Cybersecurity scientists have learned multiple campaigns focusing on Docker Hub by planting tens of millions of malicious “imageless” containers around the earlier 5 several years, the moment all over again underscoring how open-source registries could pave the way for source chain assaults.
“In excess of four million of the repositories in Docker Hub are imageless and have no information besides for the repository documentation,” JFrog security researcher Andrey Polkovnichenko reported in a report shared with The Hacker News.
What is actually a lot more, the documentation has no connection in any respect to the container. Instead, it’s a web web page that is developed to entice customers into viewing phishing or malware-hosting internet sites.

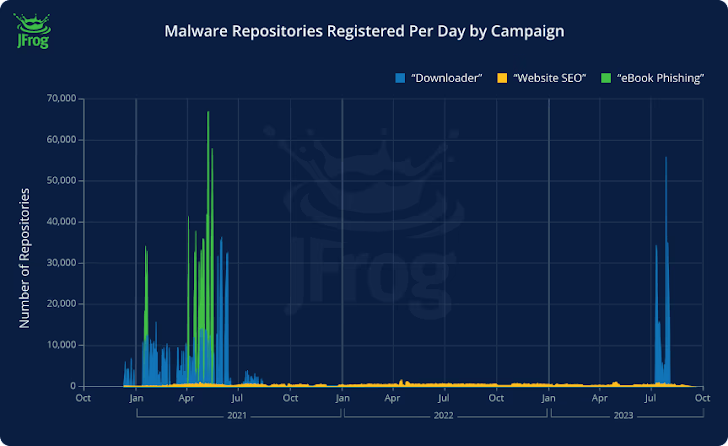
Of the 4.79 million imageless Docker Hub repositories uncovered, 3.2 million of them are said to have been made use of as landing webpages to redirect unsuspecting consumers to fraudulent web pages as part of 3 broad campaigns –
- Downloader (repositories made in the first fifty percent of 2021 and September 2023), which advertises inbound links to purported pirated content material or cheats for online video online games but possibly immediately backlinks to destructive resources or a respectable a single that, in transform, includes JavaScript code that redirects to the malicious payload right after 500 milliseconds.
- E-book phishing (repositories established in mid-2021), which redirects consumers exploring for e-textbooks to a website (“rd.lesac.ru”) that, in convert, urges them to enter their money information and facts to download the e-e book.
- Website (hundreds of repositories made daily from April 2021 to October 2023), which incorporates a website link to an on the web diary-hosting company identified as Penzu in some cases.
The payload delivered as part of the downloader campaign is developed to call a command-and-management (C2) server and transmit process metadata, pursuing which the server responds with a url to cracked software package.
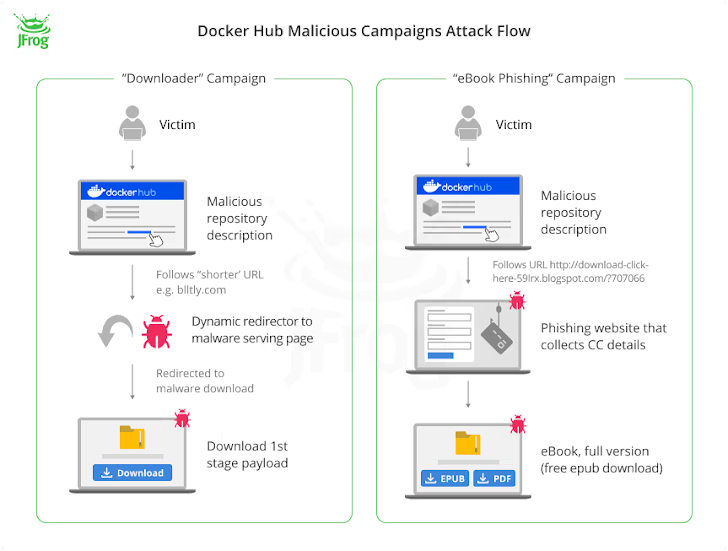
On the other hand, the specific objective of the website cluster is at the moment unclear, with the marketing campaign also propagated on web sites that have a lax information moderation coverage.

“The most concerning component of these a few strategies is that there is not a lot that users can do to safeguard themselves at the outset, other than performing exercises caution,” Shachar Menashe, senior director of security research at JFrog, said in a assertion shared with The Hacker Information.
“We are effectively looking at a malware playground that in some conditions has been a few several years in the generating. These danger actors are extremely inspired and are hiding guiding the credibility of the Docker Hub identify to lure victims.”
With threat actors taking painstaking attempts to poison properly regarded utilities, as evidenced in the case of the XZ Utils compromise, it’s imperative that developers physical exercise warning when it arrives to downloading offers from open-source ecosystems/
“As Murphy’s Law implies, if something can be exploited by malware developers, it inevitably will be, so we be expecting that these campaigns can be discovered in additional repositories than just Docker Hub,” Menashe mentioned.
Observed this article exciting? Adhere to us on Twitter and LinkedIn to read through extra exclusive information we put up.
Some parts of this article are sourced from:
thehackernews.com


 U.S. Government Releases New AI Security Guidelines for Critical Infrastructure
U.S. Government Releases New AI Security Guidelines for Critical Infrastructure