab Security Crisis Reaction Middle (ASEC) reported in an investigation posted last week.
The attack chains commence with an import declaration entice that is basically a malicious JSE file made up of an obfuscated PowerShell script, a Foundation64-encoded payload, and a decoy PDF doc.
The future phase entails opening the PDF file as a diversionary tactic, though the PowerShell script is executed in the history to start the backdoor.
The malware, for its component, is configured to accumulate network info and other applicable information (i.e., host identify, user identify, and functioning program variation) and transmit the encoded particulars to a distant server.
It is really also capable of running commands, executing more payloads, and terminating by itself, turning it into a backdoor for remote accessibility to the contaminated host.
Impending WEBINAR Cracking the Code: Study How Cyber Attackers Exploit Human Psychology
Ever puzzled why social engineering is so helpful? Dive deep into the psychology of cyber attackers in our impending webinar.
Be a part of Now
Kimsuky, active since at the very least 2012, started off targeting South Korean authorities entities, imagine tanks, and men and women discovered as professionals in several fields, right before increasing its victimology footprint to encompass Europe, Russia, and the U.S.
Before this thirty day period, the U.S. Treasury Department sanctioned Kimsuky for gathering intelligence to aid North Korea’s strategic objectives, which includes geopolitical activities, international policy, and diplomatic endeavours.
“Kimsuky has centered its intelligence selection things to do on foreign plan and national security issues related to the Korean peninsula, nuclear plan, and sanctions,” cybersecurity agency ThreatMon observed in a the latest report.
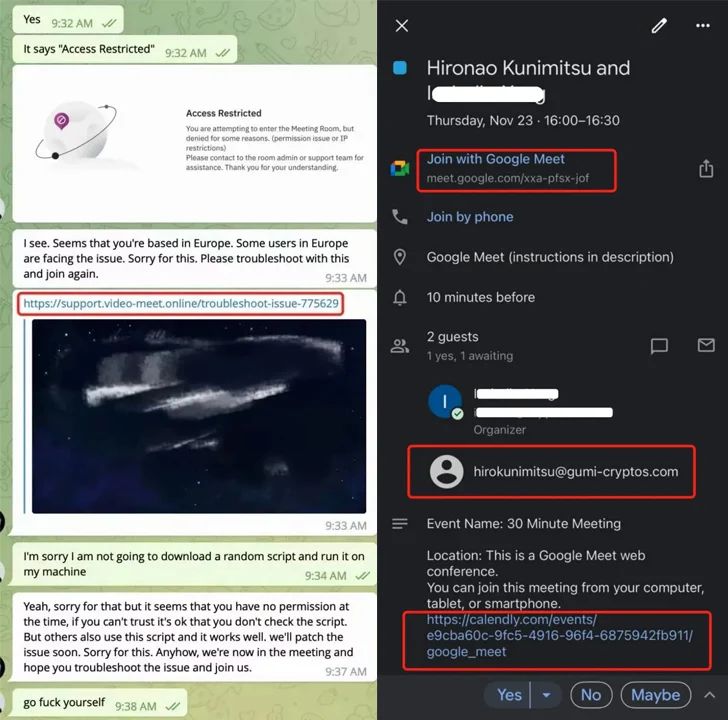
The condition-sponsored team has also been noticed leveraging booby-trapped URLs that, when clicked, obtain a bogus ZIP archive masquerading as an update for the Chrome browser to deploy a malicious VBScript from Google Travel that employs the cloud storage as a conduit for information exfiltration and command-and-regulate (C2).
Lazarus Group Goes Phishing on Telegram
The development comes as blockchain security corporation SlowMist implicated the notorious North Korea-backed outfit named the Lazarus Group in a common phishing marketing campaign on Telegram concentrating on the cryptocurrency sector.
“Additional a short while ago, these hackers have escalated their ways by posing as highly regarded investment decision institutions to execute phishing ripoffs from numerous cryptocurrency undertaking teams,” the Singapore-centered business said.

After developing rapport, the targets are deceived into downloading a malicious script beneath the guise of sharing an on line assembly website link that facilitates crypto theft.
It also follows a report from the Seoul Metropolitan Law enforcement Company (SMPA) that accused the Lazarus sub-cluster codenamed Andariel of stealing specialized facts about anti-plane weapon methods from domestic protection corporations and laundering ransomware proceeds again to North Korea.
It is believed that more than 250 data files amounting to 1.2 terabytes have been stolen in the attacks. To cover up the tracks, the adversary is mentioned to have applied servers from a nearby organization that “rents servers to subscribers with unclear identities” as an entry level.
In addition, the group extorted 470 million won ($356,000) well worth of bitcoin from 3 South Korean corporations in ransomware assaults and laundered them through virtual asset exchanges such as Bithumb and Binance. It’s worth noting that Andariel has been joined to the deployment of Maui ransomware in the past.
Located this post exciting? Adhere to us on Twitter and LinkedIn to browse a lot more special content material we publish.
Some parts of this article are sourced from:
thehackernews.com


 Ransomware-as-a-Service: The Growing Threat You Can’t Ignore
Ransomware-as-a-Service: The Growing Threat You Can’t Ignore