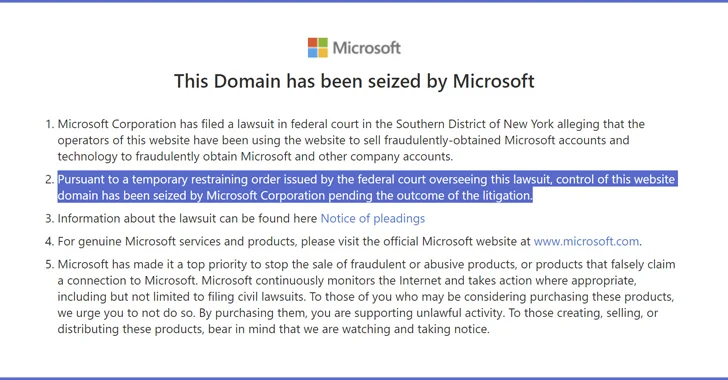
Microsoft on Wednesday claimed it attained a courtroom purchase to seize infrastructure set up by a team known as Storm-1152 that peddled about 750 million fraudulent Microsoft accounts and instruments by means of a network of bogus web-sites and social media internet pages to other criminal actors, netting them thousands and thousands of bucks in illicit income.
“Fraudulent on line accounts act as the gateway to a host of cybercrime, which include mass phishing, id theft and fraud, and distributed denial-of-provider (DDoS) attacks,” Amy Hogan-Burney, the firm’s affiliate basic counsel for cybersecurity plan and safety, reported.
These cybercrime-as-a-assistance (CaaS) offerings, for each Redmond, are built to get about id verification software program across several technology platforms and help minimize the initiatives needed to carry out destructive actions on the web, together with phishing, spamming, ransomware, and fraud, effectively decreasing the obstacles to entry for attackers.
Forthcoming WEBINAR Beat AI-Driven Threats with Zero Believe in – Webinar for Security Experts
Common security measures would not minimize it in present-day environment. It can be time for Zero Rely on Security. Protected your facts like never in advance of.
Join Now
Many danger actors, counting Octo Tempest (aka Scattered Spider), are mentioned to have applied Storm-1152’s accounts to pull off ransomware, knowledge theft, and extortion schemes. Two other monetarily inspired threat actors that have ordered fraudulent accounts from Storm-1152 to scale their own attacks are Storm-0252 and Storm-0455.
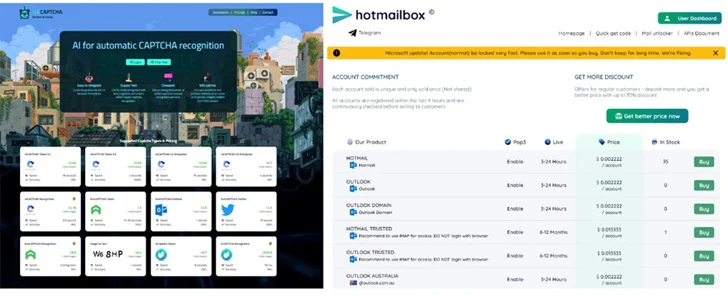
The team, active since at minimum 2021, has been attributed to the adhering to internet websites and internet pages –
- Hotmailbox.me for selling fraudulent Microsoft Outlook accounts
- 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA for offering equipment mastering-based mostly CAPTCHA fixing expert services to bypass identity verification
- Social media webpages for promotion the expert services
Microsoft, which collaborated with Arkose Labs on the initiative, explained it was equipped to discover a few people today dependent in Vietnam who had been instrumental in building and retaining the infrastructure: Duong Dinh Tu, Linh Van Nguyễn (also recognized as Nguyễn Van Linh), and Tai Van Nguyen.

“These persons operated and wrote the code for the illicit internet sites, published in depth action-by-stage directions on how to use their solutions by using online video tutorials and supplied chat expert services to guide those people employing their fraudulent solutions,” Hogan-Burney noted.
“Not only did the enterprise promote its technology like any other kind of software organization – with pricing structures based upon a customer’s requires – but it also would perform phony account registration assaults, sell individuals faux accounts to other cybercriminals, and then income out with crypto currency,” Kevin Gosschalk and Patrice Boffa stated.
Found this report attention-grabbing? Follow us on Twitter and LinkedIn to study more exclusive written content we submit.
Some parts of this article are sourced from:
thehackernews.com

 BazaCall Phishing Scammers Now Leveraging Google Forms for Deception
BazaCall Phishing Scammers Now Leveraging Google Forms for Deception