Microsoft on Wednesday disclosed that it identified a established of remarkably focused social engineering attacks mounted by a Russian nation-point out risk actor utilizing credential theft phishing lures despatched as Microsoft Groups chats.
The tech big attributed the assaults to a team it tracks as Midnight Blizzard (beforehand Nobelium). It’s also known as APT29, BlueBravo, Cozy Bear, Iron Hemlock, and The Dukes.
“In this most up-to-date action, the menace actor works by using formerly compromised Microsoft 365 tenants owned by modest corporations to make new domains that look as technical help entities,” the enterprise claimed.
“Utilizing these domains from compromised tenants, Midnight Blizzard leverages Teams messages to ship lures that try to steal qualifications from a specific organization by partaking a user and eliciting approval of multi-issue authentication (MFA) prompts.”
Microsoft reported the campaign, noticed since at minimum late May possibly 2023, impacted considerably less than 40 organizations globally spanning federal government, non-govt businesses (NGOs), IT companies, technology, discrete production, and media sectors.

The menace actor has been observed to employ token theft strategies for first entry into qualified environments, along with other strategies this kind of as authentication spear-phishing, password spray, and brute-power attacks.
A further known hallmark is its exploitation of on-premises environments to laterally shift to the cloud as perfectly as the abuse of provider providers’ have faith in chain to gain obtain to downstream shoppers, as observed in the SolarWinds hack of 2020.
In the new spherical of attacks connected to Midnight Blizzard, a new onmicrosoft.com subdomain is additional to a tenant formerly compromised in attacks, followed by producing a new user with that subdomain to initiate a Groups chat ask for with opportunity targets by masquerading as a complex aid man or woman or Microsoft’s Identity Security workforce.
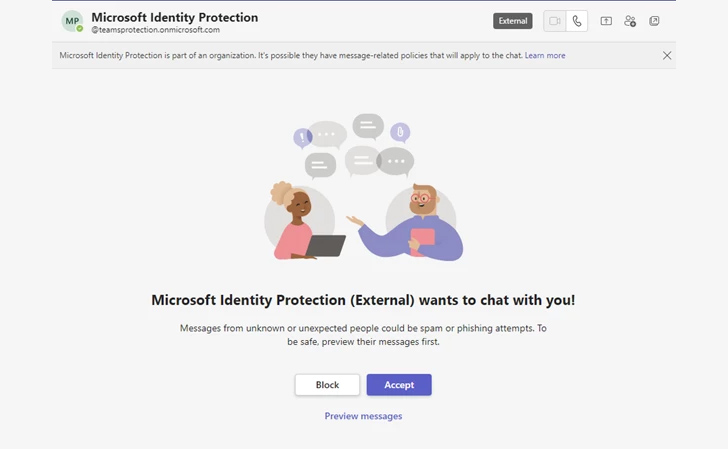
“If the goal user accepts the concept ask for, the user then receives a Microsoft Teams message from the attacker making an attempt to influence them to enter a code into the Microsoft Authenticator app on their cell machine,” Microsoft stated.
Must the target follow by with the instructions, the menace actor is granted a token to authenticate as the qualified consumer, thus letting for account takeover and follow-on put up-compromise activity.
“In some instances, the actor tries to insert a system to the business as a managed unit via Microsoft Entra ID (previously Azure Lively Listing), very likely an endeavor to circumvent conditional entry guidelines configured to restrict access to specific assets to managed devices only,” Microsoft cautioned.

The results appear times just after the threat actor was attributed to phishing attacks concentrating on diplomatic entities all over Eastern Europe with the goal of offering a new backdoor known as GraphicalProton.
They also abide by the discovery of a number of new Azure Ad (AAD) Link attack vectors that could allow for destructive cyber actors to develop an undetectable backdoor by thieving cryptographic hashes of passwords by injecting destructive code into a hash syncing approach and intercepting qualifications by signifies of an adversary-in-the-middle (AitM) attack.
“For example, attackers can leverage the extraction of NT hashes to assure they get each future password alter in the area,” Sygnia stated in a statement shared with The Hacker Information.
“Danger actors can also use [Active Directory Certificate Services] to attain AAD Connector passwords, as properly as provide as a man-in-the-center and start assaults towards SSL-encrypted channels in the network by exploiting misconfigurations in certification templates that have server authentication.”
Located this short article intriguing? Abide by us on Twitter and LinkedIn to read additional exceptional content material we post.
Some parts of this article are sourced from:
thehackernews.com


 Researchers Discover Bypass for Recently Patched Critical Ivanti EPMM Vulnerability
Researchers Discover Bypass for Recently Patched Critical Ivanti EPMM Vulnerability