Malicious ads served inside of Microsoft Bing’s synthetic intelligence (AI) chatbot are currently being used to distribute malware when searching for well-liked applications.
The conclusions come from Malwarebytes, which unveiled that unsuspecting customers can be tricked into browsing booby-trapped web sites and installing malware straight from Bing Chat discussions.
Released by Microsoft in February 2023, Bing Chat is an interactive look for working experience that’s powered by OpenAI’s substantial language design called GPT-4. A thirty day period later on, the tech giant commenced discovering positioning adverts in the conversations.
But the move has also opened the doors for danger actors who resort to malvertising techniques and propagate malware.
“Adverts can be inserted into a Bing Chat discussion in various methods,” Jérôme Segura, director of danger intelligence at Malwarebytes, mentioned. “One of those is when a person hovers above a url and an advertisement is shown to start with prior to the natural and organic end result.”

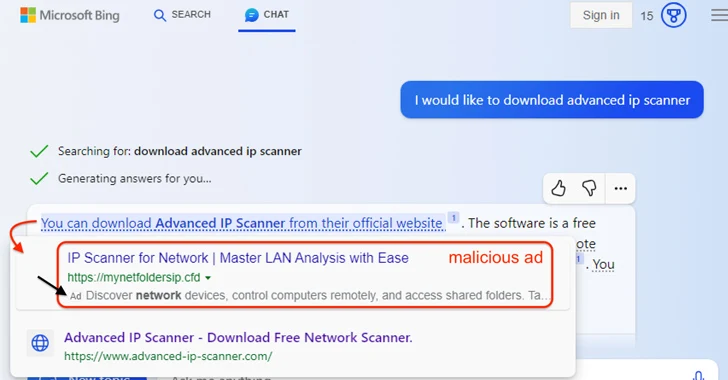
In an illustration highlighted by the cybersecurity seller, a Bing Chat query to download a reputable software termed Superior IP Scanner returned a hyperlink that, when hovered, shown a destructive advert pointing to a fraudulent link right before the formal website hosting the tool.
Clicking the hyperlink normally takes the user to a targeted visitors way procedure (TDS) that fingerprints and decides if the request is really originating from a real human (as opposed to a bot, crawler, or sandbox), right before taking them to a decoy website page made up of the rogue installer.
The installer is configured to operate a Visual Primary Script that beacons to an external server with the likely intention of obtaining the subsequent-phase payload. The actual character of the malware shipped is presently unfamiliar.
A noteworthy facet of the campaign is that the danger actor managed to infiltrate the advert account of a respectable Australian enterprise and create the advertisements.
“Risk actors continue on to leverage research advertisements to redirect customers to malicious sites hosting malware,” Segura said. “With convincing landing webpages, victims can conveniently be tricked into downloading malware and be none the wiser.”
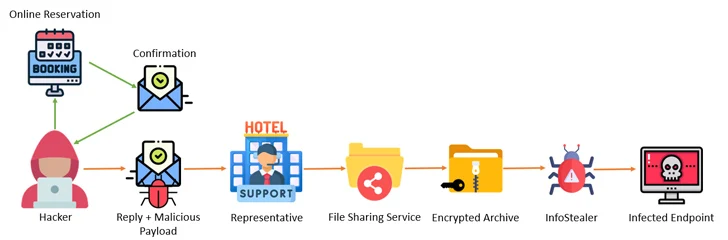
The revelation arrives as Akamai and Perception Place uncovered a multi-phase campaign that involves attacking the methods of resorts, booking internet sites, and travel agencies with details stealer malware and then leveraging the access to the accounts to go right after financial data belonging to customers applying phony reservation web pages.
“The attacker, masquerading as the resort, reaches out to the shopper by the booking site, urging the purchaser to ‘re-verify their credit card,’ then steals the customer’s information,” Akamai researcher Shiran Guez claimed, noting how the assaults prey on the victim’s perception of urgency to pull off the operation.
Impending WEBINARFight AI with AI — Battling Cyber Threats with Upcoming-Gen AI Tools
Ready to tackle new AI-pushed cybersecurity troubles? Be part of our insightful webinar with Zscaler to handle the increasing danger of generative AI in cybersecurity.
Supercharge Your Abilities
Cofense, in a report published this week, claimed the hospitality sector has been at the getting finish of a “perfectly-crafted and revolutionary social engineering attack” which is intended to supply stealer malware this kind of as Lumma Stealer, RedLine Stealer, Stealc, Spidey Bot, and Vidar.
“As of now, the marketing campaign only targets the hospitality sector, largely concentrating on luxurious resort chains and resorts, and works by using lures relative to that sector these as reserving requests, reservation modifications, and particular requests,” Cofense stated.
“The lures for the two the reconnaissance and phishing emails match accordingly and are perfectly believed out.”
The organization phishing menace management business said it also observed malicious HTML attachments meant to have out Browser-in-the-Browser (BitB) attacks by serving seemingly innocuous pop-up windows that entice email recipients into delivering their Microsoft qualifications.
The discoveries are a signal that danger actors are constantly obtaining new methods to infiltrate unwitting targets. Users should keep away from clicking on unsolicited backlinks, even if they search reputable, be suspicious of urgent or threatening messages asking for rapid motion, and test URLs for indicators of deception.
Uncovered this report exciting? Comply with us on Twitter and LinkedIn to examine more unique content we submit.
Some parts of this article are sourced from:
thehackernews.com

 Progress Software Releases Urgent Hotfixes for Multiple Security Flaws in WS_FTP Server
Progress Software Releases Urgent Hotfixes for Multiple Security Flaws in WS_FTP Server