The risk actor acknowledged as Muddled Libra has been noticed actively targeting software package-as-a-company (SaaS) programs and cloud services provider (CSP) environments in a bid to exfiltrate delicate info.
“Companies typically keep a wide variety of information in SaaS programs and use solutions from CSPs,” Palo Alto Networks Unit 42 reported in a report released past week.
“The danger actors have started trying to leverage some of this knowledge to support with their attack development, and to use for extortion when seeking to monetize their operate.”
Muddled Libra, also referred to as Starfraud, UNC3944, Scatter Swine, and Scattered Spider, is a infamous cybercriminal team that has leveraged complex social engineering techniques to attain original accessibility to target networks.
“Scattered Spider danger actors have historically evaded detection on goal networks by making use of residing off the land procedures and allowlisted programs to navigate target networks, as perfectly as commonly modifying their TTPs,” the U.S. govt reported in an advisory late previous year.

The attackers also have a background of monetizing access to target networks in several means, together with extortion enabled by ransomware and data theft.
Unit 42 earlier advised The Hacker News that the moniker “Muddled Libra” will come from the “baffling muddled landscape” affiliated with the 0ktapus phishing kit, which has been place to use by other danger actors to phase credential harvesting assaults.
A crucial component of the menace actor’s tactical evolution is the use of reconnaissance approaches to discover administrative end users to focus on when posing as helpdesk team employing phone calls to get their passwords.
The recon stage also extends to Muddled Libra, which performs substantial study to come across information about the programs and the cloud provider providers made use of by the concentrate on organizations.
“The Okta cross-tenant impersonation attacks that happened from late July to early August 2023, the place Muddled Libra bypassed IAM constraints, display how the team exploits Okta to entry SaaS purposes and an organization’s numerous CSP environments,” security researcher Margaret Zimmermann defined.
The details acquired at this phase serves as a stepping stone for conducting lateral movement, abusing the admin qualifications to accessibility one indication-on (SSO) portals to acquire speedy accessibility to SaaS applications and cloud infrastructure.
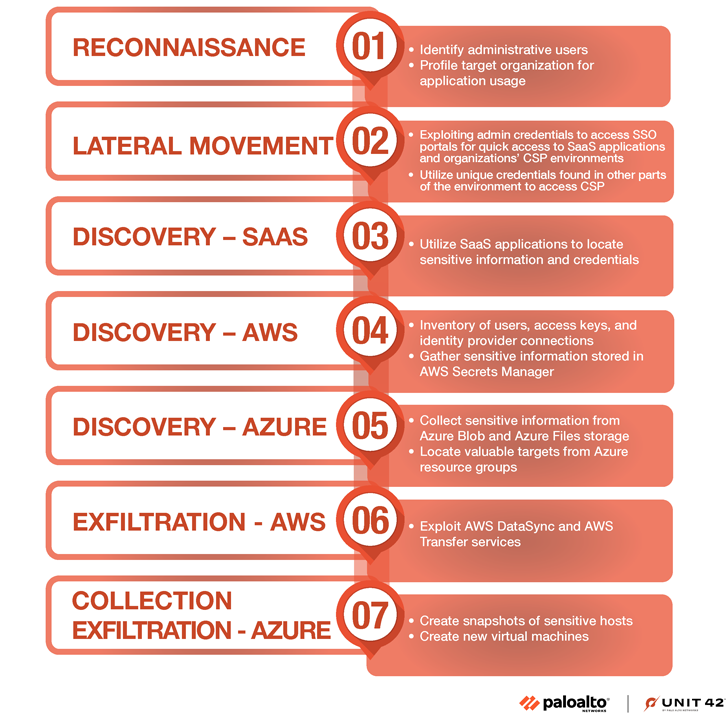
In the party SSO is not integrated into a target’s CSP, Muddled Libra undertakes broad discovery routines to uncover the CSP qualifications, probably stored in unsecured places, to fulfill their goals.
The facts saved with SaaS purposes are also employed to glean specifics about the infected environment, capturing as quite a few qualifications as probable to widen the scope of the breach by means of privilege escalation and lateral movement.
“A substantial portion of Muddled Libra’s strategies involve collecting intelligence and knowledge,” Zimmermann stated.

“Attackers then use this to create new vectors for lateral movement in an surroundings. Companies shop a assortment of info inside their special CSP environments, hence creating these centralized locations a prime concentrate on for Muddled Libra.”
These steps specially single out Amazon Web Providers (AWS) and Microsoft Azure, concentrating on companies like AWS IAM, Amazon Straightforward Storage Service (S3), AWS Insider secrets Supervisor, Azure storage account access keys, Azure Blob Storage, and Azure Data files to extract suitable knowledge.
Details exfiltration to an exterior entity is realized by abusing reputable CSP expert services and capabilities. This encompasses applications like AWS DataSync, AWS Transfer, and a system called snapshot, the latter of which makes it doable to shift info out of an Azure atmosphere by staging the stolen info in a virtual equipment.
Muddled Libra’s tactical shift calls for businesses to secure their identification portals with strong secondary authentication protections like hardware tokens or biometrics.
“By growing their techniques to consist of SaaS applications and cloud environments, the evolution of Muddled Libra’s methodology demonstrates the multidimensionality of cyberattacks in the modern-day threat landscape,” Zimmermann concluded. “The use of cloud environments to acquire huge amounts of information and speedily exfiltrate it poses new troubles to defenders.”
Uncovered this report interesting? Follow us on Twitter and LinkedIn to browse a lot more unique written content we article.
Some parts of this article are sourced from:
thehackernews.com


 Timing is Everything: The Role of Just-in-Time Privileged Access in Security Evolution
Timing is Everything: The Role of Just-in-Time Privileged Access in Security Evolution