The Midnight Blizzard and Cloudflare-Atlassian cybersecurity incidents raised alarms about the vulnerabilities inherent in significant SaaS platforms. These incidents illustrate the stakes involved in SaaS breaches — safeguarding the integrity of SaaS applications and their delicate info is critical but is not quick. Frequent danger vectors these as innovative spear-phishing, misconfigurations and vulnerabilities in 3rd-occasion application integrations reveal the sophisticated security problems going through IT methods.
In the circumstance of Midnight Blizzard, password spraying towards a test setting was the original attack vector. For Cloudflare-Atlassian, threat actors initiated the attack via compromised OAuth tokens from a prior breach at Okta, a SaaS identification security service provider.
What Just Transpired?
Microsoft Midnight Blizzard Breach
Microsoft was qualified by the Russian “Midnight Blizzard” hackers (also recognised as Nobelium, APT29, or Cozy Bear) who are joined to the SVR, the Kremlin’s international intelligence assistance unit.
In the Microsoft breach, the threat actors:
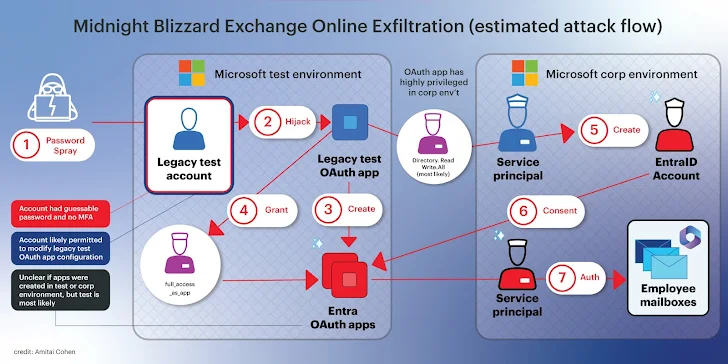 Recreation of illustration by Amitai Cohen
Recreation of illustration by Amitai Cohen
Cloudflare-Atlassian Breach
On Thanksgiving Working day, November 23, 2023, Cloudflare’s Atlassian systems were also compromised by a nation-point out attack.
SaaS Security GuideCan Your Security Group Watch 3rd Get together Apps? 60% of Groups Are unable to
Assume your SaaS security is major-notch? Appomni surveyed over 600 worldwide security practitioners, and 79% of gurus felt the exact same – nevertheless they faced cybersecurity incidents! Dive into the insights of the AppOmni 2023 Report.
Study How You Can
Risk Actors Ever more Goal SaaS
These breaches are component of a broader pattern of country-point out actors focusing on SaaS provider providers, which include but not restricted to espionage and intelligence accumulating. Midnight Blizzard formerly engaged in important cyber operations, which includes the 2021 SolarWinds attack.
These incidents underscore the value of constant monitoring of your SaaS environments and the ongoing risk posed by innovative cyber adversaries focusing on critical infrastructure and operational tech stack. They also emphasize important vulnerabilities related to SaaS id administration and the requirement for stringent 3rd-social gathering app risk management tactics.
Attackers use popular strategies, methods and strategies (TTPs) to breach SaaS providers by the pursuing eliminate chain:
Breaking the SaaS Get rid of Chain
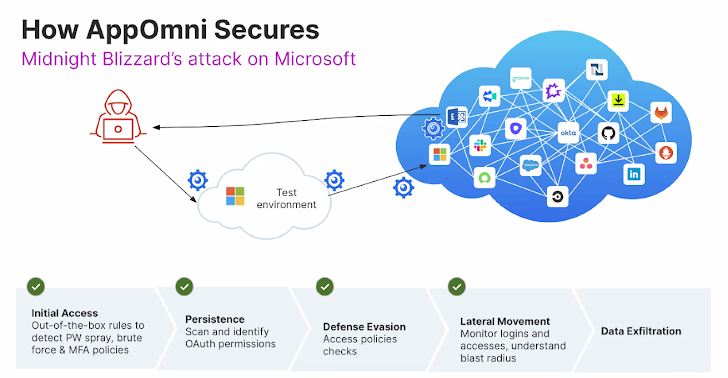
Just one powerful way to crack the destroy chain early is with continual monitoring, granular policy enforcement, and proactive lifecycle management around your SaaS environments. A SaaS Security Posture Management (SSPM) platform like AppOmni can enable with detecting and alerting on:
- Preliminary Entry: Out-of-the-box guidelines to detect credential compromise, which includes password spraying, brute power attacks, and unenforced MFA policies
- Persistence: Scan and discover OAuth permissions and detect OAuth hijacking
- Protection Evasion: Access plan checks, detect if a new id company (IdP) is produced, detect permission modifications.
- Lateral Motion: Keep track of logins and privileged access, detect harmful combos, and have an understanding of the blast radius of a potentially compromised account
Be aware: This expertly contributed post is created by Beverly Nevalga, AppOmni.
Uncovered this posting attention-grabbing? This write-up is a contributed piece from a single of our valued companions. Stick to us on Twitter and LinkedIn to study extra distinctive information we publish.
Some parts of this article are sourced from:
thehackernews.com


 Ivanti Vulnerability Exploited to Install ‘DSLog’ Backdoor on 670+ IT Infrastructures
Ivanti Vulnerability Exploited to Install ‘DSLog’ Backdoor on 670+ IT Infrastructures