Microsoft on Wednesday took the lid off a “novel and distinctive Russian menace actor,” which it said is connected to the Typical Workers Primary Intelligence Directorate (GRU) and has a “fairly very low good results price.”
The tech giant’s Threat Intelligence team, which was formerly monitoring the team less than its emerging moniker DEV-0586, has graduated it to a named actor dubbed Cadet Blizzard.
“Cadet Blizzard seeks to perform disruption, destruction, and facts collection, using what ever means are available and occasionally acting in a haphazard style,” the organization reported.
“While the group carries substantial risk because of to their destructive exercise, they show up to work with a reduced degree of operational security than that of longstanding and innovative Russian teams these types of as Seashell Blizzard and Forest Blizzard.”

Cadet Blizzard 1st came to gentle in January 2022 in link with destructive cyber exercise focusing on Ukraine working with a novel wiper malware referred to as WhisperGate (aka PAYWIPE) in the months main to Russia’s armed service invasion of the country.
The condition-sponsored actor, per Microsoft, has a observe file of orchestrating damaging assaults, espionage, and data functions aimed at entities located in Ukraine, Europe, Central Asia, and, periodically, Latin The united states.
Suspected to have been operational in some potential given that at least 2020, intrusions mounted by Cadet Blizzard have predominantly focused on government agencies, legislation enforcement, non-revenue and non-governmental businesses, IT support companies, and emergency products and services.
“Cadet Blizzard is active seven times a 7 days and has executed its operations in the course of its main targets’ off-business enterprise several hours when its activity is considerably less probably to be detected,” Microsoft’s Tom Burt claimed. “In addition to Ukraine, it also focuses on NATO member states associated in offering armed service aid to Ukraine.”
It can be well worth noting that Cadet Blizzard also overlaps with groups monitored by the broader cybersecurity community below the names Ember Bear (CrowdStrike), FROZENVISTA (Google TAG), Nodaria (Symantec), TA471 (Proofpoint), UAC-0056 (CERT-UA), and UNC2589 (Google Mandiant).
Besides WhisperGate, the hacking crew is acknowledged to leverage a raft of weapons for its arsenal, together with SaintBot, OutSteel, GraphSteel, GrimPlant, and a lot more just lately, Graphiron. Microsoft has attributed SaintBot and OutSteel to a linked activity cluster labeled Storm-0587.
Impending WEBINAR🔐 Mastering API Security: Comprehending Your True Attack Floor
Uncover the untapped vulnerabilities in your API ecosystem and get proactive steps towards ironclad security. Be a part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:just afterexhibit:inline-block.check out_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px stable #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-best-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-bottom-appropriate-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-dimensions:13pxmargin:20px 0font-fat:600letter-spacing:.6pxcolor:#596cec.wn-label:soon afterwidth:50pxheight:6pxcontent:”border-prime:2px solid #d9deffmargin: 8px.wn-titlefont-dimension:21pxpadding:10px 0font-fat:900textual content-align:leftline-height:33px.wn-descriptiontext-align:leftfont-size:15.6pxline-height:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-color:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-weight:500letter-spacing:.2px
“Cadet Blizzard is also connected to the defacements of a number of Ukrainian corporation web sites, as perfectly as numerous functions, such as the hack-and-leak forum known as ‘Free Civilian,'” Microsoft added.
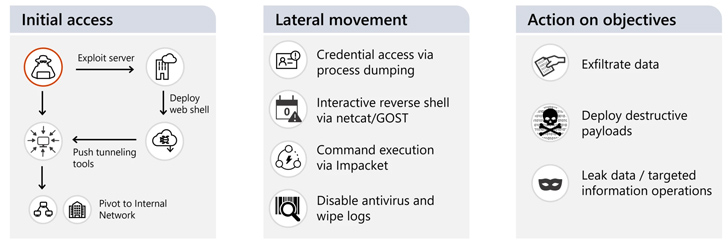
Other notable tradecraft involves the use of dwelling-off-the-land (LotL) procedures post gaining initial obtain to attain lateral movement, gather qualifications and other facts, and deploy equipment to facilitate protection evasion and persistence.
The cyber assaults, for their component, are achieved by way of the exploitation of recognised flaws in uncovered web servers (e.g., Atlassian Confluence and Microsoft Exchange Server) and material administration techniques.
“As the war continues, Cadet Blizzard activity poses an escalating risk to the broader European group, especially any effective attacks versus governments and IT assistance companies, which may possibly give the actor both of those tactical and strategic-level perception into Western functions and coverage bordering the conflict,” Microsoft famous.
Uncovered this write-up exciting? Follow us on Twitter and LinkedIn to read more unique information we article.
Some parts of this article are sourced from:
thehackernews.com


 LockBit Makes $91m From US Victims in Two Years
LockBit Makes $91m From US Victims in Two Years