Microsoft has disclosed that it really is detected a spike in credential-thieving attacks performed by the Russian point out-affiliated hacker group known as Midnight Blizzard.
The intrusions, which manufactured use of household proxy companies to obfuscate the resource IP deal with of the attacks, target governments, IT assistance providers, NGOs, defense, and critical producing sectors, the tech giant’s danger intelligence workforce claimed.
Midnight Blizzard, formerly recognised as Nobelium, is also tracked under the monikers APT29, Cozy Bear, Iron Hemlock, and The Dukes.
The team, which drew throughout the world awareness for the SolarWinds offer chain compromise in December 2020, has ongoing to rely on unseen tooling in its focused assaults aimed at foreign ministries and diplomatic entities.
It is really a indication of how established they are to continue to keep their operations up and working regardless of currently being uncovered, which tends to make them a specifically formidable actor in the espionage place.

“These credential attacks use a variety of password spray, brute-drive, and token theft tactics,” Microsoft mentioned in a sequence of tweets, including the actor “also conducted session replay attacks to gain first accessibility to cloud resources leveraging stolen sessions likely obtained by means of illicit sale.”
The tech giant even more named out APT29 for its use of household proxy products and services to route malicious website traffic in an endeavor to obfuscate connections manufactured making use of compromised qualifications.
“The danger actor likely utilised these IP addresses for incredibly brief intervals, which could make scoping and remediation tough,” the Windows makers explained.
The development arrives as Recorded Upcoming in depth a new spear-phishing campaign orchestrated by APT28 (aka BlueDelta, Forest Blizzard, FROZENLAKE, Iron Twilight, and Extravagant Bear) concentrating on federal government and navy entities in Ukraine considering that November 2021.
The attacks leveraged e-mails bearing attachments exploiting many vulnerabilities in the open-source Roundcube webmail software (CVE-2020-12641, CVE-2020-35730, and CVE-2021-44026) to perform reconnaissance and data gathering.
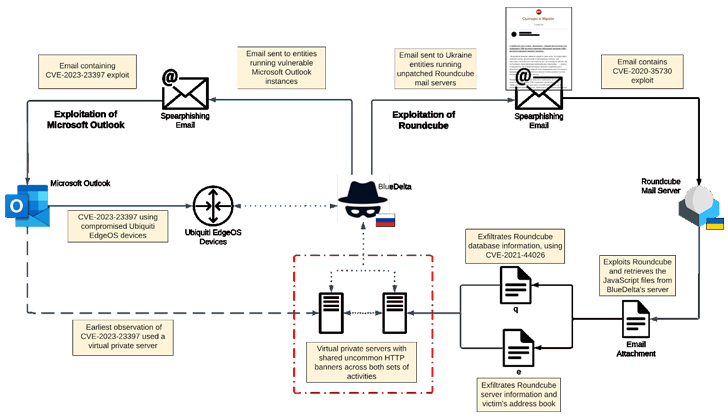
A prosperous breach enabled the Russian armed service intelligence hackers to deploy rogue JavaScript malware that redirected the incoming e-mails of qualified folks to an email tackle less than the attackers’ handle as properly as steal their speak to lists.
“The campaign displayed a superior amount of preparedness, swiftly weaponizing news content material into lures to exploit recipients,” the cybersecurity business reported. “The spear-phishing email messages contained news themes associated to Ukraine, with subject traces and content mirroring genuine media sources.”

Much more importantly, the activity is said to dovetail with one more set of assaults weaponizing a then-zero-day flaw in Microsoft Outlook (CVE-2023-23397) that Microsoft disclosed as used in “minimal qualified attacks” versus European organizations.
The privilege escalation vulnerability was tackled as component of Patch Tuesday updates rolled out in March 2023.
The conclusions demonstrate Russian danger actors’ persistent initiatives in harvesting worthwhile intelligence on a variety of entities in Ukraine and across Europe, primarily following the total-scale invasion of the region in February 2022.
The cyberwarfare operations aimed at Ukrainian targets have been notably marked by the widespread deployment of wiper malware developed to delete and wipe out information, turning it into one particular of the earliest cases of substantial-scale hybrid conflict.
“BlueDelta will almost unquestionably proceed to prioritize concentrating on Ukrainian authorities and private sector businesses to assist wider Russian military initiatives,” Recorded Long term concluded.
Uncovered this short article intriguing? Stick to us on Twitter and LinkedIn to read additional special material we write-up.
Some parts of this article are sourced from:
thehackernews.com

 Chinese Hackers Using Never-Before-Seen Tactics for Critical Infrastructure Attacks
Chinese Hackers Using Never-Before-Seen Tactics for Critical Infrastructure Attacks