A by no means-right before-seen North Korean risk actor codenamed Moonstone Sleet has been attributed as at the rear of cyber assaults targeting folks and organizations in the software and info technology, education and learning, and protection industrial foundation sectors with ransomware and bespoke malware earlier related with the infamous Lazarus Group.
“Moonstone Sleet is noticed to established up faux organizations and position possibilities to have interaction with potential targets, employ trojanized versions of genuine tools, create a destructive match, and deliver a new customized ransomware,” the Microsoft Menace Intelligence workforce claimed in a new investigation.
It also characterized the menace actor as applying a blend of experimented with-and-genuine tactics utilized by other North Korean threat actors and special attack methodologies to meet up with its strategic objectives.
The adversary, hitherto tracked by Redmond under the rising cluster moniker Storm-1789, is assessed to be a condition-aligned group that originally exhibited sturdy tactical overlaps with the Lazarus Team (aka Diamond Sleet), in advance of creating its have unique identity via different infrastructure and tradecraft.
The similarities with Lazarus involve thoroughly reusing code from recognized malware these as Comebacker, which was very first observed in January 2021 in relationship with a marketing campaign focusing on security researchers operating on vulnerability research and growth.
Comebacker was place to use by the Lazarus Team as not too long ago as this February, embedding it within just seemingly innocuous Python and npm offers to establish speak to with a command-and-management (C2) server to retrieve more payloads.

To aid its assorted aims, Moonstone Sleet is also known to go after work in software program growth positions at various legitimate providers, likely in an try to create illicit profits for the sanctions-strike place or achieve covert access to businesses.
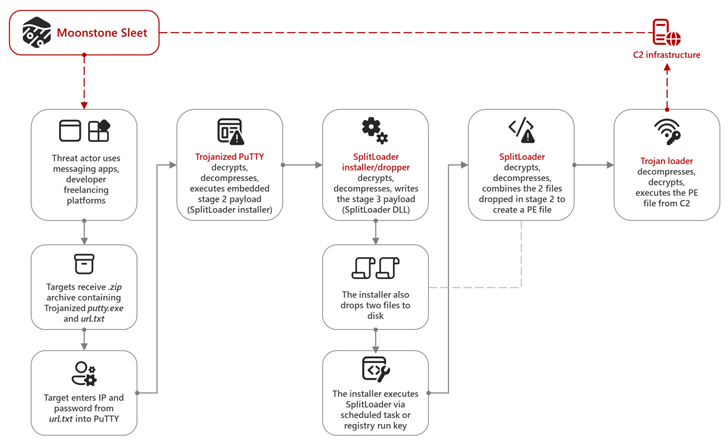
Attack chains observed in August 2023 concerned the use of a modified version of PuTTY – a tactic adopted by the Lazarus Group in late 2022 as section of Operation Dream Job – through LinkedIn and Telegram as effectively as developer freelancing platforms.
“Usually, the actor despatched targets a .ZIP archive containing two data files: a trojanized model of putty.exe and url.txt, which contained an IP deal with and a password,” Microsoft claimed. “If the provided IP and password were entered by the person into the PuTTY software, the application would decrypt an embedded payload, then load and execute it.”
The trojanized PuTTY executable is created to fall a custom made installer dubbed SplitLoader that initiates a sequence of intermediate levels in purchase to finally start a Trojan loader that’s responsible for executing a transportable executable obtained from a C2 server.
Alternate attack sequences have entailed the use of destructive npm offers that are delivered by LinkedIn or freelancing web-sites, generally masquerading as a pretend business to mail .ZIP documents invoking a malicious npm bundle below the guise of a technological abilities evaluation.
These npm offers are configured to join to an actor-controlled IP tackle and drop payloads equivalent to SplitLoader, or facilitate credential theft from the Windows Neighborhood Security Authority Subsystem Support (LSASS) system.
It is really well worth noting that the concentrating on of npm builders applying counterfeit deals has been related with a campaign earlier documented by Palo Alto Networks Device 42 below the name Contagious Job interview (aka DEV#POPPER). Microsoft is tracking the action underneath the identify Storm-1877.
Rogue npm deals have also been a malware delivery vector for another North Korea-linked team codenamed Jade Sleet (aka TraderTraitor and UNC4899), which has been implicated in the JumpCloud hack very last year.
Other assaults detected by Microsoft because February 2024 have utilized a malicious tank video game called DeTankWar (aka DeFiTankWar, DeTankZone, and TankWarsZone) that is dispersed to targets by using email or messaging platforms, when lending a layer of legitimacy by environment up phony websites and accounts on X (formerly Twitter).
“Moonstone Sleet commonly methods its targets by messaging platforms or by email, presenting itself as a video game developer looking for expense or developer help and either masquerading as a respectable blockchain corporation or making use of phony companies,” Microsoft researchers mentioned.
“Moonstone Sleet used a phony enterprise termed C.C. Waterfall to call targets. The email offered the video game as a blockchain-relevant venture and available the focus on the possibility to collaborate, with a backlink to obtain the match provided in the human body of the message.”
The purported activity (“delfi-tank-unity.exe”) comes fitted with a malware loader referred to as YouieLoad, which is able of loading subsequent-phase payloads in memory and building malicious companies for network and person discovery and browser data assortment.

One more non-existent enterprise – entire with a personalized domain, fake worker personas, and social media accounts – produced by Moonstone Sleet for its social engineering campaigns is StarGlow Ventures, which masqueraded as a genuine software advancement corporation to arrive at out to future targets for collaboration on initiatives linked to web applications, cell apps, blockchain, and AI.
Even though the stop of this campaign, which took area from January to April 2024, is unclear, the truth that the email messages came embedded with a monitoring pixel raises the likelihood that it may possibly have been utilized as part of a trust-creating physical exercise and ascertain which of the recipients engaged with the e-mails for long term profits technology opportunities.
The most up-to-date instrument in the adversary’s arsenal is a custom ransomware variant termed FakePenny that it has been observed deployed towards an unnamed defense technology business in April 2024 in trade for a $6.6 million ransom in Bitcoin.
The use of ransomware is an additional tactic pulled straight out of Andariel’s (aka Onyx Sleet) playbook, a sub-group working within the Lazarus umbrella recognized for ransomware households like H0lyGh0st and Maui.
In addition to adopting required security measures to protect from assaults by the menace actor, Redmond is urging application corporations to be on the lookout for offer chain attacks, supplied North Korean risk actors’ propensity for poisoning the software package source chain to conduct popular destructive functions.
“Moonstone Sleet’s diverse established of strategies is notable not only because of their efficiency, but due to the fact of how they have advanced from individuals of quite a few other North Korean threat actors above several many years of activity to satisfy North Korean cyber objectives,” the organization mentioned.
The disclosure will come as South Korea accused its northern counterpart, notably the Lazarus Team, of thieving 1,014 gigabytes of data and documents such as names, resident registration figures, and money data from a court docket network from January 7, 2021, to February 9, 2023, Korea JoongAng Every day documented before this month.
Found this posting exciting? Stick to us on Twitter and LinkedIn to study much more unique content material we write-up.
Some parts of this article are sourced from:
thehackernews.com


 BreachForums Returns Just Weeks After FBI Seizure – Honeypot or Blunder?
BreachForums Returns Just Weeks After FBI Seizure – Honeypot or Blunder?