Cybersecurity researchers have noticed a phishing attack distributing the Far more_eggs malware by masquerading it as a resume, a technique initially detected extra than two a long time back.
The attack, which was unsuccessful, focused an unnamed enterprise in the industrial companies industry in May perhaps 2024, Canadian cybersecurity business eSentire disclosed last 7 days.
“Especially, the focused specific was a recruiter that was deceived by the menace actor into wondering they have been a career applicant and lured them to their web site to obtain the loader,” it reported.
A lot more_eggs, thought to be the work of a menace actor identified as the Golden Chickens (aka Venom Spider), is a modular backdoor that’s capable of harvesting delicate information. It is really available to other legal actors below a Malware-as-a-Services (MaaS) product.
Very last calendar year, eSentire unmasked the actual-planet identities of two men and women – Chuck from Montreal and Jack – who are explained to be operating the procedure.
The newest attack chain entails the malicious actors responding to LinkedIn work postings with a url to a bogus resume download internet site that benefits in the download of a malicious Windows Shortcut file (LNK).

It is really really worth noting that previous Far more_eggs action has specific experts on LinkedIn with weaponized occupation offers to trick them into downloading the malware.
“Navigating to the exact URL days afterwards outcomes in the individual’s resume in plain HTML, with no indicator of a redirect or download,” eSentire noted.
The LNK file is then made use of to retrieve a malicious DLL by leveraging a respectable Microsoft method identified as ie4uinit.exe, after which the library is executed applying regsvr32.exe to set up persistence, acquire information about the contaminated host, and drop more payloads, which includes the JavaScript-dependent A lot more_eggs backdoor.
“Additional_eggs campaigns are still active and their operators continue to use social engineering techniques this kind of as posing to be career candidates who are hunting to implement for a particular job, and luring victims (exclusively recruiters) to obtain their malware,” eSentire explained.
“Furthermore, campaigns like much more_eggs, which use the MaaS featuring appear to be sparse and selective in comparison to common malspam distribution networks.”
The advancement comes as the cybersecurity agency also revealed particulars of a push-by obtain campaign that employs phony web sites for the KMSPico Windows activator software to distribute Vidar Stealer.
“The kmspico[.]ws web page is hosted guiding Cloudflare Turnstile and demands human input (moving into a code) to obtain the ultimate ZIP offer,” eSentire pointed out. “These methods are unusual for a reputable application obtain web site and are performed to conceal the site and remaining payload from automated web crawlers.”
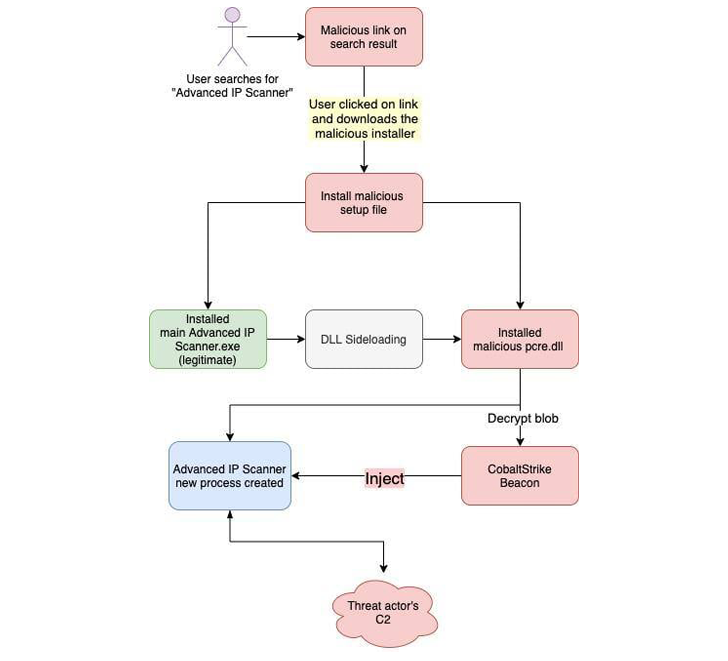
Very similar social engineering strategies have also established up lookalike web-sites impersonating legit computer software like Innovative IP Scanner to deploy Cobalt Strike, Trustwave SpiderLabs reported previous week.
It also follows the emergence of a new phishing kit referred to as V3B that has been put to use to single out banking clients in the European Union with the purpose of stealing credentials and a single-time passwords (OTPs).

The kit, presented for $130-$450 for each thirty day period via a Phishing-as-a-Service (PhaaS) design by way of the dark web and a focused Telegram channel, is explained to have been active considering the fact that March 2023. It is designed to assist about 54 banking institutions situated in Austria, Belgium, Finland, France, Germany, Greece, Eire, Italy, Luxembourg, and the Netherlands.
The most significant component of V3B is that it attributes custom made and localized templates to mimic many authentication and verification processes frequent to on line banking and e-commerce techniques in the location.
It also arrives with state-of-the-art abilities to interact with victims in actual-time and get their OTP and PhotoTAN codes, as well as execute a QR code login jacking (aka QRLJacking) attack on products and services these kinds of as WhatsApp that make it possible for indication-in via QR codes.
“They have considering the fact that constructed a customer base focused on targeting European money institutions,” Resecurity said. “Currently, it is estimated that hundreds of cybercriminals are applying this kit to dedicate fraud, leaving victims with vacant lender accounts.”
Found this posting exciting? Follow us on Twitter and LinkedIn to go through extra exceptional material we post.
Some parts of this article are sourced from:
thehackernews.com


 Cybersecurity CPEs: Unraveling the What, Why & How
Cybersecurity CPEs: Unraveling the What, Why & How