Microsoft on Thursday explained it truly is at the time yet again disabling the ms-appinstaller protocol handler by default subsequent its abuse by numerous threat actors to distribute malware.
“The observed threat actor exercise abuses the present-day implementation of the ms-appinstaller protocol handler as an obtain vector for malware that might direct to ransomware distribution,” the Microsoft Threat Intelligence crew reported.
It additional noted that a number of cybercriminals are supplying a malware kit for sale as a provider that leverages the MSIX file structure and ms-appinstaller protocol handler. The improvements have absent into impact in Application Installer model 1.21.3421. or larger.
The attacks get the sort of signed destructive MSIX software packages that are distributed by using Microsoft Groups or malicious advertisements for reputable common application on search engines like Google.
Upcoming WEBINAR From Person to ADMIN: Discover How Hackers Obtain Comprehensive Regulate
Explore the magic formula tactics hackers use to grow to be admins, how to detect and block it before it can be too late. Sign up for our webinar today.
Join Now
At the very least four distinct fiscally inspired hacking teams have been observed having advantage of the App Installer services considering that mid-November 2023, using it as an entry point for follow-on human-operated ransomware exercise –
- Storm-0569, an first obtain broker which propagates BATLOADER via look for motor optimization (Web optimization) poisoning with websites spoofing Zoom, Tableau, TeamViewer, and AnyDesk, and makes use of the malware to deliver Cobalt Strike and handoff the accessibility to Storm-0506 for Black Basta ransomware deployment.
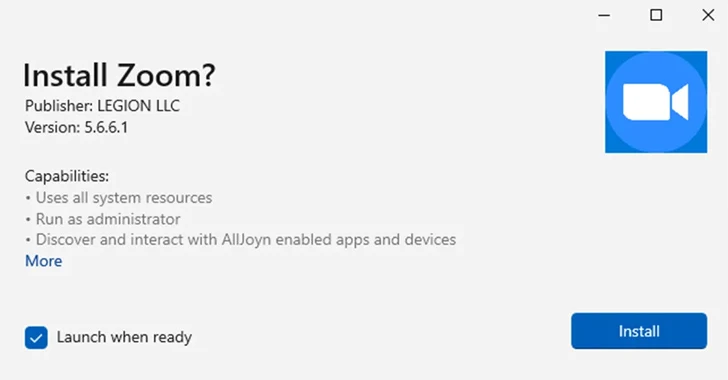
- Storm-1113, an first obtain broker that uses bogus MSIX installers masquerading as Zoom to distribute EugenLoader (aka FakeBat), which acts as a conduit for a wide range of stealer malware and distant access trojans.
- Sangria Tempest (aka Carbon Spider and FIN7), which uses Storm-1113’s EugenLoader to fall Carbanak that, in turn, provides an implant called Gracewire. Alternatively, the group has relied on Google adverts to lure people into downloading destructive MSIX application offers from rogue landing pages to distribute POWERTRASH, which is then utilised to load NetSupport RAT and Gracewire.
- Storm-1674, an original accessibility broker that sends faux landing web pages masquerading as Microsoft OneDrive and SharePoint via Groups messages using the TeamsPhisher instrument, urging recipients to open PDF data files that, when clicked, prompts them to update their Adobe Acrobat Reader to download a destructive MSIX installer that is made up of SectopRAT or DarkGate payloads.
Microsoft explained Storm-1113 as an entity that also dabbles in “as-a-support,” providing malicious installers and landing webpage frameworks mimicking effectively-known computer software to other risk actors this sort of as Sangria Tempest and Storm-1674.

In October 2023, Elastic Security Labs thorough yet another marketing campaign in which spurious MSIX Windows app bundle files for Google Chrome, Microsoft Edge, Courageous, Grammarly, and Cisco Webex were being applied to distribute a malware loader dubbed GHOSTPULSE.
This is not the initially time Microsoft has disabled the MSIX ms-appinstaller protocol handler in Windows. In February 2022, the tech big took the very same move to prevent threat actors from weaponizing it to provide Emotet, TrickBot, and Bazaloader.
“Risk actors have likely decided on the ms-appinstaller protocol handler vector for the reason that it can bypass mechanisms created to help preserve people safe from malware, such as Microsoft Defender SmartScreen and built-in browser warnings for downloads of executable file formats,” Microsoft mentioned.
Discovered this short article appealing? Stick to us on Twitter and LinkedIn to read through much more distinctive material we article.
Some parts of this article are sourced from:
thehackernews.com

 Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service
Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service