The threat actor acknowledged as COLDRIVER has continued to engage in credential theft pursuits from entities that are of strategic passions to Russia while concurrently improving upon its detection evasion capabilities.
The Microsoft Menace Intelligence crew is monitoring underneath the cluster as Star Blizzard (previously SEABORGIUM). It’s also referred to as Blue Callisto, BlueCharlie (or TAG-53), Calisto (alternately spelled Callisto), and TA446.
The adversary “carries on to prolifically concentrate on folks and corporations concerned in global affairs, defense, and logistics assistance to Ukraine, as nicely as academia, information security providers, and other entities aligning with Russian condition passions,” Redmond stated.
Star Blizzard, joined to Russia’s Federal Security Services (FSB), has a monitor file of placing up lookalike domains that impersonate the login webpages of specific corporations. It really is regarded to be active considering the fact that at least 2017.
Approaching WEBINAR Cracking the Code: Master How Cyber Attackers Exploit Human Psychology
At any time questioned why social engineering is so productive? Dive deep into the psychology of cyber attackers in our approaching webinar.
Be a part of Now
In August 2023, Recorded Foreseeable future disclosed 94 new domains that are aspect of the menace actor’s attack infrastructure, most of which feature keyword phrases related to information and facts technology and cryptocurrency.
Microsoft stated it noticed the adversary leveraging server-facet scripts to protect against automated scanning of the actor-managed infrastructure starting off April 2023, shifting away from hCaptcha to establish targets of fascination and redirecting the browsing session to the Evilginx server.
The server-aspect JavaScript code is built to test if the browser has any plugins set up, if the web site is being accessed by an automation instrument like Selenium or PhantomJS, and transmit the results to the server in the type of a HTTP Publish request.
“Pursuing the Publish ask for, the redirector server assesses the knowledge gathered from the browser and decides whether to enable continued browser redirection,” Microsoft reported.
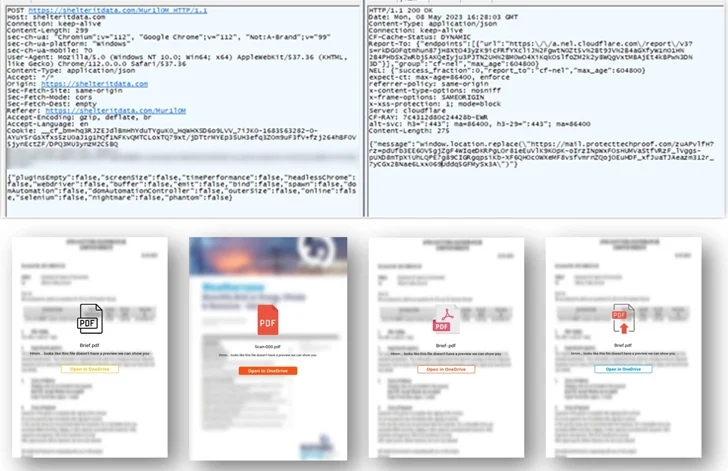
“When a great verdict is reached, the browser gets a reaction from the redirection server, redirecting to the next phase of the chain, which is both an hCaptcha for the user to address, or immediate to the Evilginx server.”
Also recently employed by Star Blizzard are email marketing and advertising providers like HubSpot and MailerLite to craft strategies that provide as the commencing level of the redirection chain that culminates at the Evilginx server hosting the credential harvesting web page.
In addition, the menace actor has been noticed making use of a area title services (DNS) provider to take care of actor-registered area infrastructure, sending password-shielded PDF lures embedding the hyperlinks to evade email security processes as well as host the documents on Proton Drive.
That is not all. In a indicator that the menace actor is actively trying to keep tabs on general public reporting into its techniques and strategies, it has now upgraded its area generation algorithm (DGA) to contain a much more randomized listing of phrases when naming them.

Despite these adjustments, “Star Blizzard actions continue to be centered on email credential theft, predominantly concentrating on cloud-based mostly email companies that host organizational and/or individual email accounts,” Microsoft reported.
“Star Blizzard stays constant in their use of pairs of devoted VPSs to host actor-managed infrastructure (redirector + Evilginx servers) used for spear-phishing routines, in which every single server generally hosts a separate actor registered area.”
U.K. Sanctions Two Members of Star Blizzard
The advancement comes as the U.K. called out Star Blizzard for “sustained unsuccessful tries to interfere in U.K. political processes” by targeting significant-profile folks and entities by means of cyber functions.
Apart from linking Star Blizzard to Centre 18, a subordinate component inside of FSB, the U.K. government sanctioned two customers of the hacking crew – Ruslan Aleksandrovich Peretyatko and Andrey Stanislavovich Korinets (aka Alexey Doguzhiev) – for their involvement in the spear-phishing strategies.
The action “resulted in unauthorized entry and exfiltration of sensitive facts, which was supposed to undermine British isles businesses and much more broadly, the British isles governing administration,” it said.
Found this posting fascinating? Follow us on Twitter and LinkedIn to browse more distinctive written content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 New Bluetooth Flaw Let Hackers Take Over Android, Linux, macOS, and iOS Devices
New Bluetooth Flaw Let Hackers Take Over Android, Linux, macOS, and iOS Devices