A now-patched security flaw in the Microsoft Edge web browser could have been abused to put in arbitrary extensions on users’ systems and have out destructive actions.
“This flaw could have authorized an attacker to exploit a private API, in the beginning supposed for promoting reasons, to covertly set up supplemental browser extensions with wide permissions with no the user’s knowledge,” Guardio Labs security researcher Oleg Zaytsev reported in a new report shared with The Hacker News.
Tracked as CVE-2024-21388 (CVSS score: 6.5), it was addressed by Microsoft in Edge steady variation 121..2277.83 launched on January 25, 2024, subsequent responsible disclosure in November 2023. The Windows maker credited both of those Zaytsev and Jun Kokatsu for reporting the issue.
“An attacker who correctly exploited this vulnerability could acquire the privileges essential to put in an extension,” Microsoft claimed in an advisory for the flaw, adding it “could guide to a browser sandbox escape.”

Describing it as a privilege escalation flaw, the tech giant also emphasized that a thriving exploitation of the bug requires an attacker to “choose supplemental steps prior to exploitation to prepare the target setting.”
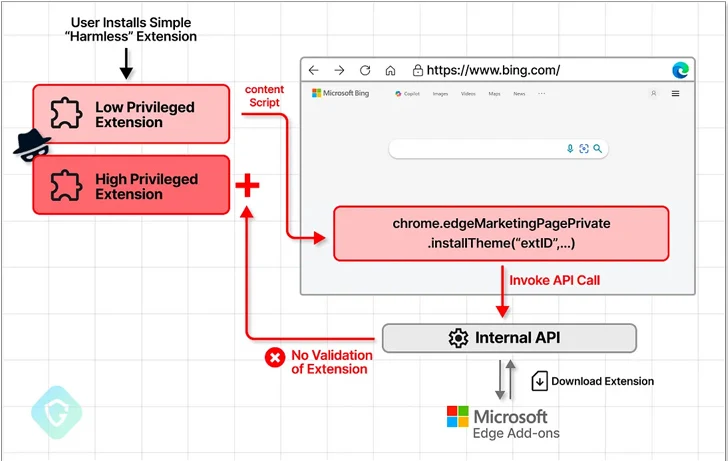
In accordance to Guardio’s results, CVE-2024-21388 will allow a lousy actor with the potential to operate JavaScript on bing[.]com or microsoft[.]com pages to put in any extensions from the Edge Increase-ons retailer sans demanding user’s consent or conversation.
This is designed doable by the reality that the browser will come with privileged obtain to specified non-public APIs that make it attainable to install an add-on as very long as it’s from the vendor’s possess extension market.
Just one these types of API in the Chromium-based mostly Edge browser is edgeMarketingPagePrivate, which is obtainable from a set of allowlisted web sites that belong to Microsoft, together with bing[.]com, microsoft[.]com, microsoftedgewelcome.microsoft[.]com, and microsoftedgetips.microsoft[.]com, between others.
The API also packs in a method called installTheme() that, as the identify indicates, is intended to install a topic from the Edge Add-ons retail store by passing a one of a kind concept identifier (“themeId”) and its manifest file as input.
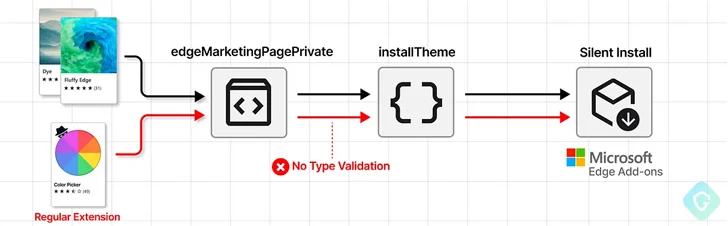
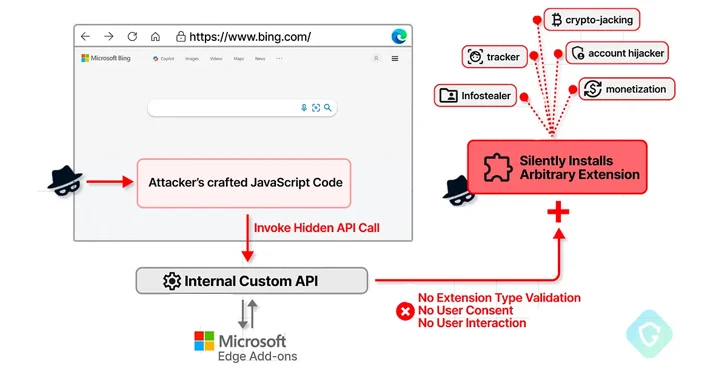
The bug discovered by Guardio is fundamentally a situation of insufficient validation, therefore enabling an attacker to supply any extension identifier from the storefront (as opposed to the themeId) and get it stealthily set up.
“As an included bonus, as this extension installation is not accomplished very in the fashion it was originally built for, there will be no need for any conversation or consent from the consumer,” Zaytsev defined.

In a hypothetical attack circumstance leveraging CVE-2024-21388, a threat actor could publish a seemingly harmless extension to the insert-ons keep and use it to inject a piece of destructive JavaScript code into bing[.]com – or any of the websites that are permitted to accessibility the API – and set up an arbitrary extension of their choice by invoking the API applying the extension identifier.
Place in a different way, executing the specially crafted extension on the Edge browser and heading to bing[.]com will automatically set up the targeted extension with no the victim’s authorization.
Guardio explained to The Hacker News that while there is no evidence of this bug becoming exploited in the wild, it highlights the require for balancing person convenience and security, and how browser customizations can inadvertently defeat security mechanisms and introduce several new attack vectors.
“It is fairly easy for attackers to trick buyers into putting in an extension that seems harmless, not noticing it serves as the initial phase in a a lot more intricate attack,” Zaytsev reported. “This vulnerability could be exploited to facilitate the installation of extra extensions, possibly for financial obtain.”
Uncovered this report interesting? Abide by us on Twitter and LinkedIn to go through more distinctive material we put up.
Some parts of this article are sourced from:
thehackernews.com

 SASE Solutions Fall Short Without Enterprise Browser Extensions, New Report Reveals
SASE Solutions Fall Short Without Enterprise Browser Extensions, New Report Reveals